COVA - A Security and Privacy Conscious Protocol

According to statistics, in 2017 alone a total of 22 zettabyte (ZB) of data was created (1 ZB = 1,000,000,000,000 gigabytes). However, out of all this large amount of created data only 1% is being utilized. One of the reason why only a small percentage is used is because of privacy. The moment data is made public the data owners expose their sensitive data and lose all control of its usage and distribution. So, in essence it is perfectly understandable that only a fraction of the potentially available data is actually being utilized. Giant companies like Google and Facebook make use of user data and machine learning algorithms to efficiently render services to its users and mind you they are currently using some fraction of this large data, now imagine if the whole data itself is used by this ML and AI techniques I believe the internet as a whole will become more interesting and effective. So now the big question is how can we utilized data and still protect its privacy.
A couple of weeks ago I came across COVA protocol a blockchain based protocols that will make user’s data smart, what this means is that data will become smart enough to retain it privacy even when it is being used, isn’t that fascinating. Here are example case for such kind of data.
- That these text messages can only be viewed after tonight.
- That a patient’s CT scan may be processed by an aggregate function and not rendered individually.
- That my credit card number may only be used once for a one-time charge. It will be erased from the server after the payment is completed.
- An ad or disclaimer has to be viewed before the rest of the content.
- and lot more
The example above illustrate a classic example of how data will behave using COVA protocol, it’s clearly obvious that data in these case are smart and protected so no need to start worrying about breaching privacy.
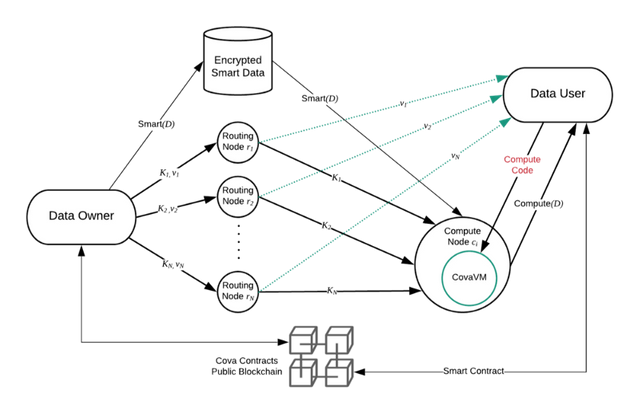
COVA protocol is a blockchain based protocol much like the internet protocol, it uses "Trusted Execution Environments (TEE)", TEE can be likened to an isolated environment that operates in parallel with the operating system and ensures security for the rich environment. It guarantees that data and code that is loaded inside the environment to be protected with respect to confidentiality and integrity. In more technical case TEE refers to the nodes that run on the chain and provide the high computational power that the chain needs to carryout it basic functions. It makes sure that any data that moves across these nodes will unreadable to the node owners and ensures that it privacy and security are protected. And also “Centrifuge” a Policy Specification Language (PSL) that specifies data usage policies in programming language and a Policy Enforcement Framework (PEF) that enforces the PSL through code. Finally, “CovaVM" a Policy Enforcement Framework (PEF) that enforces the policy written in Centrifuge. CovaVM is the counterpart of the Ethereum VM.
Want to know more about COVA check them out on: On their website: https://covalent.ai Or Read COVA’s white paper: https://github.com/covalent-hq/wiki/wiki You can also Follow COVA’s Official Telegram Group: https://t.me/covalentofficial
Follow COVA’s twitter: https://twitter.com/@covatoken
Follow COVA’s Medium: https://medium.com/@covatoken