Be Prepared: How To Manage Your Digital Assets When You're Gone.
The purpose of this guide is to let you know how to manage your digital assets today before you depart to a better place. I know this is a hard subject to discuss and that it most likely will cause tension. So please read carefully. In non-crypto related digital-death stuff, I suggest you read Vered Shavit's guides and understand. In crypto related stuff, we need to apply a different kind of method because of some differences between password management, digital inheritance and money. Also, the methods I suggest today may not be relevant in two or three years. They are current best practices and they will change over time. Keep up with the changes in tech. Fortune discussed this theoretical issue. Also, while this text deals with security and privacy, it is not meant to be a guide on how to secure. Some of the solutions here are over simplified.
First, let's understand the considerations. Our discussion will be on how to manage your assets after you've departed from this world. This means that first we need to map the different assets we want to manage (we assume all of them are cryptocurrency based). Our purpose is to first analyse and understand how we want to distribute these assets and control them when we depart. We need to take into consideration different inheritance taxes globally, and to check which of our beneficiaries will need to pay taxes; we also need to decide how will we let our beneficiaries know that they are entitled to these assets. This is the first problem. Meaning, usually, when you die, a will provided, or the law states how to distribute your assets. This means you go to the bank, and if there's an account then the bank just sends the beneficiaries their part of the balance.

In a decentralized world this just won't happen. There is not "bitcoin ltd" that you can approach and give them an account number. Without holding the keys to a specific bitcoin wallet, you cannot just go and claim the funds.
So, you first need to prepare a spreadsheet with all your assets (without keys) to let your kin now what will be left after you die. This is the first stage. This list should remain updated. Now, if you're willing to lose some assets, you don't have to update it daily, but without updating this, no one will know what he is expecting to receive.
After we've mapped out assets, the next thing to do is to see how do we control these assets. This could be divided to several methods: (1) exchanges, where we have usernames, password and a second-factor authenticator; (2) web-wallets, where we have usernames, passwords and a second-factor authenticator; (3) hardware wallets, that have a PIN code, and a paper backup; (4) paper wallets.
Back-up your second-factor authenticator. I cannot emphasise this enough. If access to your mobile phone is required in order to open your exchange account or web-wallet, this means that you need to make sure that a backup of that phone exists, or that you have another form of authentication. For example, I use my ledger-nano as a multi factor authenticator for my accounts. but, I also have a backup phone that receives codes, as well as an authenticator application. This means that if I want to log in, the first and best option is to connect my Ledger. If that's impossible, my phone has the app, and if that's unavailable, then another phone gets a text message. This means that only if all these three devices fail, I'll have to resort to my printed backup codes.
Make sure your passwords are backed up. If you want to give someone access to your exchanges, you will have to give them a password. This could be either the master password to your laptop or password manager application, or a full list of all your passwords. This has risks, that we'll take into consideration in the next part. But first, mapping all your passwords is critical.
Make sure your cold storage has backups. This means that you need to ensure that you have the seed (24-word phrase) for all your paper wallets. Now again, this has risks. We'll take them into consideration in the next part, but make sure you have them somewhere (not on an electronic device).

Second, let's understand the risks. Well, after we've mapped our means and tools to access all our accounts and assets, we need to manage the risks here. In a regular situation, we just provide our lawyer with the list of bank accounts, apartments and safe deposit boxes. Why is that? well, that's because we can't trust them. Some lawyers, not all of them, keep the funds deposited in escrow and use them. This is also a problem, because securing these keys with a lawyer is even harder than securing them with a tech-savvy user. Just ask your lawyer where does he keep his passwords, and you'll get the answer that they are all stored neatly in a sticky-note attached to his screen.
So we can't just give away all our keys and another person. That's insecure, and provides malicious attackers more incentives. If I know that X is a respected lawyer, and that people provide him with their keys and that he keeps them in his safe, then, well... I can just invest money in breaking into his safe.
So, how do we manage and understand the risks? Let's start with second factor authentication. During the last months we've seen that SIM jacking is a thing. Meaning, that hackers attempt and succeed in defrauding your phone operator to move your number to their SIM card and steal your number. This means that if you use text messages as an authentication, it is not as secure as you would like it to be. So, this means that the risk of SIM jacking is one of the risks of using a phone number to authenticate your accounts.
