Be Anonymous on The Internet
Anonymity has been in the news for the last 10 years, especially since the advent of social networks and surveillance devices.
Being anonymous on the Internet has become a luxury, and many people are willing to pay to anonymize their connection and their traces on the Internet.
In concrete terms, what is anonymity?
To be anonymous is remaining unknown, unidentifiable. Anonymity guarantees respect for one's own privacy. Being anonymous allows you to feel safe and to surf more or less without consequences. And finally, anonymity allows in some cases to override censorship and restrictions.

The mask worn by "V" in "V for Vendetta" became symbol of the group "Anonymous". I strongly suggest you to take a look at their site.

Why being anonymous on the Internet?
Because after all, when you do not download illegally, and you do not hack anyone, is there a real reason to be anonymous?
The problem with the Internet is that various data about us are collected without anyone noticing it. This seems trivial, but the importance of these data can very quickly tip the scales.

What data is recovered?
Did you know that:
Facebook's robots know what you like to do / read / hear / see, they know how to interpret published photos and can even recognize you on photos where you are back.
Your IP address, cookies, information about your browser, your browsing habits (all your data transmitted...) can be recovered or intercepted very easily.
The SpyWare do not destroy anything on your system but collect all kinds of information on your computer and especially on YOU for various purposes (especially advertising).
The revelation by a British newspaper of a surveillance program existence called PRISM, led by the National Security Agency (NSA), showing that Apple, Google, Facebook, Yahoo ... etc are associated with the program to monitor users.
Google knows more about you than your mother. For example, Google knows and retains all the terms you've been looking for, see it here (provided that you are logged in to your account)
The data you think you have deleted from a site, blog, forum ... etc are still online and visible to everyone.
And this is only a barely visible part of the iceberg.
Here is an article showing what is possible to recover (only partially) on you, just by visiting a site.
It must be known that these recovered data are not just technical data. The Big Data associated with Machine Learning makes possible to interpret a great deal of results in a very short time and to draw conclusions.
In other words, a simple GPS position does not say a lot except that a device is physically located in a given location. But this position associated with Google searches, visited sites and instant conversations allows the data to speak to a whole new level. And for example, to discover that this position indicates the location of a bar where you had joined your musician friend for the rehearsal of a concert that will take place in a week in Berlin and for which you are anxious.

How to become anonymous on the Internet?
There are 3 options for surfing anonymously, but they are not worth all.
Don’t want to read everything? There are the three recommended solution to become anonymous:
Choose a recommended VPN like HideMyAss, NordVPN or more recently ExpressVPN (the last tested service)
Keep good practices in mind or you may lose your anonymity.
Stay safe against malware on the Internet by using good protection programs, it's just as important!
These points will be developed in the article. But before that, here are the 3 options to become anonymous.

