Blockchain Wallets

Hello!
My name is Pavel Bogush, I am Deputy COO at Platinum, a company that knows exactly how and when to launch successful STO.
Make sure we do after visiting our site:
We not only know how, but also teach other people and create the greatest educational community in the league. I am talking about the University of Blockchain and Investing. You can get all ll up-to-date knowledge about blockchain, STO and ICO by buying our courses online.
Today I will help you understand what a Blockchain Wallet is, its purpose, and your present options for storing your coins.
Follow the link to learn more:
Lesson Objectives:
By the end of this lesson you will have learned the following things:
- You will understand what a Blockchain Wallet is, its purpose, and your present options for storing your coins.
- You will also understand previous failures of past Wallet companies, as well as what qualities to look for in a Wallet provider.
- You will understand the practicality of different kinds of wallets, the purpose of each type, and how to make an effective evaluation of each wallet.
- You will know how to create wallets by following a clear step-by-step guide.
- Finally, you will know exactly how to transfer and monitor the funds in and out of your wallet.
Terminology:
Lesson Three
Public Key: in the simplest terms, a public key is the digital key you give to someone else so they can transfer ownership of some amount of cryptocurrency to you into your own account.
Private Key: this is what you need to be able to unlock your own wallet to be able to transfer ownership of some amount of cryptocurrency to someone else.
2FA: two factor authentication, a means of verifying the interaction is legitimate by two steps of authentication, as opposed to simple one-step password access.
Web Wallet: The most important feature to understand about web wallets of any kind, is that they hold private keys for cryptocurrency accounts, and those keys are held and managed by a trusted third party.
Exchange Wallet: A form of Web Wallet contained within an exchange.
Desktop Wallet: A software program downloaded onto your computer or tablet’s hard drive that usually holds only one kind of cryptocurrency.
Phone Wallet: These are apps downloaded onto a mobile phone that function in the same manner as a desktop wallet and can hold many different kinds of cryptocurrencies.
Hardware Wallets: are basically physical pathways and keys to the location of your crypto assets on the Blockchain. Hardware wallets are thought to be more secure than any variety of web wallet because the keys are actually being stored on your own physical device. This completely removes the risk of your online wallet, or the exchange on which you make your transactions, being hacked in the same manner as MtGox and Coincheck etc.
Paper Wallet: another offline cold storage method of holding your cryptocurrency.
Brain Wallet: is a fancy way of describing the act of memorizing a mnemonic sentence which can be used to generate the private+public key pair, and also, for example, the watch-only wallet.
Watch Only Wallet: is a wallet without a private key or the ability to move coins.
Keylogging: is malicious software by a hacker to track your keystrokes to try to identify the keys to your crypto assets.1.
Purpose of Wallets
1.1 Introduction. Mechanism and Structure
Wallets in the cryptocurrency sphere are different types of software programs that store your public and private keys and allow you to interact with various Blockchains so that you, as the wallet holder, can view your balance, send and receive funds to other wallets etc., and manage other operations.
When digital currencies are being transferred, the sender is in effect signing off ownership of the coins or tokens from his or her wallet to the recipient’s wallet address. To be able to spend or send those tokens or coins, the private key must correspond exactly to the unique public address where the coins or tokens are allocated.
1.1 Introduction. Mechanism and Structure
If this is the case, the balance in the senders’ wallet will be decreased by the designated amount, and the recipient’s wallet will be increased by the same amount (perhaps less a small fee).
The transaction is merely the electronic transfer of ownership in the form of a digital signature on the Blockchain from one wallet address to another.
1.1 Introduction. Mechanism and Structure
1.1 Public/Private Key
The public key is the digital code you give to someone that wants to transfer ownership of a unit of cryptocurrency to you; and a private key is what you need to be able to unlock your own wallet to transfer a unit of a cryptocurrency to someone else.
The encoding of information within a wallet is done by the private and public keys. That is the main component of the encryption that maintains the security of the wallet. Both keys function in simultaneous encryption systems called symmetric and asymmetric encryption. The former, alternatively known as private key encryption, makes use of the same key for encryption and decryption. The latter, asymmetric encryption, utilizes two keys, the public and private key, wherein a message-sender encrypts the message with the public key, and the recipient decodes it with their private key.
1.1 Public/Private Key
The public key uses asymmetric algorithms that convert messages into an unreadable format. A person who possesses a public key can encrypt the message for a specific receiver.
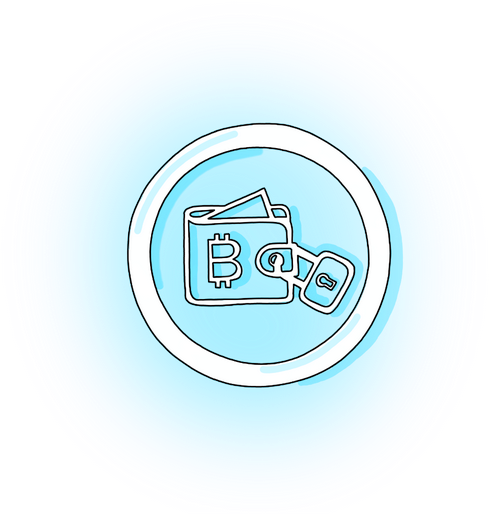
Accessing wallets
Methods of wallet access vary depending on the type of wallet being used. Various types of currency wallets on an exchange will normally be accessed via the exchange’s entrance portal, normally involving a combination of a username/password and optionally, 2FA (Two factor authentication, which we explain in more detail later). Whereas hardware wallets need to be connected to an internet enabled device, and then have a pin code entered manually by the user in possession of the hardware wallet in order for access to be gained.
1.1 Public/Private Key
Phone wallets are accessed through the device on which the wallet application has been downloaded. Ordinarily, a passcode and/or security pattern must be entered before entry is granted, in addition to 2FA for withdrawals.

