Goldilock robust digital security vault
Preamble
The era of digital money is here, it is a reality. That means that just as in its early days we were forced to learn to use the Internet to be aligned with all that technological movement that was triggered by it, in the same way, we have to quickly adopt this new alternative money for access to goods and services and become familiar with the elements that revolve around them.
The appearance of Bitcoin meant a world of opportunities for visionaries and has revolutionized the system of traditional commercial transactions due to its unique characteristics such as:
-
Decentralized. That is, it is not controlled by any government, individual or company. Its validity or credibility comes from the community that uses it.
-
It has no border limits, like a Fiat currency (Currencies issued by a central bank). Because of this, it allows transactions from anywhere in the world, without time conditions.
-
Protected by a complex mathematical or cryptographic system.
-
It is interchangeable by other digital currencies, Fiat currency or goods and services.
-
It is distributed. There is no central node where operations are processed, but a network of interconnected nodes around the world.
-
It is possible to transfer any amount of coins, larg or small.
-
It is not unlimited. Each year a certain amount are issued, which doubles the following year. This will go on until the year 2030 when the maximum amount of 21 million Bitcoins is reached . Once that figure is reached, no new bitcoins will be created. In this way, the inflationary phenomenon is prevented that would have been caused by the arbitrary growth of the digital currency.
-
It is based on a cryptographic system: Blockchain. This technology works like a database where it is meticulously recorded as an accounting book, to digital asset transactions with no possibility of being manipulated or deleted. This means that you do not need a third party, such as a bank, to validate operations. These transactions are visible to the public, although the identity of those who carry it out remain anonymous (However, some interfaces such as the Internet Archive can be known).
The Bitcoint marked the route for the emergence of other cryptocurrencies with equal or similar attributes. Today there are dozens of digital currencies that accompany new projects operating from blockchain technology.
At https://coinmarketcap.com/ we can see a top 100 top.
Each day the number of people making use of this technology increases, creating the need, among others, to design platforms with interfaces to the blockchain more friendly, in order to reduce the obstacles to its adoption. But also, unfortunately, this expansion has caught the attention of the bands of computer criminals, who work stealthily looking for weak points in the different platforms to subtract the funds from the accounts, causing millions in losses.
According to the security firm Carbon Black, just in the first half of this year the hackers managed to seize 1.1 billion cryptocurrencies using a criminal strategy known as " Phishing "
It is a systematic and daily attack. There is no truce.
The page https://checkphish.ai/trends shows the daily tendencies of this scourge that keeps the community defensive.
This has forced developers do draw more complex security strategies that guarantee the safeguarding of digital assets.
Goldilock It takes seriously this concern and need for protection required by consumers or investors about their funds.
What is Goldilock ?

It is a system that offers investors , consumers or companies the storage, management , custody and security of their digital assets, cryptocurrencies and master keys using the combination of technologies such as:
-
Biometrics. This technology implies the human recognition of characteristics that are proper , particular or unrepeatable such as fingerprint, facial recognition, iris, retina, geometry of the palm of the hand , voice orrubric.
-
Authentication in two phases. This double authentication factor will validate that who executes the combination of steps correctly will have access to the data. For example, currently Google synchronized with Authy add an additional layer of security to the account. When you enter your password and password, Google Authenticator connects to Authy, which automatically generates a Token or code that is updated every 15 seconds. Thistoken is entered in the corresponding box to unlock access to the account.
-
Recognition of devices. Goldilock will use advanced technology that will be able to iden tify the teams that connect to the blockchain evaluating attributes such as time zone, screen resolution, keyboard designs and even the micro differences that arise in the manufacturing process that works as a brand that distinguishes it from another team with the same characteristics. Access will only be allowed if these attributes match the previously registered attributes.
-
Vaults. Dedicated data centers in case companies need direct control over the server that stores their digital assets.
-
Multi-signature security. This system requires the permission of another user s or more before executing fund transactions. Usually three private keys are associated to the account. This reduces the risk of unauthorized withdrawals.
-
Secure dashboards and live reporting on access and usage. The data is susceptible to being stolen if precautions or necessary measures are not taken. Goldilock will allow the owner of the account to securely access a visual report of their data, but keeping the funds in reserve using an additional layer of security.
Goldilock follows NEO's digital identity principle. Within the network, there will be the possibility of knowing those who intervene in a transaction. Goldilock be governed by the applicable commercial rules and laws that apply. This guarantees transparency and fair transactions among the participants.
Goldilock in the Blockchain NEO

NEO is a development platform blockchain and is backed the Chinese government. Their vision is to achieve an intelligent economy. It is a platform that supports intelligent cough and safeguards against digital assets through a security layer that uses digital identity.
In his White paper it can be read:
In the NEO block chain, users can register, market and distribute multiple types of assets. Testing the connection between digital and physical assets is possible through digital identity. The goods registered through a valid digital identity are protected by law.
The spinal cord of NEO's smart economy is represented by:
-
The digital assets: all digitized assets will be . These assets can be music, documents, photographs, films or any element in digital format that their owners need to protect.
-
Digital identity: this point differentiates NEO from other blockchains . The transactions will not be anonymous. It will be possible to know who carried out operations from side to side, making use of facial recognition technologies, voice, fingerprints or other unique characteristics of each human being.
-
Smart Contrations: once agreed the conditions that will govern the contract, this will be registered in the blockchain . Neither party may interrupt its execution. The program will perform the instructionsand run without the intervention of third parties under the terms provided. The process will be absolutely automated.
The possibilities are endless, such as a traditional contract, only that Neocontract will continue to be executed and effective even if one of the parties dies (assuming it has not been established as a condition to cancel the contract ).
NEO makes use of two currencies:
-
NEO. With a limit of 100 million. Because does not contemplate mining, transactions could be ceased p r or at a rate of 10 thousand times per second.
Currently, cryptocurrency is among the hundred most valued digital currencies in the market. https://coinmarketcap.com/
-
GAS (ANC). It's the token fuel with which commissions are paid within the network.
Goldilock will have the following currencies as options within its platform: NEO , BTC, ETH , USD and the Token Lock.
Air GAP Security System