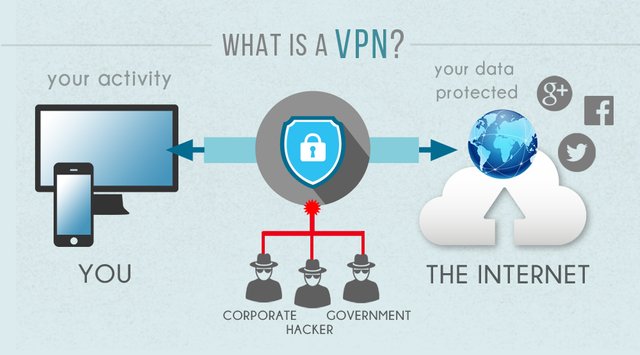
1. First option (the good one): use a Virtual Private Network (VPN)
Source
VPNs rely on a tunneling protocol. It’s a protocol allowing to encapsulate and to encrypt data transferred from one machine to another. We are talking about tunnel because the information are not readable during the transfer.
Concretely, the data is encrypted from the device using the VPN (computer, smartphone, tablet, router ... etc.) to the Internet Service Provider (ISP) who doesn’t know what your data contains. Then the ISP automatically returns the data, always encrypted, to the VPN server through the Internet. The data is then decrypted to reach their destination (the service or final site). Nobody can read your data and your anonymity is guaranteed by changing your IP address and location.
It’s still recommended to use HTTPS and other encryption protocols as much as possible.
A VPN is not only used to browse anonymously, companies often use VPN to place multiple geographical sites on the same LAN. Censorship, geolocation, blocked access to sites, the protection of its IP address are all other possible reasons and which are making the VPN necessary.
The VPN service can also be used to encrypt other protocols than HTTP, such as FTP (to transfer files) or IMAP (to access his e-mails).
The problem is again that the provider must be trusted if you want a guaranteed anonymity, as it’s the case for HideMyAss, NordVPN and ExpressVPN, three VPNs among the most recommended on the Internet.
But which one to choose?
Great question, I will try to provide you their main differences further down in the article to choose the one that is right for you, even if they are all good. They depend mainly on everyone's needs.
Know already that no matter the service:
You will be completely anonymous on the Internet, the traffic will be encrypted no matter where you are.
You will get free anonymous IP addresses in tens or even hundreds of countries.
The encryption standards are those used by governments.
All censored sites will no longer be for you.
All applications will be anonymous because all your connection will go through a tunnel (Linux, Android, Mac ... etc).
You have 30 days to test the services, if you are not satisfied, you are refunded.
Using a VPN is therefore a very good solution but it also has a cost.
A justified cost knowing all the other benefits of a VPN: it protects you more on a public Wi-Fi network to read your mails, to share private data, it helps you to improve your connection if your ISP limits flows (streaming, peer-to-peer), it allows you to unlock inaccessible content in your area, to counter censorship ... etc.
A VPN is thus not only used to visit blocked sites and to become anonymous, which makes it a good investment.

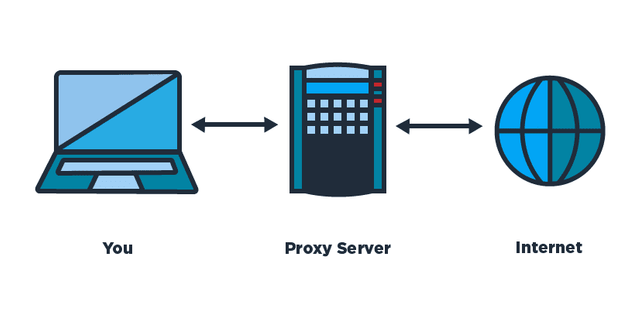
2. Second option (the bad one): use a proxy
A proxy server can connect to a site for you and then transfer the data. The visited site is not visited by you so it doesn’t know you.
Source
However, there is a problem with the data retransmission time. If you connect to an Indonesian proxy, you will certainly expect tens of additional seconds from your own connection, and that for each clicked link.
There are also several types of proxy servers: proxy servers called "elites" guarantee a more advanced anonymity while others still allow to find your IP address, and therefore find you (simply because these proxies in question share your IP address).
There are also web proxies: these are web sites that allow you to navigate for you and display the result directly to you without pre-setting.
WARNING: a lot of sites like Facebook using Ajax technology do not work with web proxies.
Even so, proxy does not guarantee 100% anonymity, it is possible to find from them your IP address on request, not necessarily from justice, and free proxy servers have a bad reputation because the owners could very well spy on your activities without you doubting it.
"If it's free, you're the product"

3. Third option: use the TOR network?

TOR (The Onion Router) is a global network of routers. The connection of an user passes through several computers in the world called the nodes.
Connections between nodes are encrypted, so it is "impossible" to find the original user.
The site that the user visits will only see the IP address of the last node.
TOR is distributed as free open source software and each user can become a node. TOR is however (very) slow since the connection goes through several nodes.
TOR was first recommended to be anonymous on the Internet, but you should know that TOR is full of crooks, black-hat-hackers and cyberterrorists hidden in the deep web, waiting to hack YOU. The cyberpolice use it to infiltrate criminal networks. And given the number of arrests and the number of malicious activities, we can wonder if TOR is really safe for anonymous surfing as individuals...
Nowadays a lot of "mirror" sites of TOR are created (onion.cab) making accessible the content you publish on the "deep web" outside of TOR (directly through Google).
In short, I don’t really recommend TOR for beginner.

