Wireless Local Area Network (WLAN): A technology for the masses.
I was walking to the closest bus stop around me last weekend and this set of people approached me and said to me, "sir we would like to ask you one IT related question and we would like to video you as you answer the question". I said to them, that would be fantastic but you'll do me a favor, I would also like to ask you one question in return and keep the recording going as you answer the question.

[Image credit: Pixabay. CC0 Creative Commons
I said this because I have watched such video clips on YouTube where they'll ask unsuspecting passerby questions like "what is the difference between genotype and phenotype, or ask them to spell gmelina and when they fail these questions, the video is edited and some funny clips and emojis are attached to the clip to make fun of them.
The man with the microphone asked me, "what is the full meaning of Wi-Fi?". I smiled and said, "Wireless Fidelity", and I intentionally asked, hope I got it? The guy questioning said yeah, sure! I said fine, I would like to know the full meaning of SSID since it is often used in conjunction with Wi-Fi. The atmosphere changed and they knew right there that they picked the wrong guy, lol.
Local Area Network has been discussed extensively in this community by me and other authors and I would like to add to our knowledge, the underlying technology that powers one of the most popular internet technologies, the WLAN. WLAN is loved by all because of the comfort it brings. These days, we just walk into our offices, power the PC and before it boots to the desktop, the news feed has already refreshed, the latest mail has already dropped and our uncompleted torrent download has resumed, same with our mobile phone without touching a single cable and without being careful so as not to trip any cable.
I know someone is shouting WiFi, but hey!, we're going beyond that here, in fact, this could be the last time I will write that acronym in this very post. This post is filled with acronyms, I just couldn't help it cause there's no way one can discuss an IEEE regulated technology without dealing with acronyms.
The WLAN Topology
Just like when I was discussing the 802.3 (LAN), I started by stating and explaining the different types of topologies we find in our LAN like the bus, star, ring and so on, we would still take the same approach. Broadly, there are two types of topology adopted for the WLAN, we address these two topologies as modes and they are:
- Ad hoc Mode and
- Infrastructure Mode
The connectivity within a circuit is known as Personal Area Network (PAN), when we connect two or more PANs and are able to share information between them, we call such setup a LAN. When such connectivity is done without leveraging any cable, we call such setup a WLAN.
)
In ad hoc setup, devices communicate directly with each other without the need for a third party device or system. Image credit Source, license .
That being said, did you know that you can share files across many PCs just by using the wireless network card embedded in almost all PCs? Setting up the same connection with our mobile phones have been simplified, commercialized and some of them given the brand name, Xender, Flashare, etc. All these setups are known as the ad hoc wireless local area network.
The term "ad hoc" is of Latin origin and is used to refer to a set of resources or solution which is used carrying out a specific task. An ad hoc wireless network is a network which is set up between nodes without the need for an intermediate device or resource(s). This can also be called a peer-to-peer wireless network. When we power our devices say, smartphone or PC, these devices have wireless cards which can transmit and receive network signals probably with the help of very tiny antenna(s).
The maximum distance away from our gadget at which signals can be received and transmitted to the gadget is known as the Basic Service Set (BSS). For wireless communication to occur in ad-hoc mode, there must be an intersection of BSS for each communicating device. The collection of intersected basic service sets in which communication is successfully occurring between devices independent of external resources (e.g, an access point) is known as the Independent Basic Service Set (IBSS).
Ad hoc network has lots of limitations apart from the physical issue of having the communicating devices confined in a close proximity, it is impossible to monitor network traffic in ad hoc mode since all the connected devices contribute to the movement of network traffic. This also makes it very difficult to implement network security on ad hoc topology. Also, there's no means of connecting participating devices to the internet unless one of the connected devices has internet access. Since one device connects all participating device to the internet, the overall performance of this device would be greatly affected.
Just as the name implies, the infrastructure mode is a wireless setup whereby infrastructures are put in place and serves as a connecting point to the local network. This device put in place to enable wireless connections to local area network is known as Access Point (AP). Whenever you walk into an office and see a wireless network notification on your smartphone, surely there must be an AP close by and they're usually seen as a white colored (usually white-colored because they're usually placed close to the roof and roofs are usually painted white) piece with a bright green, blue or white indicator led.
Not all access point are kept indoors, the image above is an outdoor wireless AP which connects wireless clients to a DS. Source, license
Just as stated above, no one connects to the AP because they like its color or its name, the only reason we connect to the AP is to have access to the network infrastructure or network backend. This network backend is known as the Distribution System (DS). This is to say that when you set up a hotspot and have your friends connect to the internet through your smartphone, your phone becomes an AP and the DS is the mobile network you're currently connected to.