1.2 A Brief History
Satoshi Nakamoto built the Satoshi client which evolved into Bitcoin in 2009. This software allowed users to create wallets and send money to other addresses. However, it proved to be a nightmarish user experience, with many transactions being sent to incorrect addresses and private keys being lost.
Image of first wallet
The MtGox (Magic the Gathering Online exchange, named after the original intended use of the exchange) incident, which will be covered in greater detail later, serves as a reminder of the dangers present in the cryptosphere regarding security, and the need to constantly upgrade your defenses against all potential hacks.
The resulting loss of 850k BTC is a still unresolved problem, weighing heavily on the victims and the markets at large. This caused a huge push for a constantly evolving and improving focus on security.
Exchanges that developed later, and are thus considered more legitimate and secure, such as Gemini and Coinbase, put a much greater emphasis on vigilance as a direct result of the MtGox hacking incident. We also saw the evolution of wallet security into the physical realm with the creation of hardware wallets, most notable among them the Ledger and Trezor wallets.

The simplest way to sift through the dozens of cryptocurrency storage methods available today, is to divide them up into digital and non-digital, software and hardware wallets.
There are also less commonly used methods of storage of private keys, like paper wallets and brain wallets. We will examine them all at least briefly, because in the course of your interaction with cryptocurrencies and Blockchain technology, it is essential to master all the different types of hardware and software wallets. Another distinction must be made between hot wallets and cold wallets. A hot wallet is one that is connected to the internet, and a cold wallet is one that is not.
Fun fact:
The level below cold storage, deep cold storage has just recently been implemented by the Regal RA DMCC, a subsidiary of an internationally renowned gold trading company licensed in the Middle East. After having been granted a crypto trading license, Regal RA launched their “deep cold” storage solution for traders and investors, which offers the ability to store crypto assets in vaults deep below the Almas Tower in Dubai. This storage method is so secure that at no point is the vault connected to a network or the internet; meaning the owners of the assets can be sure that the private keys are known only to the rightful owners.
How to create wallets by following a clear step-by-step guide?
Become the wallets master after finishing the full Basic course online:
Software Wallets – Web/Exchange/Desktop/Phone Wallets
The following varieties of crypto wallets will all be covered in more detail soon, but first we will take a quick look at specific features and functionality.1
Software Wallets
wallet applications installed on a laptop, desktop, phone or tablet.2
Web Wallets
A hot wallet by definition. Web Wallets are accessible through the web browser on your phone or computer. The most important feature to recognize about any kind of web wallet, is that the private keys are held and managed by a trusted third party. MyEtherWallet is the most commonly used non-exchange web wallet, but it can only be used to store Ethereum and ERC-20 tokens.
Though the avenue of access to MEW is through the web, it is not strictly speaking a web wallet, though this label will suffice for the time being. The MEW site gives you the ability to create a new wallet so you can store your ETH yourself. All the data is created and stored on your CPU rather than their servers. This makes MEW a hybrid kind of web wallet and desktop wallet.3
A form of Web Wallet contained within an exchange. An exchange will hold a wallet for each individual variety of cryptocurrency you hold on that exchange.
A software program downloaded onto your computer or tablet hard drive that usually holds only one kind of cryptocurrency. The Nano Wallet (Formerly Raiwallet) and Neon wallet for storage of NEO and NEP-5 tokens are notable examples of desktop wallets5
Phone Wallets
These are apps downloaded onto a mobile phone that function in the same manner as a desktop wallet, but actually can hold many different kinds of cryptocurrency. The Eidoo Wallet for storing Ethereum and its associated tokens and Blockchain Wallet which currently is configured to hold BTC, ETH and Bitcoin Cash, are some of the most widely used examples.
Hardware wallets are basically physical pathways and keys to the unique location of your crypto assets on the Blockchain. These are thought to be more secure than any variety of web wallet because the private key is stored within your own hard wallet, an actual physical device.
This forcibly removes the risk your online wallet, or your exchange counter party, might be hacked in the same manner as MtGox.

