51% Attack Is Now Becoming Regular on the Blockchain.
Monacoin, bitcoin gold, zencash, verge and now, litecoin cash.
At least 5 cryptocurrencies have recently been hit with associate degree attack that wont to be a lot oftheoretical than actual, bushed the last month. In every case, attackers are ready to amass enough computing power to compromise these smaller networks, arrange their transactions and go off with voluminous greenbacks in an endeavor that is maybe the crypto equivalent of a bank heist.
More stunning, though, is also that supposed fifty one attacks ar a well-known and dangerouscryptocurrency attack vector.
While there are some instances of such attacks operating with success within the past, they haven't specifically been all that common. they have been thus rare, some technologists have gone as way onargue miners on bound larger blockchains would ne'er fall victim to 1. The antique (in crypto time) argument? It's too expensive and that they would not get all that abundant cash out of it.
But that does not appear to be the case any longer.
NYU computing scientist Joseph Bonneau free research last year featuring estimates of what proportioncash it might price to execute these attacks on prime blockchains by merely dealing power, instead ofshopping for all the instrumentation.
One conclusion he drew? These attacks were doubtless to extend. And, it seems he was right.
"Generally, the community thought this was a far off threat. i believed it had been abundant less distant and are attempting to warn of the chance," he told CoinDesk, adding:
"Even I did not assume it might begin happening this presently."
Inside the attacks
Stepping back, cryptocurrencies aim to unravel a long-standing computing issue referred to as the "double pay downside."
Essentially, while not making associate degree incentive for computers to watch and stop dangerousbehavior, electronic messaging networks were unable to act as cash systems. In short, they could notforestall somebody from outlay an equivalent piece of knowledge 5 or maybe one,000 times at once (without trusting a 3rd party to try and do all the dirty work).
That's the entire reason they work as they are doing, with miners (a term that denotes the machines necessary to run blockchain software) overwhelming electricity and ensuring no one's cash is obtainingtaken.
To make cash victimisation this attack vector, hackers want a number of items to be in situ. For one, associate degree aggressor cannot do something they require once they've racked up a majority of the hashing power. however they are able to double pay transactions underneath bound conditions.
It would not be to amass all this costly hashing power to double pay a $3 group action on a cup of low. associate degree aggressor can solely take pleasure in this investment if they are ready to steal thousands or maybe voluminous greenbacks.
As such, hackers have found varied clever ways that of constructing certain the conditions are excellent to form them more money. that is why attackers of monacoin, bitcoin gold, zencash and litecoin money have all targeted exchanges holding millions in cryptocurrency.
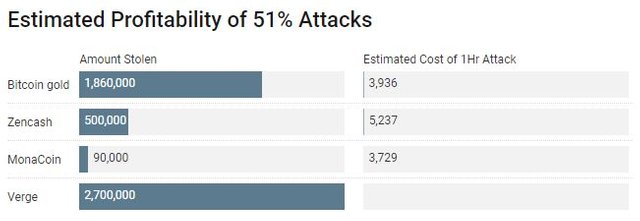
By amassing over half the network's hashing power, the bitcoin gold aggressor was ready to double pay terribly costly transactions sent to associate degree exchange.
Through 3 winning attacks of zencash (a lesser-known cryptocurrency that is a fork of a fork of privacy-minded Zcash), the aggressor was ready to break out with regarding over twenty one, zen (the zencash token) value overflow $500,000 at the time of writing.
Though, the attack on verge was a small amount totally different since the attacker exploited insecure rules to confuse the network into giving him or her cash. Though, it's clear the attacks targeted verge's lower protocol layer, researchers ar debating whether or not they technically represent fifty one attacks.
Small coins in danger
But, if these attacks were uncommon for such an extended time, why are we have a tendency to suddenly seeing a burst of them?
In voice communication with CoinDesk, researchers argued there's not one, clear reason. Rather, there variety of things that doubtless contributed. let's say, it's no coincidence smaller coins are those being attacked. Since they need attracted fewer miners, it's easier to shop for (or rent) the computing power necessary required to create up a majority share of the network.
Further, zencash co-creator Rob Viglione argued the increase of mining marketplaces, wherever users willeffectively rent mining hardware while not shopping for it, setting it up and running it, has created it easier, since attackers will use it to simply purchase plenty of mining power all right away, while not having to paythe time or cash to line up their own miners.
Meanwhile, it's big easier to execute attacks as these marketplaces have collected a lot of hashing power.
"Hackers ar currently realizing it is wont to attack networks," he said.
As an information purpose for this, somebody even erected a website Crypto51 showing however costlyit's to fifty one attack varied blockchains employing a mining marketplace (in this instance, one referred to as NiceHash). assaultive bytecoin, let's say, may cost a {little} as little as $719 to attack victimisation rented computing power.
"If your savings ar in a very coin, or the rest, that prices not up to $1 million each day to attack, you ought to rethink what you're doing," tweeted Cornell academician Emin Gün Sirer.
On the opposite hand, larger cryptocurrencies like bitcoin and ethereum ar more durable to fifty oneattack as a result of they are far larger, requiring a lot of hashing power than NiceHash has offered.
"Bitcoin is just too massive and there's not enough spare bitcoin mining capability sitting around to tug off the attack," Bonneau told CoinDesk.
But, whereas Crypto51 offers a rough estimate, ETH Zurich analysis Arthur Gervais argued to require the results with a grain of salt, since it "ignores" the initial prices of shopping for arduous and software system. "Thus, the calculations ar simplistic in my mind," he added.
The solution: a extended wait
Gervais any argues it's value golf shot these attacks into context. tho' a fifty one attack is probably the foremost far-famed cryptocurrency attack, it is not essentially the worst in his mind.
He pointed to different malicious bugs, like one found in zcoin, where, if exploited, a user would are ready to print as several zcoin as they might like. however fifty one attacks ar still perturbing since they will still be worthy typically, impacting exchanges or whoever happens to be within the center of attention of the aggressor.
"As associate degree trade, we've got to place associate degree finish to the current risk," Viglione aforesaid, inform to efforts on zencash to prevent this from happening once more.
Either way, a method for users or exchanges to form certain they are not defrauded is to solely settle forcash that is older, or has been buried by a lot of blocks of transactions, referred to as "confirmations." The a lot of confirmations there are, the more durable the funds ar to steal in a very fifty one attack.
Initially, exchanges wherever bitcoin gold was taken needed solely 5 confirmations, and also the aggressorwas ready to reverse all of them with their hashing power. In response to the attacks, they need upped the quantity of confirmations to fifty, that has with success blocked up the attacks, a minimum of for currently.
Because of this, developers and researchers contend larger blockchains with a lot of hashing power behind them ar safer since they need fewer confirmations.
As bitcoin enterpriser John Light put it:
"Remember this next time somebody tells you they use altcoins as a result of they are 'cheaper' to use."