Goldilock, will not only make use of proven technologies, but has developed pending securitysystem patented before the United States Patent and Trademark Office, named "Air GAP" combines do with (PSTN) or public network analog technology.
This term has a date of more than 30 years. This security measure was put into practice by the US military to protect, for example, confidential information whose disclosure would endanger national security. This information was stored in airtight warehouses with restricted access. The transfer from one system to another it was done following a strict protocol by qualified people to do the work.
Currently, this methodology is used to refer to servers that store critical data, which must be kept away from the possibility of theft by hackers. These servers rest in closed spaces, disconnected from other devices andchannels electromagnetic, acoustic, term or optical.
This physical separation between servers and users is what is known as Air GAP. That is, it is not possible to access these servers from any network system that links to the Internet. Isolation is the key. These can only be accessed in a physical way by means of external storage devices jealously controlled as USB or CDs.
This high security environment is using Goldilock to protect cryptographic keys and digital assets of the user s your chain block.
Goldilock is a platform designed thinking about the receipt of sensitive information generated by systems such as governmental, military, financial, industrial, medical, etc. entities , which it is necessary to keep away from inadequate hands that could generate damages.
As does 30 to us access to this s enclosures will include security protocols authorized personnel.
This pending patented security system will use dial-up telephone networks for identity verification through PIN commands or voice recognition.
Cold and Hot storage
Goldilock combines the strengths of a cold and hot storage according to its three premises.
- Possibility of sporadic and brief data access.
- Storage of sensitive data isolated and inaccessible from an Internet network. further of backups.
- Quick access to data
- The cryptoactive storage server is without Internet connection, reducing the possibility of being attacked by hackers.
- Data stored in cold, escape to computer viruses .
- They are ideal for soul to dine large volumes of funds. They resemble savings accounts.
- Only the time necessary to access the information is active. Then they disconnect.
- Private keys are generated and signed off line . The user is the one who controls your private key.
- They are easily accessible from the web.
- They are useful for daily operations and small fund transactions.
Cold storage
Hot storage
Token Lock
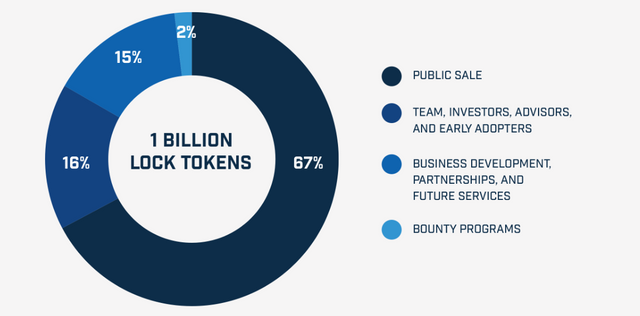
Goldilock will distribute only a total of 1 billion tokens, and just like the NEO cryptocurrencies, these can not be mined. The sale of these tokens will be used to finance the operations and developments of the platform.
Weighing
Although it has been talking about virtual currencies since the appearance of Bitcoin almost a decade ago. The bulk of the population has paid little attention to the potential possibilities offered by this technology on which these cryptocurrencies are based.
Ignorance is still widespread, Fiat coins are still considered as the only sources for exchanges of goods and services for the vast majority. And the traditional banks, the only reliable ones to safeguard the assets.
Despite this, the movement around this new paradigm of commercial transactions with decentralized virtual currencies continues to grow, adjusting and strengthening.
Although Bitcoin continues to lead, after it have emerged dozens of new cryptocurrencies that are listed on the stock market. All representing a project that can cover demands that the traditional market is not capable of.
Probably, the resistance that blocks the massive adoption once and for all of this technology, is due, in the first place, to ignorance about technological issues that can be a bit confusing at first and the security breaches that remain a neuralgic issue in digitized networks, which are exploited by groups of cyber criminals creating mistrust in the majority.
There are groups of experts that study ways to counteract these attacks and, have been closing the possibilities of action of these cybernetic pirates.
Goldilock is aware of this problem and is aware of the concern of consumers and companies that claim for safer and more reliable systems, that provide the peace of mind that their digital assets, sensitive data or funds are out of reach of scrupulous hands.
Goldilock will make use of NEO technology to achieve integration between the systems of companies or organizations such as universities, banking systems, oil systems, steel systems, hospital systems, government systems, etc. For example, the Neocontract intelligent contract system supports applications developed in conventional languages (such as C #, Java, Kotlin, C, C ++, GO, Python, JavaScript). It will not be necessary to incur training expenses of the group of developers of the company for the Goldilock adaptation.
Goldilock continues to work on strengthening its Security Suite, with the commitment to create a robust and reliable ecosystem.
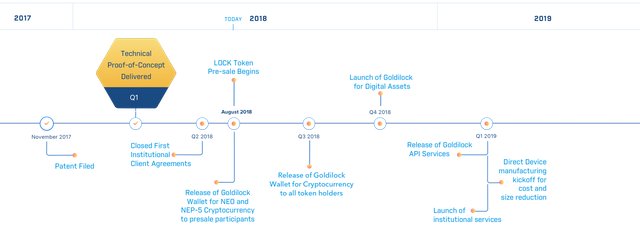
Roadmap

Team

Partners

Resources
Website WhitePaper Telegram
DiscordLinkedin Facebook
TwitterReddit Github
Visit 810 STEEM ~ Sponsored Writing Contest: Goldilock
Sources and imagen:
Neo White Paper
Goldilock White Paper
Goldilock Tokenomic
goldilocktwitter
goldilock2018
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
As a follower of @followforupvotes this post has been randomly selected and upvoted! Enjoy your upvote and have a great day!