2018 Duo Trusted Access Report
Duo Security Released their 2018 Trusted Access Report on May 23rd. You can download the report here. The report is based off of analysis of Duo's 10.7 million devices and half a billion authentications per month to over 800,000 applications, and it contains some very interesting insights.
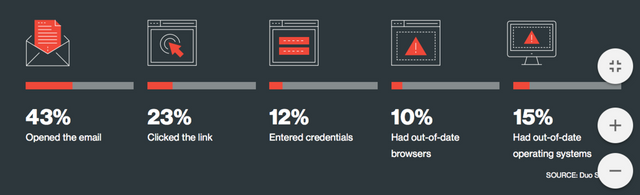
The report is broken down into two main categories: User Behavior and Device Health. In the User Behavior section, the biggest takeaway is that more people than ever are working remotely. Whether that means working from home, from a coffee shop, from a business partner's location, or on an airplane, people are connecting to corporate resources from many different locations and networks. This means that people are potentially connecting to unsecured WiFi networks and other untrusted networks which introduce new points of entry into corporate systems. Another key point is that Phishing isn't going away, and is in fact getting worse. In their studies, Duo found that 62% of Phishing campaigns were able to extract at least one set of user credentials. The below graphic shows some other stats from Duo's simulated Phishing campaigns.
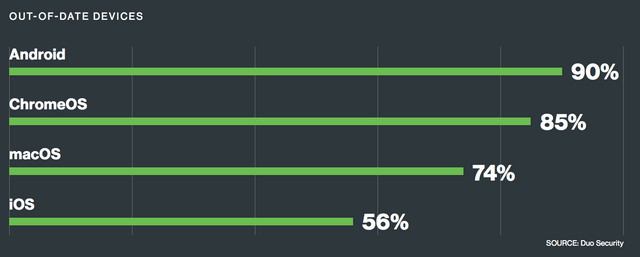
On the Device Health front, the main message is to update your devices. As they described in the Phishing section, Phishing campaigns not only target user behavior, but they generally target vulnerabilities in out of date operating systems, browsers, and email software. Keeping devices up to date is the simplest method to stay safe on the intewebs. Duo's findings show that MacOS and IOS devices are typically the most up to date, while Android devices lag far behind.
In summary, as people become more mobile, deploying some form of multi-factor authentication for accessing corporate resources, and especially cloud-based resources, is more important than ever. It's relatively trivial to compromise user credentials, so having a 2nd factor of authentication is absolutely critical. Many cloud applications offer this functionality for free. Check out twofactorauth.org to see if the cloud applications that you use, such as your bank, offer 2FA, and if they don't you can use the simple tool on twofactorauth.org to tweet out to them asking why it isn't supported. On the corporate side, all reputable firewall manufacturers will offer their own MFA solutions for VPN as well as integrations with 3rd party MFA solutions, so you really have no excuse not to protect yourself.
Hi, Nice to meet you and Upvoted you :) !
:
胜利者往往是从坚持最后五分钟的时间中得来成功。——牛顿
I just downvoted the comment by @ustd
@ustd - You clearly realize that "nice to meet","nice to meet you","to meet you" is considered to be spam since I've replied to you 127 times before so I just gave your comment a 100% downvote*.
@sendingtime - You can remove this comment and everyone can whitelist me from appearing in future posts.
*If you continue posting in this way, I will continue flagging and the weight of my downvote will increase each time I reply until you stop. Please reply if my algorithm is mistaken.