MY TRAITS...MY SECURITY! A GLANCE INTO THE BIOMETRIC TECHNOLOGY
Hello, hi there!
I trust your day has been awesome? Have you ever seen this popular movie called “MISSION IMPOSSIBLE”, I guess we movie freaks have seen every episode of this awesome movie. This movie where the main cast Tom Cruise could penetrate any security, bypass any authentication. He could do that using either a false facial recognition of the original person or a false thumb/finger print gotten from their advanced technique or even go as far as copying a particular voice and using it as an access. After watching this movie, I feel like I could do something cool like that but common, this is real life not a movie. It might be possible though…so from the stable of sparklez article, I bring to you this wonderful write-up about the Biometrics Technology. Truth be told, the trending technology in Nigeria right now is the fascinating fingerprint feature that comes with most mobile phones. Everyone wants an android device with the fingerprint feature, no one wants to be left behind. The funny thing is that majority of these people have absolutely no idea how this stuff actually works or what this stuff is. All they know and are concerned about is having a phone that they can stick their finger to and it would magically unlock without having to key in long passwords or draw hideous patterns that look like bees in a war zone. Alright, enough preamble gist, let’s talk biometrics, more specifically let’s talk “Biometrics Technology”. That phrase shouldn’t be strange at all but I bet that you will be shocked at how that much it actually does entail so, get ready to be blown away by what you didn’t know about biometrics technology.
Biometrics Technology
Biometric technologies are used to create a database or profile of people’s identity, based on their physical and behavioural characteristics on the computer. It can be used to identify individuals, which means whenever you do a registration requiring a thumb/finger print, a facial recognition or a signature verification, your biometrics are recorded or stored in the database of a particular company or the government and this include all automated methods of identifying a living person based on unique physiological or behavioural characteristics. Biometrics are used to attain high confidence, conveniences and secure authentication since they are known for their uniqueness which cannot be easily stolen or forgotten and are very difficult to forge, and besides who has the technology for that level of forgery in Nigeria. Most time, the biometrics technology are used for security purposes, they are used for access control to a particular resource by the government, a company, group, organisation or for personal purpose which means I could actually setup a biometric system in my personal house/home or even in my toilet…lol! Now, let me break this big words a bit for better comprehension. A physiological characteristic in this context simply means those characteristics in human you can see, physical characteristics which includes an individual’s facial structure, fingerprint, palm geometry, iris, or blood pattern on the back of the eye. Behavioural characteristic on the other hand are those individual characteristics gotten over time. For instance, a person’s signature which is the most commonly used behavioural biometric for identification purposes. Because most behavioural characteristics vary over time, people may decide that their current signature is no longer beautiful enough or that it's too easy to be replicated, an identification system that allows for updates is used to enrol biometric references. An example of such would be myself, I'm less than 40 years and I have already changed my signature twice, I wonder what would have happened to my bank account and my identification card if there was no room for updates in the system? Relax, as I explain some of the biometric technologies I could get my hands on. I really pray I don’t go off track, because talking about the biometrics technology, it’s so broad, so I will just be talking on the little ones. (Takes a deep breath)
Biometrics Sensors
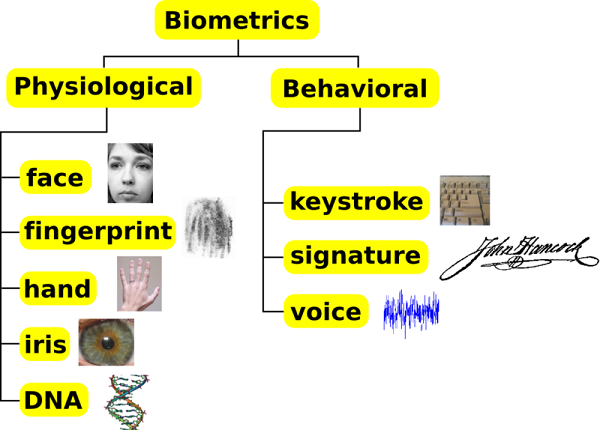
The term biometric sensors refer to those devices that transmit a person’s bio characteristics into electrical signals. The biometrics need a sensor which transmits, reads or measures various characteristics of the human part. Those biometric devices include thumb print scanner, eye/iris scanner, facial recognition, voice verification, human motion, etc. they are basically classified into two (2) which are Physiological Biometrics and the Behavioural Biometrics
Physiological Biometrics
From the term, you would know this has to do with the physical part of your body, these includes
- Finger Recognition
- Facial Recognition
- Iris / Retina Scan
- Palm / Hand Scan
- Vein Pattern Scan
Behavioural Biometrics
As the name implies, it has to do with the collection of the human behaviour into the database and this includes the
- Voice Recognition
- Human Motion
- Signature
- Typing Rhythm or Keystroke
Finger Print Recognition
This is most common of all forms of biometric technology. I will be talking about how the ten fingers ended up becoming a means of identification. The human fingerprint is a unique feature possessed by all, since no two individuals can have same fingerprints even if they were identical twin. The use of fingerprints for identification can be dated as far back as to the time of ancient Babylonians who recorded business transactions by pressing the tips of their into clay and also the Chinese who used ink-on-paper finger impressions for business and identification of their children. These were the early use of biometrics, however, it wasn’t until 19th century before fingerprints was used as a method of identifying criminals. Finger print is one of the unique feature as I’ve mentioned earlier because of the different patterns on the fingers. This is a very popular kind of biometrics because they are even used in secondary schools/colleges either for exam registration or for student data record used in identifying each student generally confirming a person’s identity. Even with all the patterns in the epidermal layer of the skin, curves here and there, it is considered to be the cheapest kind of biometric technology. You could refer to STEPHANIE WATSON, (how stuffs work), for some history on how finger prints was discovered out of an ancient piece of clay and the ideas that brought it to life.
