The New Era of Hacking and Cyber Attacks
“Hello, I was wondering if you can take a look at a website I am trying to get to, it’s for a big customer thing I am working on for Monday… And I can’t seem to get to the website from my computer.”
“Sure, what is the website you are trying to get to?”
“Thanks I appreciate the help, it could be a really stupid thing, I really suck at computers… The website is www.survey-pro.com”
“Yeah I got it, I got a prompt and clicked open”
“Oh right, now it seems to work for me as well, thank you very much!”
Above, is a recorded phone call from a hacker pretending to be an employee of a company. Nowadays, calling someone pretending to be naïve is all it takes for a hacker to gain access to a company’s network, “unfortunately, this is the case for most companies”, states Chris Snyder, a senior security analyst at the NSA.
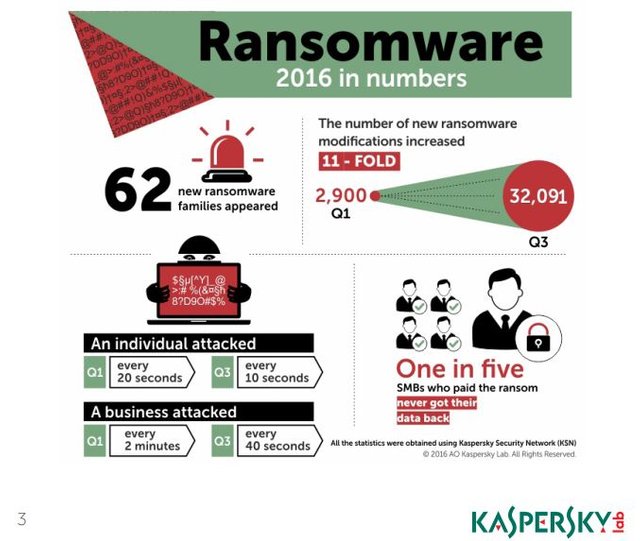
However, this is just one example out of many. Hackers are hacking businesses every single day, “a company is hit with a ransomware every 40 seconds”, states Kaspersky, arguably the most influential anti-virus company in the world. As the technological world advances, it has never been so easy to steal information, “there are only two types of companies: those that have been hacked, and those that will be”, states the FBI director Robert Mueller in 2012.
“Sometimes, our job feels like it’s too easy”, said Jeremiah Salamantes, the social engineer of a Redteam security, showing how it easy it was for him to gain full control of a big company that was thought to be secure.
Nonetheless, this isn’t just a problem affecting businesses and companies, but just about everything we depend on. The NSA, the world’s most important security agency, said it’s a matter of “when, not if” there is a cyber-attack. The problem gets even more serious with breaches on a national scale. In 2016, hackers fully compromised the US power grid, and “It was surprisingly easy”, explains Ryan Manship, Redteam Security’s practice director.
Not only are these attacks concerning in terms of what hackers are able to do with them, but they also cause major financial damage. This can be seen with the arrival of ransomwares, for example. Ransomwares are programs that encrypt data on your computer and charge you money to get it back. In 2017 alone, they have caused over 5 billion dollars of damage spread over 114 countries. WannaCry, the biggest ransomware yet, shows how severe this problem really is, having caused over 1 billion dollars of damage in just 4 days.
Furthermore, WannaCry has targeted big corporations, including public facilities such as hospitals. This has caused the National Health Service centers to close, X-ray sessions to be cancelled and surgery to be postponed, “WannaCry had a large impact on UK healthcare institutes, reportedly causing some hospitals to prioritise or turn away patients – thereby putting human lives at risk” says Corey Nachreiner, chief technology officer at WatchGuard Technologies.
Hackers benefit and profit from large corporations, but from normal individuals as well, just like your average online user that browses social media from time to time. In 2016 for example, there have been over 600.000 individual PC’s hacked. The reason behind all the attacks, are not due to devices being insecure, but rather the people not securing themselves, “Human error accounts for an estimated 95% of security incidents”, states Avast, one of the most famous internet security applications.
This can be seen with the rise of phishing attacks in the last few years, for example. Just like the word ‘phishing’ suggests, a phishing attack is a way for a hacker to lure and ‘catch’ its victim with a fake website or email, that will ultimately steal the victim’s credentials. To illustrate, in 2016, 76% of organizations reported being victim of a phishing attack. Moreover, phishing attacks are responsible for 55% of all online threats.
The reason why phishing attacks are so popular and effective is because they exploit the computer’s biggest flaw, the human, “people are the weakest link in security, and that’s especially true when it comes to phishing”, explains Avast. This is because tricking the human behind the machine is much easier than tricking the machine itself. In fact, “50 percent of the 1,700 test subjects clicked on links from strangers in emails and Facebook messages, even though 78 percent of them claimed to be aware of the risks”, shows a study conducted by Avast.
It doesn’t always come down to a single person however, several companies have been found not taking proper measures to protect their user’s privacy. This was made evident for example, when T-Mobile was found storing passwords as plaintext, making over 76 million people vulnerable to hackers. This doesn’t regard just some companies, but the whole technology industry itself, having seen over 1.75 billion credential spills in 2016 alone.
In fact, once your data has been stolen, it is mostly used for fraud and identity theft. With the access to Tor, hackers can easily sell your data on the dark web, for as low as 5 dollars. The dark web is already known as a place for hackers to sell sensitive data and items such as account login details, drugs, weapons… which are usually illegally obtained.
Recently, in 2017, a database with data belonging to 1.4 billion users has been published on the dark web. However, the greatest concern is that, “many people often tend to use the same passwords for multiple logins such as email, social media and banking transactions’ explains Julio Casal, CTO of identity threat intelligence firm.
This all sounds very alarming, but there are several precautions that can be taken to better secure yourself online. “Create complex passwords, click smart, and keep your guard up”, emphasizes Gary Davis, Chief Consumer Security Evangelist.
However, as an internet user, you must remember that your data will never be 100% secure. That is because the moment you access the internet, or are using an IoT device you are putting yourself at risk. “Whenever an appliance is described as being smart, it’s vulnerable”, explains Mikko Hyppönen, Chief Research Officer at F-Secure. As long as we use the internet, we can try to protect ourselves as much as we can, but we must face the reality that our data will never be fully secure.
Congratulations @fedecuci! You received a personal award!
Click here to view your Board
Congratulations @fedecuci! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!