Crypto Academy Season 3 (Week 2) - Homework Post for @pelon53 [Hash and Cryptography]
On this occasion I will try to answer questions from the homework given by professor @pelon53, as for this week's class related to Hash and cryptography, well I will try to answer some of the questions given in this week's homework.
1. Explain what does the resistance to collision mean? And what does resistance to preimage mean?
Resistance to Collision
Resistance to Preimage
Resistance to Second Preimage
2. Use tronscan and etherscan to verify the hash of the last block and the hash of that transaction. Screenshot is required for checking
Tronscan
- Visit the tronscan website; https://tronscan.org/#/. there you can see several options to get the information contained in the tronscan such as Blocks and Transactions
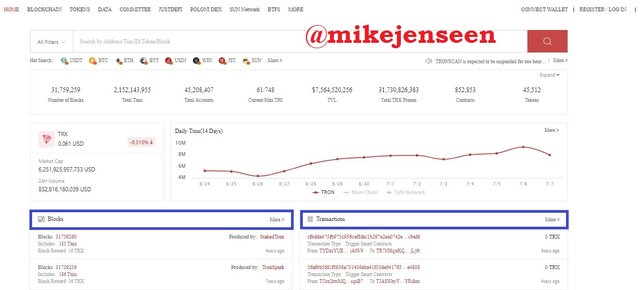
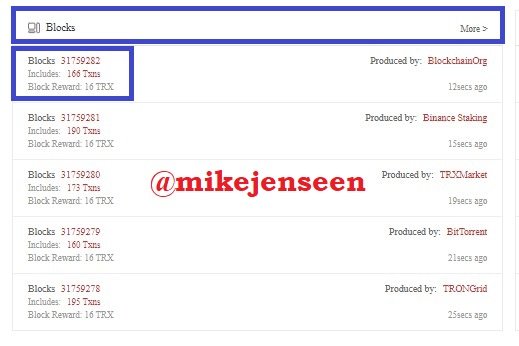
- Then select the last block to view block information.
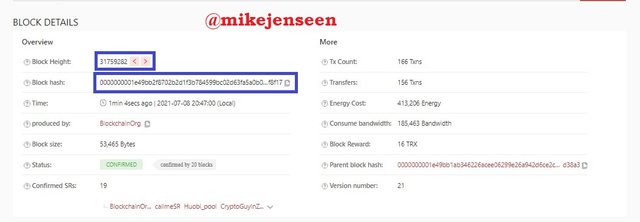
- There you will get information about the block. Block Height : 31759282, and Block Hash : 0000000001e49bb2f8702b2d1f3b784599bc02d63fa5a0b04d7e565f7d2f8f17
- Then return to the main page to select the last transaction
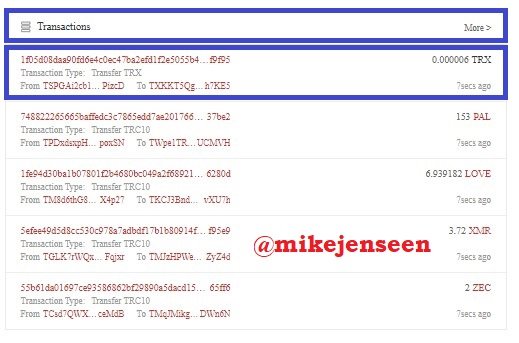
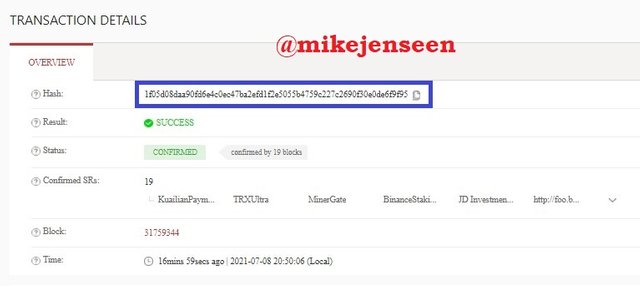
- After that you can see the latest information. Hash : 1f05d08daa90fd6e4c0ec47ba2efd1f2e5055b4759c227c2690f30e0de6f9f95
Etherscan
- Visit the official website of Etherscan ; https://etherscan.io/. there you can see several options to get the information contained in etherscan such as Latest Blocks and Latest Transaction
- Then open Latest Blocks.
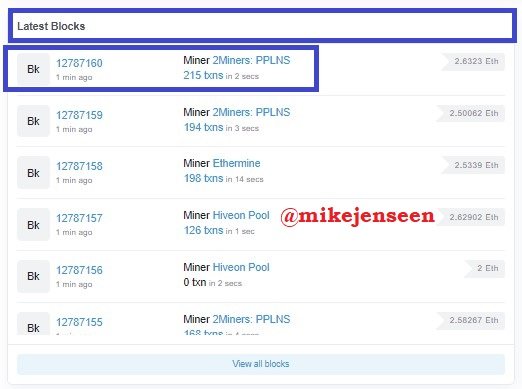
- then you will get block information. Block Height : 12787160
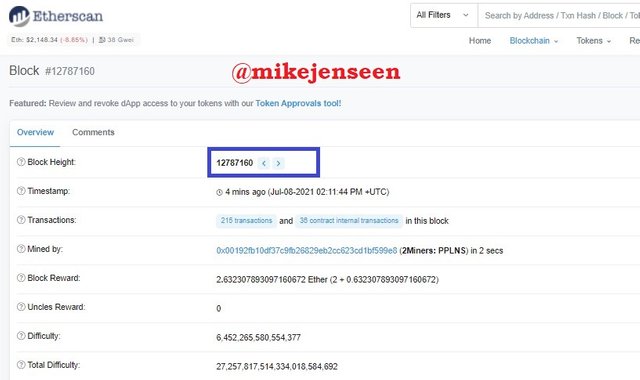
- Then scroll down click to see more, and Hash : 0x291a7c19d6fbcd34c49aa57cdd22c472617ebd038b8ac77c4b936fe01d4cfff0
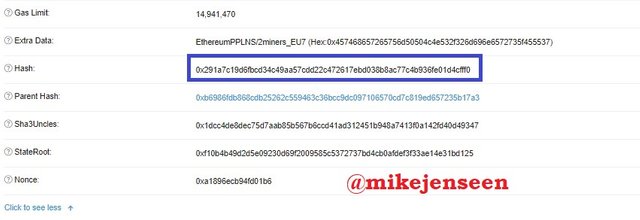
- Then return to the beginning to be able to select the last transaction
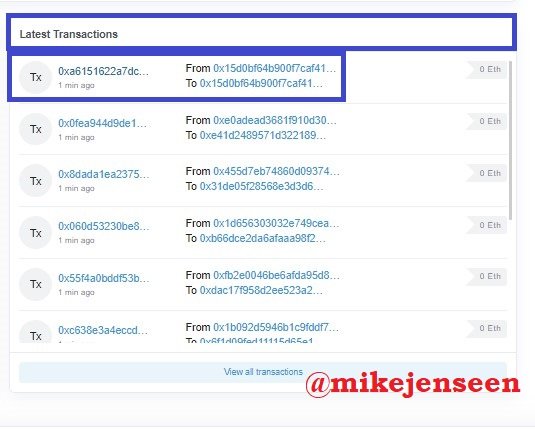
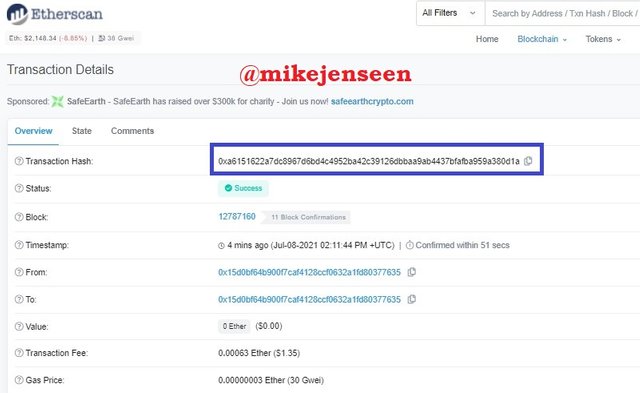
- Then you will get the last transaction details. Transaction Hash: 0xa6151622a7dc8967d6bd4c4952ba42c39126dbbaa9ab4437bfafba959a380d1a
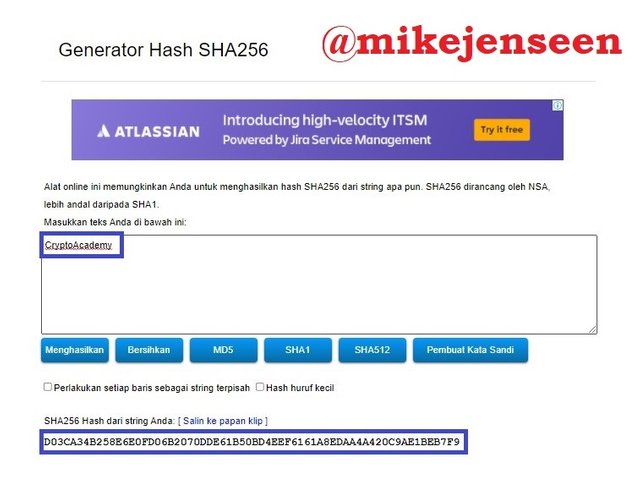
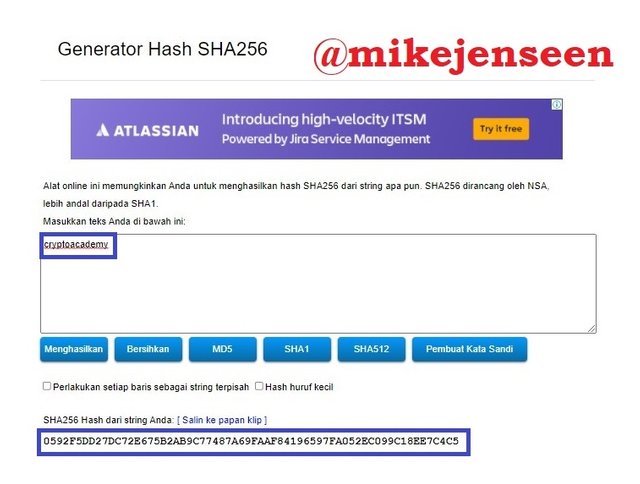
3. Generate the hash using SHA-256, from the word CryptoAcademy and from cryptoacademy. Screenshot required. Do you see any difference between the two words? Explain
The first step is to find the hashes of the words "CryptoAcademy" and "cryptoacademy" using SHA-256. visit the web address https://passwordsgenerator.net/sha256-hash-generator/.
First let's try to enter "CryptoAcademy". it will generate Hash: D03CA34B258E6E0FD06B2070DDE61B50BD4EEF6161A8EDAA4A420C9AE1BEB7F9
- Second, let's try entering "cryptoacademy". it will generate Hash: 0592F5DD27DC72E675B2AB9C77487A69FAAF84196597FA052EC099C18EE7C4C5
4. Explain the difference between hash and cryptography
As for some of the differences between Hash and cryptography, I'll try to break it down.
Hash
Hash is able to make information into a unique algorithm so that it cannot find the input information from the output (Hash).
Hash does not require a password.
Hash protects an information that is inputted through the output resulting in a unique algorithm that cannot be cracked.
Hash have the same length of an algorithm
Hash cannot be repeated or changed.
Hash a good level of security because the hash rarely has the same output from different inputs so it is very difficult to hack.
Cryptography
cryptography is able to perform the encryption and decryption process
Cryptography requires a password
Information is very confidential so it cannot be known by foreigners who are not involved in the transaction process
Cryptography has a very variable length of data.
Cryptography can be repeated to find the initial input.
Cryptography has a good level of security because it prioritizes user privacy in terms of maintaining various user information when making transactions.
Although from a functional point of view, hash and cryptography have some differences, hash and cryptography both play a very important role in maintaining the security of the blockchain system.
Conclusion
Thanks.......


Gracias por participar en Steemit Crypto Academy Season 3:
Espero seguir leyendo tus publicaciones.
En la pregunta 2 no coincide el bloque con el hash de ese bloque y la transacción de ese mismo bloque, en tronscan. 31759282 y 31759344.
Buen trabajo, espero seguir viendo mejorías en tus tareas.
Recomendaciones:
Calificación: 8.8