1.3 Hardware wallets – Ledger/Trezor/Alternatives
In hardware wallet transactions, the wallet’s API creates the transaction when a user requests a payment. An API is a set of functions that facilitates the creation of applications that interact and access features or data of an operating system. The hardware then signs the transaction, and produces a public key, which is given to the network. This means the signing keys never leave the hardware wallet. The user must both enter a personal identification number and physically press buttons on the hardware wallet in order to gain access to their Blockchain wallet address through this method, and do the same to initiate transfers.
1.3 Paper Wallets
Possibly the safest form of cryptocurrency storage in terms of avoiding hacking, Paper Wallets are an offline form of crypto storage that is free to set up, and probably the most secure way for users, from beginners to experts, to hold on to their crypto assets. To say it simply, paper wallets are an offline cold storage method of storing cryptocurrency.

1.3 Paper Wallets
This includes actually printing out your public and private keys on a piece of paper, which you then store and save in a secure place. The keys are printed in the form of QR codes which you can scan in the future for all your transactions. The reason why it is so safe is that it gives complete control to you, the user. You do not need to worry about the security or condition of a piece of hardware, nor do you have to worry about hackers on the net, or any other piece of malware. You just need to take care of one piece of paper!
1.3 Lesser used forms of Wallets
Other forms of wallet types include the Brain Wallet which is a fancy way of describing the act of memorizing a mnemonic sentence which can be used to generate the private+public key pair, and the watch-only wallet.
A wallet without any private keys or seed in it is called a Watch Only Wallet. This kind of wallet is useful for situations where you just want to be able to view balances and transactions on a computer connected to the internet without any chance of you or anyone else being able to move, transfer, or spend any cryptocurrency within it. It is for keeping track of transactions only.
1.3 Lesser used forms of Wallets
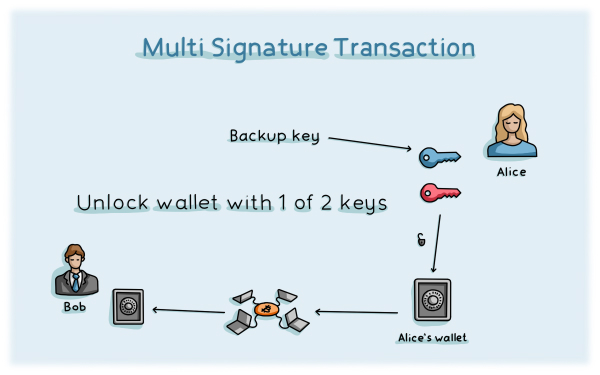
Multi-Signature wallets are primarily used by people, normally traders or exchanges, that are pooling their crypto assets together. These wallets function identically to single person sole-signature wallets, except that 2 or more signatures are required to transfer or spend any of the crypto assets therein.
1.4 Real World Historical Examples of Different Wallet Types
Web Wallet: Blockchain.info Brief mechanism & Security
Blockchain.info is both a cryptocurrency wallet, supporting Bitcoin, Ethereum and Bitcoin cash, and also a block explorer service.
The wallet service provided by blockchain.info has both a Web Wallet, and mobile phone application wallet, both of which involve signing up with an email address, and both have downloadable private keys.
1.4 Real World Historical Examples of Different Wallet Types
Two Factor Authentication is enabled for transfers from the web and mobile wallets, as well as email confirmation (as with most withdrawals from exchanges).

1.4 Real World Historical Examples of Different Wallet Types
The Eidoo wallet is a multi-currency mobile phone app wallet for storage of Ethereum and ERC-20 tokens.
The security level is the standard phone wallet level of email registration, confirmation, password login, and 2 factor authentication used in all transfers out. You may find small volumes of different varieties of cryptocurrencies randomly turning up in your Eidoo wallet address. Certain projects have deals with individual wallets to allow for “airdrops” to take place of a particular token into the wallet, without the consent of the wallet holder. There is no need to be alarmed, and the security of the wallet is not in any way compromised by these airdrops.

