Meet “Goldilock”: the benefits of hot + cold storage without their potential risks!


Sensitive data needs to be secured, but it also needs to be available
In a world as fast paced as the one in which we are living, there are a lot of situations where we need to have access at a moments notice to some personal information so a certain procedure can continue its course. It can be related to our finances, our health, or any other sensitive field that always require a proper privacy, safety, but also efficiency when providing the information that is required.
In these cases, the wise thing is to approach the handling of our sensitive information with a lot of precaution, to protect ourselves from possible accidents or attacks that could cause us harm.
However, when it comes to the security of our sensitive information, in the majority of the cases, it relies on the hands of a third party that is responsible for the security protocols that are applied, which means, we aren’t really in proper control over our private and sensitive information, but rather we kind of outsource that control to entities that in theory, should be experts in implementing all types of security measures to protect the users.
There are 2 common methods of storing sensitive information, such as:
Hot storage
Most of the information around the world is stored this way. It consists in simply uploading the information to the internet in order for it to be accessible immediately. The majority of centralized organizations use this method to store the information they manage.
Having everything available to be accessed without wasting time can surely allow any organization to function in a very efficient matter, but it comes with considerable risks. Every major hack, whether it is in the crypto industry where malicious hackers figure out a flaw in the code and use it to stole millions of dollars from online wallets, or with more traditional companies like AdultFriendFinder and the security breach they suffered in 2016 where millions of their users had their private information exposed because of the hack, every single one of these cases wouldn’t have happened if that information had not been permanently available in the internet.
Storing information that is constantly available online will always have risks because even if it is totally secure in the present, maybe there is a security flaw that has not been discovered as of yet, and eventually a hacker could take advantage of that vulnerability. However, most organizations use this method because so far it is the only practical one that allows them to continue with their activities in a proper way.

Cold storage
In this method, the information is not permanently available in the internet, it is completely disconnected and isolated, in such a way that only the owner can have physical access to the device where the information is stored. This type of storage is specially common in the blockchain industry to safely store private keys that allow access to cryptocurrency holdings.
Since there is no way a remote hacker can have control over the device because there is no way to reach it, it is essentially unhackable, but the fact it is just a single gadget being used as the medium to store the information means there are other types of risks.
First of all, the simplicity factor is nonexistent for people that have no proper knowledge when it comes to managing the latest technology, and the mental worry of doing some kind of mistake that could make the information inaccessible makes it unlikely to be adopted by a lot of people. The typical users that buy cold storage solutions are individuals with no problem in learning how to use new technological gadgets, but this is clearly not the case with most people.
Another potential risk is present in those cases where the information is only stored in one single device, with no extra backups, if due to some accident or disaster that device is physically destroyed, it would make the information inaccessible as well. Therefore, the physical integrity of the device would be of huge importance. A similar risk can be found in case of the device being lost or stolen.
Finally, since having access to the information is only possible through the physical handling of the device, if the person forgets to carry it with him, he wouldn’t be able to use the stored data.
Once of all these issues are taken into account, it is not difficult to come to the conclusion there must be a way that allows individuals and organizations to handle their sensitive information in a secured way, but also allowing it to be rapidly accessible, or in other words, to have both the benefits of a hot and cold storage, without none of its risks.
This is exactly what Goldilock is bringing to the market.

What is Goldilock and their solution to handle sensitive information?
Goldilock is a new project bringing to the market a new method of handling digital assets, which allows for the information to be remotely stored, away from potential hackers, while at the same time being accessible at any moment in case the owner of said data requires it.
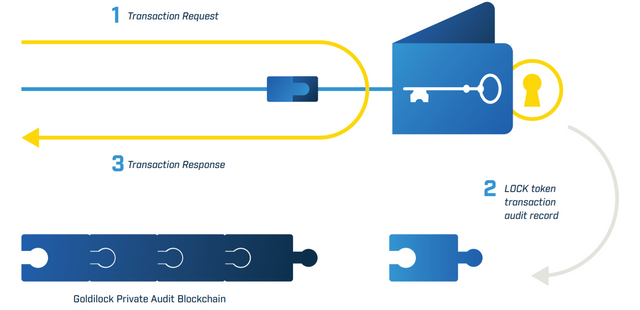
This is achieved thanks to the airgap technology, this means a particular system is not connected to any other system, network or device, it remains completely isolated for security purposes, therefore the data will have a temporal online access only when being used, the rest of the time it will remain in its safe offline storage, as shown in the image below:
The security of a system such as this one is that no malicious malware can be used against the system, and there is no way for a hacker to find access, simply because there won’t be any connection between the system and the hacker.
In order to have access to the information, Goldilock “leverages multi-factor authentication, biometrics, regressive non-IP technologies triggers, and cryptography” | Source to make sure everything happens without having any security breach.
Some of the security features in use are the following:
This way, Goldilock can offer the availability of a hot storage, while also having the security of a cold storage, making everything much easier for the users and allowing everyone to feel more secure when going through situations in which private and sensitive data needs to shared between different parties, there will be no more worries since the typical risks associated with the previous methods of managing private information are eliminated once and for all.
With this new level of security, people in general should feel confident enough to increase their involvement in the crypto industry, it is very likely that a lot of individuals are driven away after reading all the stories about millions of dollars being stolen by hackers, it can make anyone feel an intense fear caused by the slightest possibility of this happening to them, but with the solution Goldilock is offering, there shouldn’t be more fears about being hacked or about losing certain data, every risk has been analyzed and taking into account when designing this tool, therefore, an increase level of security is the end result. This should make the crypto industry a less risky place to get involved, and more people might start to take part in this technology, driving up the adoption and luckily expanding the blockchain industry even further.

Applications and use cases
A method such as the one described from Goldilock have tons of potential use cases, ranging from banks, to hospital, and of course, blockchain projects.
The system can be leveraged to store private cryptocurrency keys, banking and credit information, personal identity, health data, digital media, and signature or approval keys. | Source
Benefits and use case to individual consumers
A particular person will find it much easier to store his private information like health records, credit data, ID documents, and the private keys of his crypto holdings using Goldilock, this way, he eliminates the risk of being hacked and the risk of losing his documents. A specific use case could be the following:
Tom is a very busy person with a lot of responsibilities and a lot of stress, a few months ago he was hacked and lost some money because of it, and it is no surprise to see him losing documents and other items on a constant basis because of his stress, if things don’t change Tom will probably collapse.
Luckily, he discovers the Goldilock solution, and start to use it right away. Now, he is protected not only from malicious hackers, but also from his problem regarding the misplacing of documents. With Goldilock he will always have a safe way to access his documents while also being protected from online attacks.
As a result, Tom stress starts to decrease and his health starts to improve.
Benefits and use case to banks
Banks have some of the most highly sophisticated security protocols there are, however, that doesn’t mean there are not hacks or accidents that could harm them and their customers. There are cases where banks have been hacked, money stolen and customer’s private information exposed.
Regarding the private information of the customers, it could very well be completely protected by Goldilock’s solution, because that information wouldn’t be available online on a permanent basis, which will make the hackers unable to get to it. A simply use case can be like this:
There is a bank that got hacked because of a vulnerability in its security method, they have a lot of information stored in their servers, and everything was in the hands of the hackers.
The hackers published that information, revealing sensitive information from a lot of customers, as a result, the bank’s clients were very disturbed and some of them close their account because they lost confidence in the bank.
Since the reputation of the bank was negatively affected, they decided to research a solutions that could prevent this from happening again, and they found out about Goldilock. They adopt it, and now their clients private information is protected from potentials hacks, they announced the implementation of Goldilock, and slowly their image as a bank started to improve, even to the point of recovering some of the clients previously lost due to the hack.
Benefits and use case to insurance companies and health providers
This type of entities always have access to extremely sensitive information regarding the health conditions of their clients and they are responsible for safeguarding that information in order to protect their privacy.
It would be a wise decision for these entities to take advantage of the method offered by Goldilock, with the goal of providing the ultimate security to their clients regarding the protection of their private data. Similar to the previous example about the banks, if any of these entities were hacked, it would cause great harm to their clients because their information would be totally exposed, and people would lose trust in the particular hospital or insurance company that got hacked. The previous use case about the bank could also be applied in this case, only that instead of financial records, the information hacked would be health records.
Benefits and use case to crypto exchanges and crypto wallets operators
One of the riskiest places to store crypto currencies is in hot wallets, and most of the hacks and stolen money in this industry has come from hackers that figured out a way to access funds in hot storage, it has happened both to exchanges and wallets operators.
If both of them implemented the Goldilock’s solution when managing the private keys, those hacks wouldn’t have happened in the first place. Regarding the wallets operators, Goldilock can be integrated with both cold and hot wallets that already exist and are in use, allowing them to offer an improved service to their customers. A particular use case could be like this:
A hot wallet was getting a lot of hype thanks to its simply interface and reliable service, but unfortunately, one day a group of malicious hackers discovered a vulnerability and got access to the crypto holdings of people using this wallet.
The users lost their money and the wallet was near closure, because no one wanted to use it given the risks. The wallet developing team decides to implement Goldilock’s API that allows their hot wallet to have the same security benefits of a cold wallet, making it one of the most attractive and successful available wallets.

Goldilock is highly versatile given the fact it can be implemented in several ways, according to the whitepaper, “Goldilock API Services will run on-premise, in our colocation facilities, and in the Cloud. These services will make it easy for enterprises and partners to create privacy-focused, consent driven applications. The APIs can be embedded within non-decentralized applications or into stand-alone dApps.” | Source Besides, since this solution is going to be patented, any third party wishing to implement it would have to do it with the collaboration of Goldilock team.
With the goal of taking advantage of the most compatible blockchain in which to develop their project, Goldilock will initially be fully compatible with NEO, it is important to notice that other blockchains will eventually be taking into account, but the following reasons make NEO the most suitable one for this particular project:
- Aims for regulatory compliance: since a lot of the uses Goldilock is offering, are for big entities that are constantly storing sensitive information, the fact that NEO will allow certain entities to audit digital information as well as issuing digital identities is of great help. This feature will make everything easier when implementing the Goldilock solution in a bank or insurance company.
- NEO has a Superior Consensus Mechanism: in every blockchain the consensus mechanism is the way in which decisions are taken, it is use "to achieve the necessary agreement on a single data value or a single state of the network among distributed processes or multi-agent systems. It is useful in record-keeping". SourceThe consensus mechanism used in NEO is Delegated Byzantine Fault Tolerance which consists in " holders of NEO tokens vote for delegates, and the delegates must reach a consensus on acceptable transactions." Source This fact makes NEO more reliable in the long term.
- Faster transactions: blockchains transactions can get very slow when the network is having too many transactions, this clearly disturbs the user experience and can make entities using the blockchain to reduce the efficiency of their operations. NEO thanks to its consensus mechanism, offers faster transactions that its competitors, with the goal of being capable of handling a large number of users without the network coming to halt. Source
These reasons, made the Goldilock team choose NEO as their chosen platform.

The token
The token that people will need to use in order to have access to Goldilock’s services is called LOCK, this token “when coupled with Goldilock’s proprietary smart contract logic, will allow for the storage of private keys for cryptocurrencies and other digital assets, as well as provide an immutable auditing mechanism for each individual node using Default Byzantine Fault Tolerance”. Source
The following image is a graphic representation of how the token is a basic element of the security system:
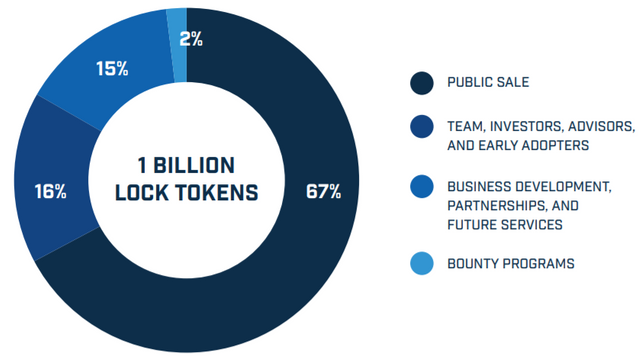
Token Allocation
As we can see in the image below, there will be 1 billion tokens in total, with the majority of those being put on sale to fund the development of the project.
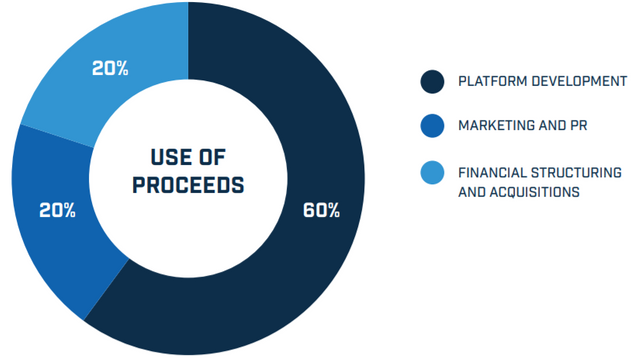
Use of funds

The team
The people behind this project have extensive experience and specialized knowledge that allowed them to come with the idea of Goldilock and make it a functional product. In the website we can find specific information about each member, as well as their LinkedIn profiles.



Advisors


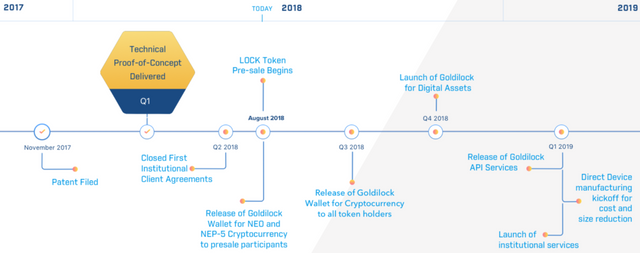
Roadmap

Summary
Common ways of storing digital information have risks that could cause serious complications to anyone, Goldilock identified this issue and developed a solution where they allow people to have secure access to their information through a sophisticated system that will be patented in the near future. This way, users can enjoy the benefits of both hot and cold storage, without any of their risks, which can certainly be a great solution not only for individuals but also for entities that are known to safeguard sensitive information of their clients, like banks, insurance companies, among many others.
- If you want to know more about this project, I invite you to visit their website.
- If you want to know more about how this platform works, please feel free to check their whitepaper.
- If you want to see informative videos about this project, you can find those here in their youtube page.
- They are also present in several social medias, such as Facebook, Twitter, LinkedIn & Telegram
Here is a video I made sharing my thoughts about this platform.
- And if you want to ask me any question about this project, feel free to leave a comment below.
This is my entry for the @originalworks writing contest
goldilock2018
Tweet: https://twitter.com/dedicatedguy/status/1027032311743868928
goldilocktwitter






This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
@dedicatedguy
Goldilock seem like a very safe spot as it offers cold and hot storage platform.....
Thanks for the information.
Yes, it offers the benefits of both methods.
Thanks for stopping by.