Surfing anonymously in a cybercafe?
We often talk about connecting to a cybercafe or from a company computer to surf anonymously and prevent anyone from finding us.
This is an assertion which is not necessarily right because it should be assumed that no other spyware is placed on the computers in question. And of course, that no other program could allow to track you (including the logs connection). And that's without mention the cameras surveillance and other fingerprints left behind, even if there are extreme cases ... and then after all, what are you trying to do in this case?!?

Little conclusion:
We have seen that being anonymous on the Internet is not obvious and the ideal would already be to start with a VPN.
That said, we will push a little more the explanations:
The truth about logs!
Most VPNs record the real IP addresses of Internet users (at least those used to visit their site) for a certain period. This is not to track you but rather to respond to a serious problem and demand from the justice.
Because if you belong in an organization of cyberterrorists aiming to hack banks or whatever, there is still the chance that the VPN service will have to give your information if it has some and if the authorities come ask them.
It is also interesting to read the terms of use, because there are many VPNs (which I will not mention) to promise a 100% anonymous surfing while conditions say that the connection data are saved for an undetermined duration and disclosed to third-party services. HideMyAss deletes the logs every 2/3 months, NordVPN and ExpressVPN do not record logs (we will immediately talk about it).

A very efficient "no log" VPN
If you prefer to use a so-called "no logs" VPN service that does not record any information about you (100% anonymous surfing), you can look atNordVPN, or ExpressVPN. All the standards of a good VPN are there.
Between HideMyAss, NordVPN or ExpressVPN, which one to choose?
It is a question of preference depending on what you want to get, we can note some differences between the three:
- Do you prefer a high speed and a large network (HideMyAss or ExpressVPN), or rather an enhanced anonymity (NordVPN, ExpressVPN)?
- Do you prefer using the service on several devices like Android, iOS, Mac or Linux (NordVPN, ExpressVPN), or a cheaper service (NordVPN, HideMyAss)?

Does the VPN do everything?
Would you give your first and last name and your post address at an unknown site, even using one of the anonymity solutions we saw?
No, at least I do not think so. It seems logical.
In other words, if you go to your Facebook or to an other account with a VPN, your profile from the technical point of view will certainly be different (different IP address ... etc), but Facebook will know that it’s indeed you, because you are connected to your own account. This account on which your virtual identity is apparent (name, first name, address, photos ... etc).
More generally, if your browser, your cookies, or your online accounts remain unchanged before and after using a VPN ... you may not necessarily gain much privacy. The idea is to complement your use of a VPN with good practices such as the following:
Delete cookies (including sites that track you).
Hide your User Agent (several extensions available depending on your browser).
Do not publish your personal data voluntarily, do not bind them together (email alias), do not connect to usual accounts ... etc.
If a camera observes what you type on your keyboard or the sites you visit on the screen, your VPN becomes useless, that makes sense. Computer security is a set that works on multiple levels to protect.
Security therefore lies in complementarity of: user + antivirus + VPN + all the security measures (technical or not) that exist.

Thanks, very good read!
I just wrote this article, would you mind giving it a look? :)
https://steemit.com/security/@gaottantacinque/steemit-security-check-iframe-tricks#comments
Thank's man!
Nicely written, a brief information of current privacy condition. I have shown some few tricks for better anonymity If you want to check it out: https://steemit.com/cybersecurity/@fako/unorthodox-way-of-using-vpn-and-tor-networks-chains
I should check out the VPN soon.
Posted using Partiko Android