Also, password managers have inherent risks. Some browser-based managers are prone to auto-fill requirements, some are hard to restore if you lose access to your accounts, or use your email as a recovery option, meaning that if someone has access to your email they have access to all your passwords.
Now, keeping your wallet recovery seed in a safe is also risky. This means that the security of your assets is only as good as your $100 safe. This is called the "five dollar wrench attack vector" and means that if someone knows you, and knows that you hold funds, they'll hit you with a blunt object until you give them your recovery seed. This means that we need to split the keys in a different way to avoid keeping one copy of it in a central place.
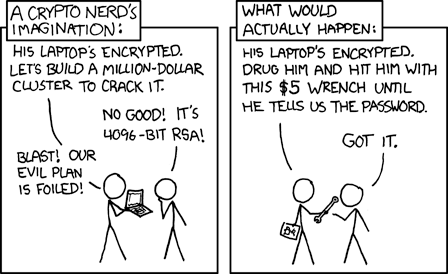
(cc-by-sa xkcd)
Third, we understand the limitations of technology. So, the first thing I learned from Meni Rosenfeld was to implement (an over simplified version of) Adi Shamir's Secret Sharing when distributing keys. This means that, in theory, we split our assets (mostly keys, but also passwords) into N+1 parts, that each need only N parts to operate. This means that if we have a 4-word recovery seed "correct horse battery staple" and we want to distribute it between three people, we do the following:
A 123
B 124
C 234
(pardon me if I got the math wrong here)
This means that each pair could operate the wallet, but no individual person could. In this method, we split the key four ways and give each person 75% of the key. This means that even if one person is compromised, then there is no apparent risk of losing all funds. This also means that less drastic measures could be made to secure the keys. That's, well, because even if someone steals these keys he can't do anything with them (he'll need a lot more computing power to guess the rest). Now, I suggest that we use more than three custodians, and more than four words, but you do get my point, hopefully.
The problem is that this technology is limited. It means that you do need to manage your keys. And if, for example, you'll need to replace your wallet's address, you will still need to replace the keys.
Also, generating these keys and storing them outside a computer is not the easiest thing to do. You need to hand-write them (or use a cryptosteel) and hand them over.
Also, this only works when you have the keys or passwords. In some cases, you use biometrics or a phone number as an authentication. What will you do then? In most cases, you will need a backup.
Fourth, we apply this. You will need to find people you trust with your assets. Even though you give each of them only a part of your keys, then could organize and gang up to steal all your funds. This also means that you either need to find people who are unfamiliar with each other (for example, your lawyer, your brother, a co-worker and a friend from school) and give each of them a part, or you will need to find your beneficiaries and train them on how to use this. Each of them should get a list of the "safe words" or passwords, and they should receive training on how to recover your accounts.
You should do a recovery dry run to make sure that they will access to your assets when you pass away, and make sure that each of them can keep their part of the asset in a secure location.
Now, I suggest you update this procedure once every year or two. Technology improves constantly; security improves, and we discover new vulnerabilities. Don't be over-confident with your assets.
Great advice. With some sites that require SMS 2FA, I've found that using Google Voice works (Although some sites deny Google voice numbers). If you do this, keep in mind that your 2FA is now only as secure as your Google account. For some this might be an acceptable tradeoff to trusting help desk techs at a cellular provider.
This post was spotted by @theluvbug and has received a 100% upvote and a resteem.
If you would like to possibly receive future support from @theluvbug
then please make use of the #theluvbug tag.
Spreading the STEEMIT LOVE with upvotes and resteems of AWESOME Steemit content. Use #theluvbug to get my attention :)
In Proud Collaboration with @steemitbloggers
and their founder @jaynie
interested in joining the Steemit Bloggers Community?
What happens when your attorney retires to Mexico, your brother dies, and your friend from college that nobody else knows changes his phone number and email address? Yikes. Great article with lots of good thoughts, and i loved reading it. seems like there are still plenty of opportunities for that money to evaporate if one or two requisite elements aren't quite there