Goldilock | Security system for digital assets

Starting from the reality that all information on the internet is vulnerable, a need for security for assets and digital information is created. The decision of a corporation to invest in cryptography will also depend on this premise.
Giants like Google and Microsoft begin to enter the cryptographic market and this creates a drag effect of smaller companies that are also managed in the same sector of work until they reach a massive influence.
This boom generates movement of investments, capital and digital assets in the market, which creates a focus of view for hackers.
The need for systems that guarantee the security of these assets is paramount to generate a market that is reliable for investors and with a fixed focus on development.
From this need is born, Goldilock.
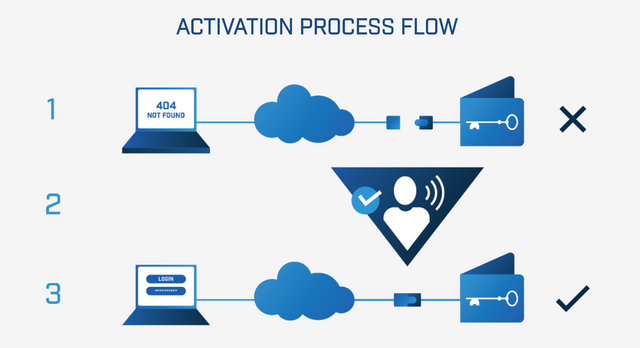
Goldilock is a security system for digital assets that allows users to protect them under encrypted and offline nodes until they want it.
To access digital assets, it must be done through a "Personal Device" that acts remotely with commands that do not use IP.
After the user makes the transactions the node is isolated in a network that is physically separated with a "Conceptual" air space of the entire internet. This measure of computer security is called "Airgap".
This security system guarantees the safeguarding of assets and digital information by remaining disconnected from the Internet, making a kind of intangible and invulnerable vault. This provides diverse applicabilities for natural and legal persons.
Goldilock - Natural People
Personal data, visa, passport, medical history, digital assets, cryptocurrencies, tenant documents, securities and movable and immovable property, inheritance, among many others.
Goldilock - Legal Entities
Constitutive acts, investments, customer information, product patents, securities and property titles, digital assets, cryptocurrencies, among others.
These applicabilities are necessary for people and institutions that need to have work information protected in one place but that can be accessible from the points that are necessary.
Goldilock - Benefits of cold and hot storage
Cold storage:
Advantage: While access to funds is closed, hacking is impossible.
Disadvantage: The user does not have the full time availability on their assets.
Hot storage:
Advantage: The user has full availability of their funds.
Disadvantage: While access is open there is a risk of hacking.
They are different scenarios and contrary to the storage. But, taking the advantages of both, the ideal storage that every person and institution needs is achieved.
This mix of benefits is what Goldilock offers to users through "Airgap" This computer security system works under a theory of isolation, offering users a prudential time to access their funds and then enters a period of inactivity so that hackers can not infiltrate.
Goldilock - Encourages massive cryptographic adoption
By gaining the confidence of large companies with security in the safeguarding of information and digital assets, mass adoption will be a domino effect. Lower-level companies will want to invest in cryptography. But not only is winning the trust, but is shown with efficiency to see that the system works and has applicability.
The refusal to invest in cryptography comes from the many capital piracies that have occurred and it is understandable that an institution does not have the confidence to adopt another type of economy even offering great benefits, because this type of situation can lead to bankruptcy or to a lesser extent. measure, to the loss of the most important customers.
Goldilock - NEO as a starting point
NeO is the starting point for Goldilock, and it does well, since NeO offers a great transaction speed of about 10,000 per second, making a difference to other platforms that work with POW.
In addition, NeO has plans with centralized entities, which seeks to open entry on services in terms of finance, security and public health, which are precisely the areas where the Goldilock system may have greater applicability.
Goldilock - LOCK Token
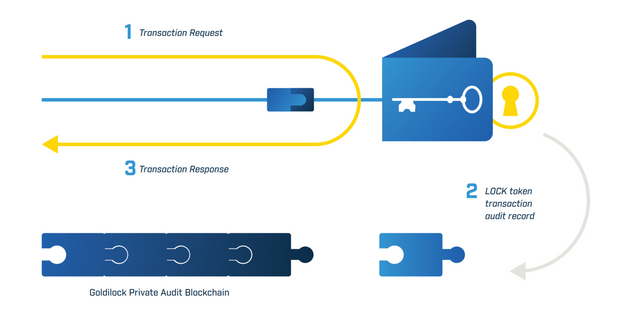
"LOCK is the utility token that will be used to provide a gateway for Goldilock services. The LOCK token is required to access the Goldilock Wallet. When the user logs into the Goldilock Wallet, the Wallet will query the NEO public Blockchain to confirm the user’s public key address owns a LOCK token. If the user’s public key address owns a LOCK token, then the Goldilock Wallet will launch in the user’s browser. When the user is granted access, the Wallet will write audit information to our own Private Audit Blockchain. These audit entries will ensure that every time your private key is brought online, this access is written to immutable storage that can be queried from the Goldilock Wallet. LOCK token allows Goldilock to provide users with a record of their node activity, while keeping user-owned data encrypted and locked away even from everyone including the Goldilock team."
For more information watch this short feature intro:
This CONTEST is sponsored by:
@originalworks
goldilocktwitter
goldilock2018
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
@originalworks