Our eyes cannot see radio signals and we are not also enhanced to sense them but our phones can, but what enables our wireless devices to distinguish between different radio signals? Every AP broadcasts its name along with its services, this is known as a Service Set Identifier (SSID). Any wireless device within a Basic Service Area (BSA) can connect to the broadcasting AP with the right authentication details (if it is enabled on the AP).
Remember I stated above that the BSS (basic service set) is the maximum distance away from a wireless client at which signal can be sent to and or received from the device. The BSA is the maximum distance away from the AP at which signal can be sent to and or received from a wireless access point, this can also be called a cell.
Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) and Wireless Frames
Let's say you've got this high-end PC from a retail store with the attendant telling you that it can surf the web with mind-boggling speeds and you just can't wait to plug this PC to the amazing dedicated internet connection you just set up. You're finally at home and ready to boot the PC with your AP already booted up and your network fully functional, when your PC comes up how does it know that there's a wireless network available for connection and how does it know when to safely transmit without running its traffic against traffic coming from other devices or even from the AP?
The network can be seen as a road through which signals traverses. When there are signals from many sources, we term such, a traffic. The Ethernet (IEEE 802.3) uses what is known as CSMA/CD (carrier sense, multiple access with collision detection) to detect and recover from a traffic collision.
To illustrate CSMA/CD assume the Ethernet links (IEEE 802.3) to be a straight double lane road and the network traffic seen as a car trying to use the road. For the car to use the road, the driver just look in both directions and if he "feels" the road is free, he jumps into to the road, if he is lucky, he might just make it to his destination but if he is unlucky, he'll just collide with another vehicle and the agency responsible for managing "accidents" will be called upon to save the day.
This is to say that collisions are allowed to happen in wired links (IEEE 802.3) and this also allows traffic flow in both directions (full-duplex communication). The case is totally different for wireless links, here, collision is not allowed to occur and communication is only in half-duplex mode. How are collisions totally avoided in wireless links?
To illustrate how CSMA/CA works let's use the previous scenario. Here, the car is still trying to access the road but this time, the road is single lane and the driver has a very fast dog in the car. Before he uses the road, he sends the dog to run very fast across the road and if the dog successfully returns from the trip, the drive is very sure the road is free and then starts his journey.
In reality, before a host can use a wireless link (IEEE 802.11), it will first send a Request To Send control (RTS) signal down the link it intends to use, if the link is free, a Clear To Send (CTS) control signal will be sent to the host as an acknowledgment to go ahead and use the medium. Let's get to know IEEE 802.11 frames in detail.
The wireless local area network uses three groups of frames to carry out its operations, these frames are grouped as;
- Management frames
- Control frames and
- Data frames
The management frames include Probes, Authentication, Beacon and Association. In order for our device to discover access points, the access points constantly transmit wireless beacon frames, giving out information like AP name (SSID), supported protocols, channel information, Media Access Control (MAC) address, Vendor information, etc.
For a device to learn about a wireless network using beacon frames, it means the device waited passively and only have to respond to beacon frames but this is not always the case. A wireless device after waiting to receive a beacon frame could without success, go active and start looking for an available access point. To do this, the host start sending Probe frames. The probe frame is divided into probe request and probe response.
The probe request is sent by is sent by devices looking for an access point and includes in the frame, its supported data transfer rates, its frequency channel information, its MAC address as the source address and a destination MAC address of all "Fs" (Broadcast MAC address). When an access point receives a probe request, it responds with a frame that is very similar to the beacon frame, the only difference is that the frame has a destination MAC address of the probing host, the rest of the field is the same as the beacon frame.
Once a host and access point link has been successfully initiated, communication then controlled using the Control frames. Control frames include a Request To Send (RTS) frame, a Clear To Send (CTS) frame and an Acknowledgement (ACK) frame. These control frames ensure that there's no traffic collision in the network.
Once a device is actively participating in a wireless network, each device randomly picks a countdown number from 0 to 31. Let's say a device connects to an access point and picks the number 25 and starts counting down in microseconds. The time in between each countdown is known as Slot time and this varies across wireless standards (as we will discuss shortly). For example, in IEEE 802.11g, the slot time or the time in between countdown is 9 microseconds.
As the device keeps counting down, another devices' countdown might've reached zero (0) and has the right over the medium. The currently transmitting device transmits along with its payload, the amount of time it will spend on the medium. This is known as the NAV (the Network Allocation Vector) and is communicated to every connected device. Once a counting down device receives the period, it adds it to the remaining countdown time. That is to say that if a device counting down to transmit receives a period information of say 300 microseconds from an access point, it quickly increments its current period by 300 and continues counting down.
A device can only transmit if it successfully counts down to zero. Once the countdown hits zero, the device wishing to transmit sends an RTS frame and upon the reception of a CTS frame is now eligible to use the medium and can only spend the amount of time it specified in its NAV field.
The ACK frame is used to ensure that frames and packets reach its destination. Once a sender receives the acknowledgment frame, the data is assumed to have been sent successfully.
Wireless LAN specifications and Standards
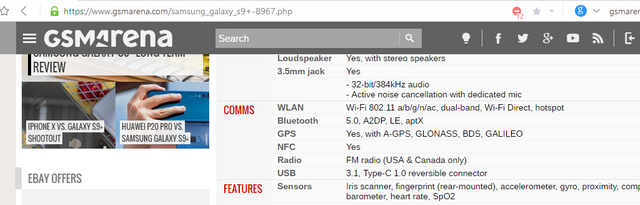
Many of us are in the waiting list for the Samsung Galaxy S10 flagship phone and part of the features that were rumored be a 5G smartphone, on-screen fingerprint scanner, 600 pixels per inch display, Ultra Fast Storage 3.0(UFS 3.0), dedicated AI chip, Wi-Fi speeds in gigabit range and so much more. Only very few take time to check the Wi-Fi specification and the few that did look up the specification lacks the in-depth knowledge of the difference in wireless LAN specifications and standards.
A screenshot from Gsmarena web page on Galaxy S9+ features and review
The screenshot above shows the Wi-Fi standards supported by the Samsung Galaxy S9+ which include the IEEE 802.11a, b, g, n, and ac. Let's get to know what these alphabets stand for before that, let's get to know the wireless LAN frequency channel spectrum.
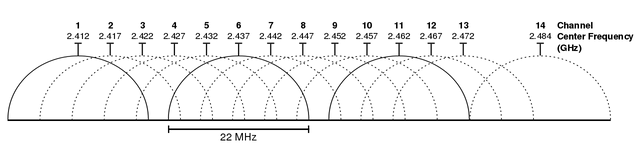
Wi-Fi frequency channels available in the 2.4GHz frequency. Source, License
The Institute of Electrical and Electronics Engineers (IEEE) is responsible for setting standards for layer 1 and layer 2 on the internet technology, apart from the standard body, we also have the regulatory bodies, for instance, the FCC (Federal Communication Commision) is responsible for the regulation of communication technologies in the United States and they ensure that wireless devices used in the US operate under agreed frequency, channel and transmission power.
When a wireless device is said to be operating in 2.4GHz frequency, it doesn't mean the device is locked to a single frequency but a group of frequencies as shown above. The first wireless standard was the 802.11 which operates only in the 2.4GHz range with a channel width of 22MHz.
Looking at the frequency spectrum above, if a device using the 802.11 legacy technology is operating at say, channel 6, the device can communicate with other devices in channels 2, 3, 4, 5, 7, 8, 9 and 10. The implication of this is that interference is also actively happening among the listed channels. Hence, there are exactly three non-overlapping channels shown in the spectrum in thick lines and is observed in today's wireless LAN networks.
The legacy 802.11 standard was able to transmit and receive at speeds up to 2MbPs using a technology called frequency-hopping and this involves choosing series of frequency channels by both communicating device and an agreed algorithm used to quickly send and receive signals these channels.
Using the 802.11 standards, the 2.4GHz spectrum was quickly over crowded and interference became the order of the day. A saving grace was the introduction of 802.11a which was introduced in the year 1999 and introduced a whole new frequency spectrum, the 5GHz range and could transmit at speeds up to 54MbPs using the Orthogonal Frequency Multiplexing (OFDM) modulation technique.
More on the standards, regulations and specifications in my next post.


)
This is a really wonderful blog. You allow for our ignorance--yes, I am pretty much in the dark about how all of this works--but not so much anymore. No one ever bothered to explain what all those acronyms mean. I turn on my PC and it works. If it doesn't I call my son. Now, though I have a better overall idea of the logic that allows my PC to connect to a network.
The only objection I have to your article is the bit about the dog. Leave the dog in the car :)
that was very funny, anyway, I'm happy you took time to go through my work.
This post has been voted on by the SteemSTEM curation team and voting trail in collaboration with @curie.
If you appreciate the work we are doing then consider voting both projects for witness by selecting stem.witness and curie!
For additional information please join us on the SteemSTEM discord and to get to know the rest of the community!
Congratulations @henrychidiebere! You received a personal award!
Click here to view your Board of Honor
Congratulations @henrychidiebere! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!