Hackers hijack - Hackers attack hits Australian government websites. Hackers used Australian government websites to mine cryptocurrency
Hackers hijack government websites to mine crypto-cash

Hackers used plug-in to force computers to secretly mine cryptocurrency.
A progression of Australian government websites, including the Victorian parliament’s, have been traded off by malware that forces visitors’ computers to secretly mine cryptocurrency, as part of a worldwide security breach. The process, known as cryptojacking, forces a user’s computer to mine cryptocurrency without their permission, generating profits for the hacker. Government sites were tainted with the malware on Sunday after a program module made by an outsider was bargained. Thousands of sites, including the UK’s National Health Service, and the UK’s own data protection watchdog, were affected.

In Australia the cryptojacking attack hit the official website of the Victorian parliament, the Queensland Civil and Administrative Tribunal, the Queensland ombudsman, the Queensland Community Legal Center homepage, and the Queensland legislation website, which lists all of the state’s acts and bills.
UK security researcher Scott Helme discovered the malicious software (Twitter)
More than 4,000 websites may have fallen victim to crypto-jacking — when computers are secretly made to mine cryptocurrency.
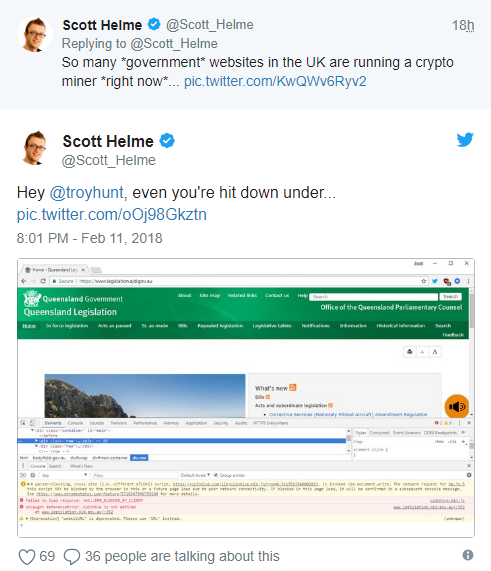
UK security researcher Scott Helme discovered the malicious software on Sunday, which he said was "definitely mining". The compromised website plug-in responsible has now been taken offline. Locally, websites that appear to have been affected include the Queensland Government's legislation website, the Queensland Civil and Administrative Tribunal and the Victorian Parliament.
In the UK, websites run by the National Health System, the UK's Student Loans Company and the Northern Powergrid were also impacted.
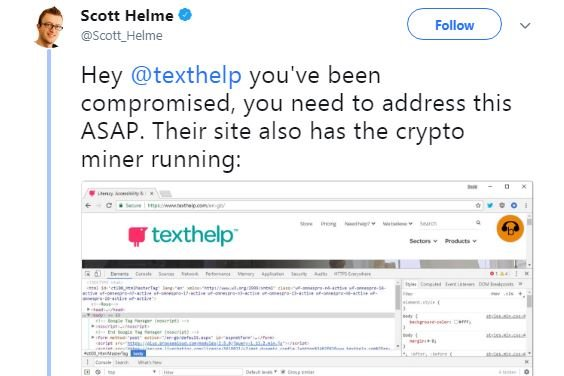
Mr Helme said he found the compromised JavaScript file on Sunday morning after a friend's anti-virus program set off an alert on the site of the UK Information Commissioner's Office. He found the malicious script and traced it back to its source: a website plug-in called Browsealoud, which helps people with low vision, dyslexia and low literacy access the internet.
"If you want to load a crypto miner on 1,000+ websites you don't attack 1,000+ websites, you attack the 1 website that they all load content from," Mr Helme wrote on his blog.

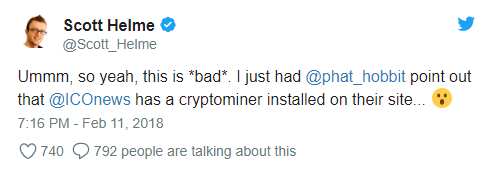
Hackers exploited a vulnerability in the popular browser plug-in Browsealoud, a program that converts website text to audio for visually impaired users. The makers of Browsealoud, Texthelp, confirmed that hackers inserted a script known as Coinhive into their software. Coinhive hijacks the processing power of a user’s computer to mine the cryptocurrency Monero.
On Monday morning, Texthelp took the Browsealoud plugin offline, which meant that new visitors to the affected sites would no longer load the cryptojacking script.
The situation could have been much worse
Mr Helme said using the same technique, malicious actors could have injected a range of malware into the websites. For example, they could have installed a keylogger that tracks people entering usernames and passwords, a malicious software update or a virus.
"At this point, the attacker is limited by their imagination. Right now, the worst-case scenario is you probably made some money for a criminal gang." he said.
Mr Hunt agreed the incident was a wakeup call.
There are ways of mitigating the risk. For example, he suggested, ensuring that scripts are only run if they look a certain way or only loading scripts from certain locations. "In fairness, [the affected websites] are not out of step with the industry," Mr Hunt said. "Websites in general have to get more serious about what they will trust to run." The UK National Cyber Security Centre said it was investigating the incident:
"At this stage there is nothing to suggest that members of the public are at risk."
Helme documented the attack on his website, while Texthelp said an investigation was under way.
“The company has examined the affected file thoroughly and can confirm that it did not redirect any data, it simply used the computers’ CPUs to attempt to generate cryptocurrency,” it said. “The exploit was active for a period of four hours on Sunday. The Browsealoud service has been temporarily taken offline and the security breach has already been addressed, however Browsealoud will remain offline until Tuesday 12.00 GMT.”
The Queensland Civil and Administrative Tribunal said it has disabled the Browsealoud plug-in on their website. The Queensland Government, the Victorian Parliament and the Australian Cyber Security Centre have been contacted for comment.
Source/References:
ABC News
The Guardian
Like what you've read?
Don't forget to Upvote & Follow.
Follow @geek.phoenix
