 pixabay.com
pixabay.com

RC4 algorithm is a symmetric key algorithm which processes the stream ciphershaped units or input of data, messages or information at one time. Unit or a byte of data in general or even bits (byte in RC4). This algorithm does not have to wait for a number of data input, messages or information before processing or adding additional bytes to encrypt. RC4 has an S-Box, S0, S1, ......, S255, which contains a permutation of the numbers 0 to 255. While the Vernam cipher algorithm is one of the classic cryptographic algorithms that are well known today. The second algorithm uses XOR encryption and decryption in doing so make it easier to merge or combination and Vernam cipher RC4.
# Vernam Cipher Encryption Process
The Vernam Cipher encryption algorithm is in the *pseudocode* form below:
* Step 1: Input Plaintext
* Step 2: Input Key
* Step 3: Change each character in Plaintext into the form *Ascii Code*
I=0
Jum = LEN(Plaintext)
For i=1 to jum
P(i) = Asc(substr(Plaintext, 1,i))
Next i
* Step 4: Change each character on the Key into the form *Ascii
Code*
I=0
Jum = LEN(Key)
For i=1 to jum
K(i) = Asc(substr(Key, 1,i))
Next i
* Step 5: Encrypt with formulas
I=0
Jum = LEN(PlainTeks)
For i=1 to jum
C(i) = P(i) XOR (K(i) // Weakness
Next i
* Step 6: Change the Ascii Ciphertext into character form
I=0
Jum = LEN(Ciphertext)
For i=1 to jum
Character_C(i) = chr(substr(C(i), 1,i))
Next i
# Vernam Cipher Decryption Process
The Vernam Cipher decryption algorithm is in the form of pseudocode below:
* Step 1: Input Ciphertext
* Step 2: Input Key
* Step 3: Change each character in the Ciphertext into the form *Ascii Code*
I=0
Jum = LEN(Ciphertext )
For i=1 to jum
C(i) = Asc(substr(Ciphertext , 1,i))
Next i
* Step 4: Change each character on the key into the form *Ascii Code*
I=0
Jum = LEN(Kunci)
For i=1 to jum
K(i) = Asc(substr(Key, 1,i))
Next i
* Step 5: Encrypt with formulas
I=0
Jum = LEN(Ciphertext)
For i=1 to jum
P(i) = C(i) XOR (K(i) // Weakness
Next i
* Step 6: Change Ascii Plaintext to character form
I=0
Jum = LEN(Plaintext )
For i=1 to jum
Character_P(i) = chr(substr(Plaintext ,1,i))
Next i
# Analysis of the Weakness of Vernam Cipher Cryptographic Algorithm
The weakness point is seen in the commented part in the *pseudocode*. The weakness of this algorithm lies in the use of XOR in encryption and decryption between plaintext and key.