Enough of the 1800s history reading, let’s speed up to more modern times. In the 1980s computers had already come to stay, the Japanese National Police Agency established the first electronic fingerprint matching systems ever. The Japanese’s Automated Fingerprint Identification Systems (AFIS), eventually enabled law enforcement officials around the world to cross-check a print with millions of fingerprint records almost instantaneously after it was upgraded to integrated AFIS in 1999. In every humans’ finger, you could see arcs, loops, curves, ridges and whorl, those patterns can’t be the same finger prints. That is why it’s so unique, just the same way the facial recognition don’t just recognize your face, is how the finger print recognition does. Different finger prints are collected and stored on a database system, so that when someone puts out the finger for scanning, it reads from the database and identifies the person. There are various finger prints reader used to achieve this
1. Thermal Readers: Judging from the word thermal, for those who did physics, it has to do with temperature. This reader uses temperature on the finger print on contact to the surface but the disadvantage of this reader is that most time it is often affected by climatic change or environment temperature.
2. Optical Readers: This is the well known reader and very common. This type of reader uses sensors in a digital camera that scans the finger. One of the disadvantage of this reader is that sometimes it may not read the finger if the fingers are dirty.
**3. Ultra Readers: This kind of reader make use of high frequent sound to check the outer skin layer. This reader are way expensive because of the accuracy of data it gives and the finger doesn’t need to be clean or scar-free before it could work as it uses sound waves.
The Minutiae and Pattern matching system are the process were the finger read are interpreted, compared and matched together.
Facial Recognition
Imagine a situation where you are walking on the street where you feel nobody knows you and suddenly someone comes to you and give you a full breakdown of your history…omg! What comes to your mind at that point? “Is this person stalking me, could it be this is Voodoo, Juju (African magic) or are my being pranked?” is all the questions you might ask yourself…well, it might be any of those things or it might just be that the person might be using a facial recognition biometrics technology. The facial recognition became very popular when the guy called ‘Edward Snowden’ released a particular document that the United State government was creating a program which will digitize people’s faces, using algorithms to create profiles, he then mentioned that the US government and British spies secretly monitor every details on the yahoo account. Since the facial structure does not change that much and the distances between the eyes and the nose never changes, the facial biometrics sensor through a digital camera analyses and scans the characteristics of the person’s facial structure. Before this scan takes place, the eyes, the nose, the mouth and the jaw are to be placed properly as it measures the entire structure of the face. The scanner checks for some of the features like the distance between the eyes, wideness of the nose, placement of the cheekbone and the jaw line. Which means my facial recognition security placed at home could deny me access if I don’t properly place my face towards the scanner. I hear questions like “will you just place your face on the scanner and it recognises it?” the answer is no. facial structure or faces of different type are already captured either by the government, private company or just yours for your personal security and stored in the systems database
The Retinal/Iris Scan
This is almost the same as the facial recognition but it only has to do with the eye. Most time, people are sceptical about this type of biometric system because it entails weak or low infrared light scanning your eye from scanning of the blood vessel of the eye to checking the structure of the iris. As I said earlier, people are so scared of this, as they don’t want one red light going through their eye; their though would be “what if I get blinded?” (for those that watch too much horror movies…hahaha!). Also, the iris scan came as ease to the retina scan as it scans only the white area of the eye because people are so scared of coming very close, the iris scan can detect the eye from yards away as it is easily visible
Voice Recognition
For me, I think this is like my coolest type of biometrics. Imagine where you could say something cool or weird and something happens…sweet right? Yeah! I could use this to impress a girl…lol! Well, this is a type of biometrics technology that analysis your speech. This is carried out by recording an individuals’ voice by saying or speaking 2-3 syllable words 8 times in any language they wish to, and example of this is the AT & T Smart Card that are used mostly in an automatic teller system. The individual can use any word he/she chooses and stored either on a memory card or in a database. Since the vocal tract is considered to be the originator of speech. So the voice recognition picks up the sound from a vocal tract.
Signature Verification
This is not often used by everyone as the face and finger recognition. To me, I think they are mostly used for confidentiality and security of an individual. The signature recognition is considered to be a behavioural biometrics and are measured/analysed with coordinates, pressure, inclination and when the pen is up or down. Let me use instances to state the two ways this type of biometrics operates. Let’s say I (sparklez) have billions in the bank (maybe in like 20yrs time…hahaha!), it’s just an instance guys…, and I want to withdraw it with my signature, I could write the signature on a piece of paper and then it is placed in front of a digital camera or an optical scanner for it to be analysed, this method or process is called the ‘Static Mode’ of signature recognition and its offline or I could be giving a signature pad, digitized tabled or a PDA to sign on and this goes directly into the system to be analysed, this process is called the ‘Dynamic Mode’ and its online. Imagine I really had that kind of billions in my bank account, I won’t even miss a point in my signature, I would even be signing in my dreams or sign with both eyes closed..lol! Today, most smart phones and Android phones have all this biometric embedded in them as an easy way of identification as it is convenient and easy.
To me, Biometrics is just a process that combines human biology and technology together, using those unique features in you as your security, that’s like my own personal security. All mentioned are forms of biometric technology and they all serve different purposes in the process of identification even as fingerprints still remains the most popularly used. As it has also been employed by the Nigerian government in identification process used in the National Youth Service Corps (NYSC) Enrollment. So, when next you unlock your device with your fingerprint remember that this technology did not just fall out of the sky but a product of the efforts made by many to improve identification process and reduce the need for long passwords and lock codes and in so doing make life easier. But even in making life easier, our data are taking, full profile of every individual stored in a database and these have put fear in lots of people’s heart as they fear one day their data or a whole information about them could be leaked or exposed causing a breach in contract. We all know that even if it’s not done so well in Nigeria, the US government has over billions of biometric database of individuals and people fear that one day the government will just gain all the power and an average man would have nothing to say in the country. While lots of people too are still cool with it as they say “we don’t have anything to hide and it’s for our own security”. One thing we should know is that all data taking are secured not only on a secured database but also by law governing the people. There are several laws guiding this data and cannot be used against an individual except used to haunt down criminals and fraudsters. In all I have written so far,
what is your say in biometrics technology? Do you have an issue if the government have all our data or not? Are we really secured or are we being watched?
Till I come your way next time, I remain @sparklez your humble boy!
Thank you all for reading
References
Elprocus
Getreport
How stuff works
Kinooze
Biometric Solutions
))
))
))
))
.jpg](https://steemitimages.com/DQmRRB1asMYKkux4k65gDBxqUrUT1U2TTpdKFL8FTpXgn32/Facial_Recognition_(5883951201).jpg)))
))
))
))
Hmmm! This post reminds me of the movie "persons of interest", are we really safe with this technology? Nicely written and detailed. Thank you @sparklez
Men...that feeling that we are beign watched is not a good feeling at all no mater how ok it may look to know that the govt have all our data but it only makes feel we are not secured. Hmmm
Congratulations! this post got an upvote by @steemrepo and was manually picked by the curator @yandot to be added on STEEM REPOSITORY, simply comment "YES" and we upload it on STEEM REPO Website.
Want to know more about the Steem Repo project? Contact us on Discord