1.4 Real World Historical Examples of Different Wallet Types
Neon Wallet
The NEON wallet sets the standard for web wallets in terms of security and user-friendly functionality. This wallet is only designed for storing NEO, Gas, and NEP-5 tokens (Ontology, Deep Brain Chain, RPX etc.). As with all single-currency wallets, be forewarned, if you send the wrong cryptocurrency type to a wallet for which it is not designed, you will probably lose your tokens or coins.
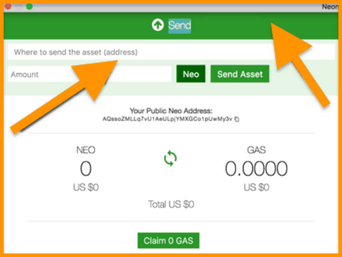
1.4 Real World Historical Examples of Different Wallet Types
MyEtherWallet
My Ether Wallet, often referred to as MEW, is the most widely used and highly regarded wallet for Ethereum and its related ERC-20 tokens. You can access your MEW account with a hardware wallet, or a different program. Or you can also get access by typing or copying in your private key. However, you should understand this method is the least safe way possible, and therefore is the most likely to result in a hack.
1.4 Real World Historical Examples of Different Wallet Types
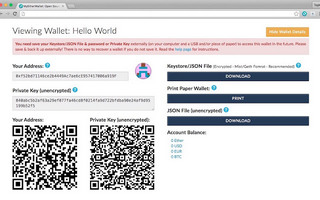
1.4 Real World Historical Examples of Different Wallet Types
Hardware: Trezor/Ledger Brief History Mechanism and Security
A hardware wallet is a physical key to your on-chain wallet location, with the private keys contained within a secure sector of the device. Your private key never leaves your hardware wallet. This is one of the safest possible methods of access to your crypto assets. Many people feel like the hardware wallet strikes the right balance between security, peace of mind, and convenience.
1.4 Real World Historical Examples of Different Wallet Types
3.1d)Paper Wallet
Paper wallets can be generated at various websites, such as https://bitcoinpaperwallet.com/ and https://walletgenerator.net/. They enable wallet holders to store their private keys totally offline, in as secure a manner as is possible.

1.5 Real World Example
Poor Practice
MtGox Hack history effects and security considerations

MtGox was the largest cryptocurrency exchange in the world before it was hacked in 2014. They were handling over 70% of BTC transactions before they were forced to liquidate their business. The biggest theft of cryptocurrency in history began when the private keys for the hot wallets were stolen in 2011 from a wallet.dat file, possibly by hacking, possibly by a rogue employee. Over the course of the next 3 years the hot wallets were emptied of approximately 650000 BTC. The hacker only needed wallet.dat file to access and make transfers from the hot wallet, as wallet encryption was only in operation from the time of the Bitcoin 0.4.0 release on Sept 23rd 2011.
1.5 Real World Example
Even as the wallets were being emptied, the employees at Mt Gox were apparently oblivious to what was taking place. It seems that Mt Gox workers were interpreting these withdrawals as large transfers being made to more secure wallets.
The former CEO of the exchange, Mark Karpeles, is currently on trial for embezzlement and faces up to 5 years in prison if found guilty.
The Mt Gox hack precipitated the acceleration of security improvements on other exchanges, for wallets, and the architecture of bitcoin itself. As a rule of thumb, no small-to-medium scale crypto holders should use exchange wallets as a long-term storage solution. Investors and experienced traders may do this to take advantage of market fluctuations, but exchange wallets are perhaps the most prone to hacking, and storing assets on exchanges for an extended time is one of the riskiest ways to hold your assets.
BitGrail

In a case strikingly similar to the MtGox of 2011-2014, the operators of the BitGrail exchange “discovered” that approximately 17 million XRB ($195 million worth in early 2018) were missing. The operators of the exchange were inexplicably still accepting deposits, long after they knew about the hack. Then they proceeded to block withdrawals from non-EU users. And then they even requested a hard fork of the code to restore the funds. This would have meant the entire XRB Blockchain would have had to accept all transactions from their first “invalid” transaction that were invalid, and rollback the ledger.
The BitGrail exchange attempted to open operations in May 2018 but was immediately forced to close by order of the Italian courts. BitGrail did not institute mandatory KYC (Know your customer) procedures for their clients until after the theft had been reported, and allegedly months after the hack was visible. They also did not have 2 factor authentication mandatory for withdrawals. All big, and very costly mistakes.
How to create wallets by following a clear step-by-step guide? Become the wallets master after finishing the full Basic course online:
UBAI.co
Contact me via Facebook to get actual info on the courses and Platinum services:
Facebook