P(i) = C(i) XOR K(i)
Where if it is assumed that A successfully intercepts 2 different Ciphertexts with the same key, A then XOR the two Ciphertexts, if it succeeds in knowing the plain text of the Ciphertext it will easily find another plaintext without needing to know the key circuit as shown below:
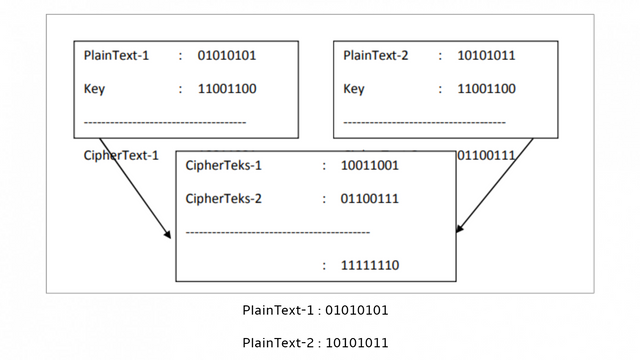 Figure 1. Example of XOR Results so that it gets Plaintext
Figure 1. Example of XOR Results so that it gets Plaintext
# Rivest Cipher 4 (RC4)
RC4 algorithm is a symmetric cryptographic algorithm. Called a symmetric cryptographic algorithm because it uses the same key to encrypt or decrypt a message, data, or information. Encryption key is obtained from a 256 bit state-array (KSA) which is initialized with a separate key with a length of 1-256 bits. After that, the state-array will be scrambled back and processed to produce an encryption key that will be XORed with plaintext or ciphertext. In general, RC4 algorithm is divided into two, state-array initialization and the encryption and encryption key generation. The algorithm of RC-4 Encryption is as follows:
* Step 1:
S-Box Initialization (Array S)
Jum = Len(Key)
i = 0
j = 0
For y=1 to Jum
j = (j + S[i] + K [i mod jum]) mod jum
Swap (S[i],S[j])
Next y
* Step 2:
Perform S-Box Randomization
Jum = Len(Key)
i = 0
j = 0
For y=1 to Jum
i = (i + 1) mod Jum
j = (j + S[i]) mod Jum
swap (S[i],S[j])
Key(y) = S[(S[i]+S[j]) mod jum]
Next y
* Step 3 :
Encrypt
Jum = Long(PlainText)
i = 0
j = 0
For y=1 to Jum
C(y) = Biner(P[y]) XOR Biner(Key[y]) //
Next y
And to do Decryption then do the steps as follows:
* Step 1 :
S-Box Initialization (Array S)
Jum = Len(Key)
i = 0
j = 0
For y=1 to Jum
j = (j + S[i] + K [i mod jum]) mod jum
Swap (S[i],S[j])
Next y
* Step 2 :
Perform S-Box Randomization
Jum = Len(Key)
i = 0
j = 0
For y=1 to Jum
i = (i + 1) mod Jum
j = (j + S[i]) mod Jum
swap (S[i],S[j])
Key(y) = S[(S[i]+S[j]) mod jum]
Next y
* Step 3 :
Encrypt
Jum = Long(PlainText)
i = 0
j = 0
For y=1 to Jum
P(y) = Biner(C[y]) XOR Biner(Key[y]) //
Next y
# Analysis of the Weakness of Rivest Cipher Cryptography Algorithm
As for the weaknesses of RC-4 seen in the box in psedocode above, this cryptographic algorithm uses XOR in performing operations on encryption and decryption. If it is assumed that A successfully intercepts 2 different text ciphers with the same key, A then XOR the second Cipher text, if it succeeds in knowing the plain text of the Cipher text it will easily find another plaintext without knowing the key circuit as shown below this :
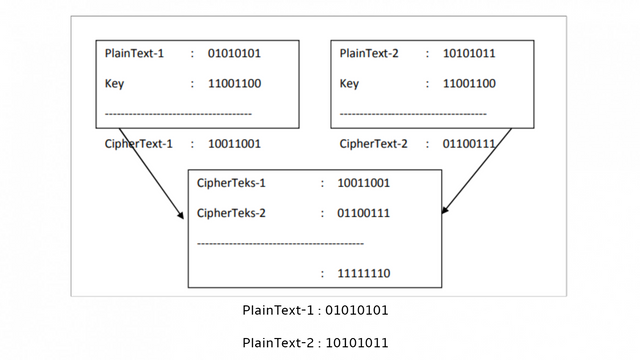 Figure 2. Example of XOR results so that it gets Plain
Figure 2. Example of XOR results so that it gets Plain
To be continued ...












Thanks for using eSteem!
Your post has been voted as a part of eSteem encouragement program. Keep up the good work! Install Android, iOS Mobile app or Windows, Mac, Linux Surfer app, if you haven't already!
Learn more: https://esteem.app
Join our discord: https://discord.gg/8eHupPq
Congratulations @alfarisi! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOPDo not miss the last post from @steemitboard: