BUGLAB Token Review

INVEST NOW at https://buglab.io/
What is Buglab?
Buglab is a Ethereum-based platform that connects companies with a global network of expert cybersecurity researchers.
At the center of our ecosystem, there are two programs - the buglab contest and Vigilante Protocol, helping companies all over the world to discover and fix vulnerabilities on their digital solutions or assets.
What are BGL Tokens?
A token on the Ethereum blockchain is a digital asset that is held inside a token contract, in trust for a wallet address.
The buglab token, identified as BGL, is based on the ERC20 standard for blockchain tokens.
BGL tokens are required for all transactions in the buglab ecosystem, from ordering a contest to rewarding pentesters and whitehats.
Who is Buglab for?
The Cybersecurity Market
Impacts on Return on Investment (ROI) are difficult to quantify, so it takes time for companies to recognize the need for cybersecurity services.
For all-too-many enterprises, as well as individuals with any digital assets on their websites (content included), it often takes a breach into their system before they take action to shore up security
Meanwhile, the victims of cyber attacks rarely advertise that they have been targets, unless they must, and data vulnerabilities are rarely first priority as product gets rushed to market, so it is difficult, if not impossible, to get exhaustive statistics about cyberattacks details, including their frequency or their impact on ROI. However, one aspect is absolutely certain: the trend is decidedly on the rise, with some widely-known geopolitical impacts.
THE CYBERSECURITY MARKET
A standout case is that of the 2016 U.S. presidential election campaign, when a massive email leak cast a shadow over the Democratic party in July 2016. Sen. Hillary Clinton’s campaign was hit by a large-scale cyberattack that not only put the Democratic party’s electoral strategy in peril, but also shaped the future of American politics. At that time Reuters reported that a “computer network used by Democratic presidential nominee Hillary Clinton’s campaign was hacked as part of a broad cyber attack on Democratic political organizations.” The article went on to say that the attack “follows two other hacks on the Democratic National Committee, or DNC, and the party’s fundraising committee for candidates for the U.S. House of Representatives.”
Blockchain Security
The method offered by Buglab deploys expertise and smart contracts across the blockchain.
A blockchain is a thread of digital records across which different types of data are stored. Together, these distributed (or decentralized) records make up a database similar to the pages of a large ledger book. These virtual ledgers are hosted across many servers, which helps verify and authenticate any given transaction. It is an intense numerical process, across many machines hosted by countless participants, or miners. See also Advantages of Using the Blockchain to Reshape Pentesting.
Methods of Fighting Cybercrime
Traditional options for fighting cybercrime are not feasible for small businesses and organizations. The cost of two common strategies outlined here rapidly becomes out of reach for all but large enterprises.
Penetration tests performed by a cybersecurity consulting firm:
Requires that clients pay for the service in terms of total billable hours, regardless of the test results. The majority of penetration tests performed by consulting firms are done by one, maybe two pentesters. This means that the client is only able to take advantage of the methodology and skillset of two consultants.
Bug Bounty challenges:
Information security researchers are paid on a per-vulnerability-uncovered basis. Companies often end up getting charged to fix issues not entirely consequential to their revenue or customers. This is described in more detail in the next section.
The Buglab Solution
The Buglab platform links organizations that have information security needs, which is just about all of them, with a community of certified cybersecurity penetration testers in an incentivized environment, where testers are rewarded when they uncover system vulnerabilities, ranked by severity and potential impacts. It’s done as a race against time. Importantly, finding unique vulnerabilities is ranked above simply producing a list of issues.
Core Features of the Buglab Platform
The Buglab platform enables customers to either use the mass of pentesters or choose a validated team from a known company. Teams must include no fewer than five pentesters.
Public Contest
Private Contest
Selection Filters
Triage System
Reports
Chat
Fix Companion
Client-Managed
Mediation
-Leaderboard
Defining Requirements
The list of potential use cases is quite long. Scenarios might include uncovering malicious SQL injection, which routes database content to a hacker. A system may have authentication bypass vulnerabilities. Sensitive company data may be unencrypted. File uploads may not be protected. User sessions may be subject to takeover by malicious entities. Perhaps the vulnerability is relatively straight-forward: for example, a company may have insufficient login security. The Buglab strategy addresses these and other vulnerabilities in a cost-effective manner to tackle cybercrime and its impact on clients’ bottom lines
Real-Time Reporting
The client company staff follow the contest as it unfolds in real time to see the reported vulnerabilities and mitigation recommendations. They’ll have the means of communicating with the pentesters to follow up. The platform can also integrate with other reporting tools at your company’s discretion.
The Contest
A client signs up on the platform and provides information about itself, including its products and services. Then, using a simple and user-friendly interface, it subscribes to a competition contract, choosing it’s rules.
Clients are able to customize the confidentiality1 of the competition, the type of management they want, and the contest cost, which depends upon the selected plan and an optional bonus. As necessary, a Buglab team will interact with customers to help them set up program parameters.
Contest Scoring
Upon the contest launch our community of pentesters that have registered with Buglab is notified. Our international cybersecurity pentesters then analyze, test, and report back on the vulnerabilities of a solution directly on the Buglab platform.
When the contest concludes, the role of Buglab is limited to vulnerability scoring and triage using the Common Vulnerability Scoring System 3 (CVSS3) standard described in Vulnerability Timestamp. Pentesters are compensated according to their rank in the contest.
Vulnerability Timestamp
Outcomes of penetration test contests depend on the Vulnerability Timestamp (VTS) that corresponds to the exact moment a vulnerability was reported.
It was necessary to set up a ranking system in order to be able to reward the best researchers according to both their overall score and timing. A pentester’s overall score for a contest is equal to the sum of all of the scores they’ve received for uncovering a vulnerability. The score for a vulnerability is based on objective and measurable criteria, thanks to CVSS3.
For such cases, researchers obtain CVSS3 scores based on the speed with which they were able to uncover the vulnerability. The first to have done so will receive full marks, and those that follow will see their score diminish according to their rank in time and the number of pentesters who have uncovered that same vulnerability
Fix Companion
At the Enterprise level, Buglab will verify that the fix has been implemented. Buglab will attempt to verify (exploit) the vulnerability again. When confirmed as fixed, a Buglab team of analysts will update the status accordingly in the platform. A “fix” can be declined by Buglab to give the company a chance to address the vulnerability again. The company will be allotted up to five attempts to address the vulnerability issue
Through the entire duration of the challenge companies can chat with pentesters and access reports, they will be able to implement recommendations to remedy the vulnerabilities in real time. This is especially useful if the vulnerabilities and the associated fixes are time sensitive. Companies need not wait until the end of the contest to implement a fix.
Service Levels
For a fixed price, Buglab will organize penetration tests done by experts pre-approved by our team. Highlights of the features with the three service levels are provided in the following table.
Vigilante Protocol
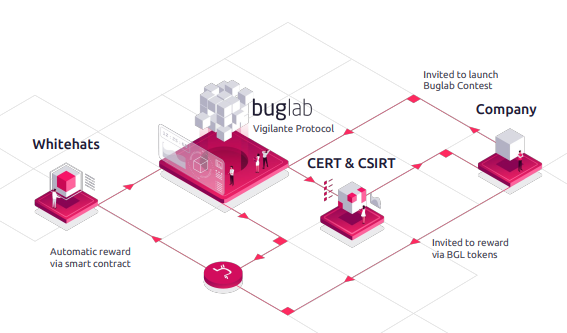
Computer Emergency Response Teams
Our Vigilante Protocol Smart Contract enables communication of sensitive information in a confidential and secure manner through the applicable certified national authorities, namely computer security incident response teams (CSIRT), which are administered by many countries across the globe.
In addition to notifying the company in question of a vulnerability, CSIRT and Computer Emergency Response Teams (CERT) will themselves have to triage and score it. In return, once the company marks a vulnerability as resolved, the response teams will be rewarded in tokens that come out of the Vigilante Protocol Reserve, as partnerships are forged with Buglab.
Assigning Pentester Status
For a whitehat to reach pentester status and to be able to participate in the various challenges, they must, when signing up for the Buglab platform, meet two mandatory requirements, i.e. furnish ID plus at least one certification. Country of residence is optional. The account is only approved once those requirements have been validated.
Another way to achieve pentester status is by acting under the Vigilante Protocol in order to prove one’s abilities and willingness to participate in our preventative security program. Once they’ve collected a total of 20 points, in accordance with the CVSS3 grading system, they will be able receive the status and take part in the challenges.
The Buglab Token
The Buglab Token (BGL) is being introduced to incentivize penetration testing in the blockchain environment. In the context of the Buglab experience, token exchange occurs in the following scenarios:
● To reward contest winners— up to the top three in rankings, or as customized by the client.
● To cover the cost of a contest, including transaction costs.
● To enable and tokenize “tipping” functionality for white hats.
● To fund both the VPR and BTR.
● To reward CERTs and CSIRTs for triaging of vulnerabilities and help build new partnerships.
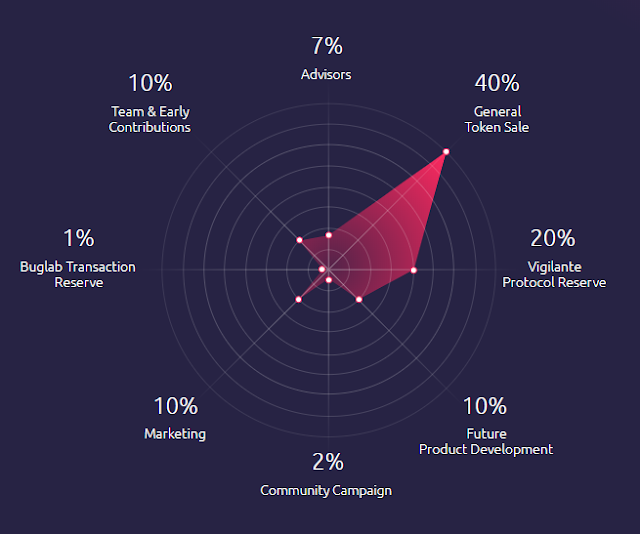
TOKEN DISTRIBUTION
So join now and invest at https://buglab.io
Source- https://buglab.io/
MORE INFORMATION :
Website : https://buglab.io/
Whitepaper : https://buglab.io/assets/docs/Buglab_WhitePaper.pdf
Twitter : https://twitter.com/joinbuglab
Facebook : https://www.facebook.com/buglab.co
Telegram : https://t.me/buglab
Reddit : https://www.reddit.com/r/buglabProject/
Bounty Bitcointalk : https://bitcointalk.org/index.php?topic=4446991
BTT ANN THREAD :
Authorized By:
My Bitcointalk account : jagadlangit
My Bitcointalk account link : https://bitcointalk.org/index.php?action=profile;u=1109252;sa=summary
My ETH address : 0xA2BFa48A6AfEFaBF498B6541f609E6cef4700D91
New Free Miner