📌 a BlockChain Learning Blog # S3E1 | 🚀 CryptoGraphy 101
Symmetric and Asymmetric cryptography and the science behind cryptocurrencies cryptography.
Cryptocurrencies like Bitcoin and Ethereum use a peer-to-peer decentralized system to conduct transactions. Since the entire process is online, there are fears that the transactions maybe volatile and hackable in this open network uses cryptography to make their transactions extremely secure.
What is Cryptography?
Cryptography is a method of using advanced mathematical principles in storing and transmitting data in a particular form so that only those, for whom it is intended for, can read and process it.
In modern technology, there are three forms of encryption that are widely used, symmetric cryptography, asymmetric cryptography, and hashing.
Private Key Crypto Gharphy
• Also knows as Symmetric key cryptography
• Use the same key during encryption and decryption of the message.
• Where we need to share the key with receivers
Alice generates the CypherText using shared private key
CypherText = Encryption (Message, Private Key)
Bob decrypt the CypherText using shared private key
Message = Decryption (CypherText, Private Key)
Public Key Crypto Graphy
• Also known as asymmetric key cryptography
• We use the key pair where message is encrypt using Public of receiver
• Which only receiver can decrypt using his private keys
• Receiver can decrypt the message without knowing sender's private key.
Alice generates the CypherText using Bob’s public key
CypherText = Encryption (Message, Bob’s Public Key)
Bob decrypt the CypherText using his own private key
Message = Decryption (CypherText, Bob’s Private Key)
POPULAR ALGORITHMS
AES - AES is the "gold standard" when it comes to symmetric key encryption, and is recommended for most use cases, with a key size of 256 bits. Learn more about AES.*
PGP - PGP is the most popular public key encryption algorithm. Learn more about PGP.
In the above manner Both Alice and Bob were able to exchange message securely, But apart from this we can also use asymmetric key cryptography where the recipients needs to validate of source of message and here the another aspect of Public Key Cryptography comes into picture knows as Digital Signature..
Digital Signatures
One of the most important cryptographical tools that are used in cryptocurrency is the concept of signatures. It is a kind of digital code which mimics our real life signature to authenticate the existence of digital entity. What is a signature in real life and what are its properties?
Provide verification : The signature should be able to verify that it is you who actually signed the paper.
Non-forgeable : No one else should be able to forge and copy your signature.
Non-repudiation : If you have signed something with your signature, then you should not be able to take it back or claim that someone else has done it instead of you.
In real world signature can be forged and it is very hard to detect. In digital world to maintain above mentioned properties, Cryptography gives us a solution to this by means of “digital signatures” which is done via the use of “keys”.
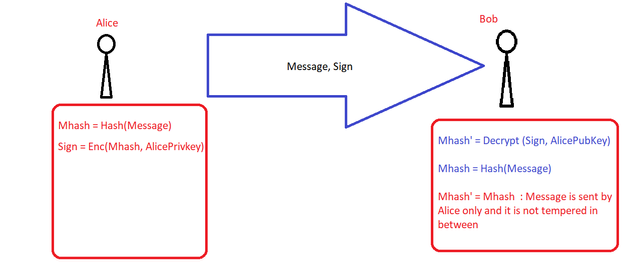
In this scenario Alice will Create a message Hash from original message Mhash = Hash Function (Message)
She will used Encrypt message hash using her private keys Function i.e. DigitalSig = FunctionEnc( Mhash, Alice Private Key)
Now she will send original Message and DigitalSig to Bob
Bob will Decrypt the Digital Sig using decryption function .i.e. Mhash' = (DigitalSig, Alice Public Key)
Now Bob will read the message but need to make sure that it must not be tempered, so he will use the Hash function and generate message hash Mhash = HashFunction(Message)
Now Bob will comare Mhash with Mhash' If both are equal then Bob can be sure that message has been sent by Alice only and has not been tempered.
And on the same principle we do make use of digital signature to authenticate the source of message in distributed environment.
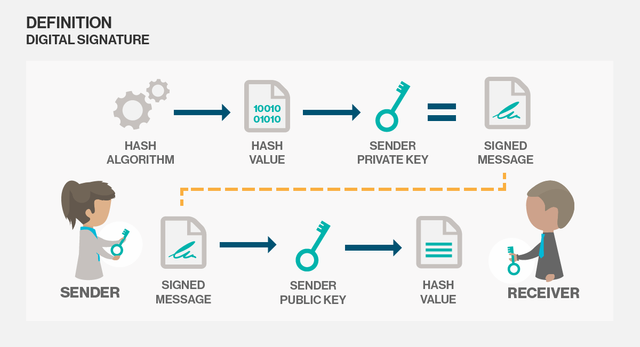
Kindly the a simply explained illustration on this concept
References : Blockgeeks
To view more kindly follow my blog https://steemit.com/@devrajsinghrawat
Thank you in advance for your comments...
Sign up nad Earn Free Bitcoin for solving simple tasks at Earn
Mannabase is an online platform for the world’s first Universal Basic Income cryptocurrency. You are also welcome! https://www.mannabase.com/?ref=e7e72550c8
Sign up to best Crypto to Crypto Exchanegs Binance Signup & KuCoin Signup
⚡ Best part about Kucoin Exchange is KuCoin Bonus ⚡
⚡ All your RESTEEM's always are much appreciated here, and always noticed ⚡
Stay Tuned & Keep Steeming,
Cheers
Interesting read
Thanks for the kind words
Thanks for resteem! appreciate it
Welcome!
@devrajsinghrawat, I'm interested in the same topic as you, let's spin it together. I signed on to you, I hope you'll sign up for me. Always glad to meet new people!
Dear @surikowstepanuk I visited your wall but can't find any post on it! have you not yet started blogging
Congratulations @devrajsinghrawat! You have completed the following achievement on Steemit and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOP