(JACS) - which aims to change the way data networks work today

Introduction
Physical and Logical Addresses In Data Networking, there are twokinds of addresses; physical addresses (likeMAC) and logical addresses (likeIP).IP addresses and MAC addresses were developed around the same time but each wasresponding to a different problem.Consider the case of an Ethernetcable/segment overwhich several devices could be physically connected,and all have visibility to the signals transmitted onto thecable. In other words; all devices canhear all other devices,but each device has a unique identifier (MAC Address) with which they could address their data. This address would not prevent everyone else on the cable from seeing the data, but it would provide an indicator as to which, specific device was the intended recipient of that data.
But because in the real-worldnodes will not always be on the same segment, as the case of the public Internet, everydata networknode(host,router, oreven a network printer)is assigned alogical globaladdress(like IP)that is used to locate and identify the node in communications with other nodes.IPv4addressingprovides 232(4,294,967,296) addresses(just less than 4.3 Billion). However, large blocks of IPv4 addresses are reserved for special uses and are unavailable for public allocation.
Per-Interface IP Address In the IP world, if a device has several network interfaces, then each interface must have at least one distinct IP address assigned to it. For example, a laptop might have a wireless network interface and a wired network interface using a network cable, and this would require a total of two IP addresses, one per interface. Another example is a mobile phone withcellular data networkand Wi-Fi.
Routers, by nature,have several network interfaces and typically have several IP addresses associated with them. It is also possible that an interface can be assigned more than one IP address for various reasons(secondary addresses).
The IPv4 addressing structure provides an insufficient number of publicly routable addresses to provide a distinct address to every Internet device or service. This problem has been mitigated for some time by changes in the address allocation and routing infrastructure of the Internet. This started by the transition fromclassfulnetworkaddressing toClassless Inter-Domain Routing(CIDR), thatdelayed the exhaustion of addresses substantially.
In addition,Network Address Translation(NAT)permits Internet service providers and enterprises to masquerade private network address space with only one publicly routable IPv4 address on the Internet interface of a customer premises router(CPE), instead of allocating a public address to each network device.
Problems
IPv4 Exhaustion, Address exhaustion isthe depletion of the pool of unallocatedIPv4 addresses. Because there are fewer than 4.3billionaddresses available, depletion has been anticipated since the late 1980s, when theInternetstarted to experience dramatic growth. This depletion is one of the reasons for the development anddeployment other alternatives solutions, likeIPv6.The main market forces that accelerated IPv4 address depletion included the rapidly growing number of Internet users, always-on devices, mobile devicesand recently the Internet of Things (IoT).
TheInternet Engineering Task Force(IETF) created the Routing and Addressing Group (ROAD) in November 1991 to respond to the scalability problem caused by theclassful networkallocation system in place at the time. The anticipated shortage has been the driving factor in creating and adopting several new technologies, includingNAT,CIDR in 1993, and IPv6 in 1998. IPv6, the successor technology to IPv4 which was designed to address this problem, supports approximately3.4×1038network addresses.
Although as of 2008the predicted depletion was already approaching its final stages, most providers of Internet services and software vendors were just beginningIPv6 deploymentat that time.The top-level exhaustion occurred on 31 January 2011.
Four of the five RIRs have exhausted allocation of all the blocks they have not reserved forIPv6 transition; this occurred on 15 April 2011 for the APNIC, Asia-Pacific,on 14 September 2012 for RIPE NCC, Europe, Middle East and Central Asia, on 10 June 2014 forLACNIC,Latin America and the Caribbean, and on 24 September 2015 for ARIN North America.
Individual ISPs still had unassigned pools of IP addresses, and could recycle addresses no longer needed by their subscribers. Each exhausted its pool of available addresses at different times.
IPv4 Exhaustion-Reasons, While the primary reason for IPv4 address exhaustion is insufficient capacity in the design of the original Internet infrastructure, several additional driving factors have aggravated the shortcomings. Each of them increased the demand on the limited supply of addresses, often in ways unanticipated by the original designers of the network.
1-Mobile devices, As IPv4 increasingly became thede factostandard for networked digitalcommunication and the cost of embedding substantial computing power into hand-held devices dropped.Mobile phones have become viable Internet hosts. Even new specifications of4Gdevices require IPv6 addressing.
Internet Routing Security
Internet routing security is one of the pressing issues in the Internet. It encompasses the correct announcement and propagation of IP prefixes between the domains or -usingthe Internet terminology -Autonomous Systems (AS). BGP (Border Gateway Protocol) is the protocol that manages the advertisement and propagation of prefixes between the different domains.
BGP configuration is mostly done via out-of-band mechanisms where network operators tell each other which prefixes to announce among themselves. Hence, an accidental misconfiguration or a malicious attacker controlling a BGP router can divert traffic to networks which should not receive it or make ranges of IP addresses unavailable (and effectively denying global services). This attack is commonly knownas BGP hijacking and can be accomplished forging BGP announcements and propagating them to neighboring AS’s.
There were many incidents for BGP hijacking, one of the most recent one happened November2018 On November 12th, 2018, between 1:00 PM and 2:23 PM PST, some customers in the USAnoticed issues connecting to Google G-Suite, Google Search as well as Google Analytics. The reason was thatthe traffic (destined to Google)was gettingrouted anddropped at China Telecom!That was a severe denial of service to Google services. Someanalysis indicatedthat the origin of this leak was the BGP peering relationship between aNigerian provider, and China Telecom. The Nigerian providerhas a peering relationship with Google via IXPN in Lagos and has direct routes to Google, which leaked into China Telecom. These leaked routes propagated from China Telecom, via sometransit ISPs.
Numerous similar incidents taking place in 2017, were reported here: https://www.internetsociety.org/blog/2018/01/14000-incidents-2017-routing-security-year-review/
Solution Attempts
IPv4 Exhaustion5.1.1Before ExhaustionEfforts to delay address space exhaustion started with the recognition of the problem in the early 1990s and the introduction of a number of stop-gap refinements to make the existing structure operate more efficiently, such as CIDR,NAT as well as strict usage-based allocation policies.
Other technologies include:
Use ofNAT which allows a private network to use one public IP address and permitting private addresses in the private network
Use ofprivate networkaddressing
Name-basedvirtual hostingof web sites
Tighter control by regional Internet registries on the allocation of addresses to local Internet registries
Network renumbering andsubnettingto reclaim large blocks of address space allocated in the early days of the Internet, when the Internet used inefficientclassfulnetworkaddressing.
After Exhaustion1-Reclamation of unused IPv4 spaceBefore and during the time whenclassful networkdesign was still used as allocation model, large blocks of IP addresseswere allocated to some organizations. Since the use ofCIDR,IANA could potentially reclaim these ranges and reissue the addresses in smaller blocks.
ARIN, RIPE NCC and APNIC have a transfer policy, such that addresses can get returned, with the purpose to be reassigned to a specific recipient.However, it can be expensive in terms of cost and time to renumber a large network, so these organizations are likely to object, with legal conflicts possible. Even if all of these were reclaimed, it would only result in postponing the date of address exhaustion.
Similarly, IP address blocks have been allocated to entities that no longer exist and some allocated IP address blocks or large portions of them have never been used. No strict accounting of IP address allocations has been undertaken, and it would take a significant amount of effort to track down which addresses really are unused, as many are in use only onintranets.
Some address space previously reserved by IANA has been added to the available pool. There have been proposals to use theclass E networkrange of IPv4 addresses (additional 268.4 million addresses to the available pool) but many computer androuter OSsand firmware do not allowthe use of these addresses. For this reason, the proposals have sought not to designate the class.
E space for public assignment, but instead propose to permit its private use for networks that require more address space than is currently available throughRFC 1918.Several organizations have returned large blocks of IP addresses likeStanford University, who relinquished theirClass AIP address block in 2000, making 16million IP addresses available.
Utility token
At the start of its operation, JACS will leverage the Ethereum public blockchain toperform all address allocation registry functions. This means all functionality liesin the blockchain, in the form of a group of smart contracts that run in the blockchain without humanintervention.
Modifications to the information regarding the registry of JACS address blocks aretriggered by blockchain transactions and subject to the consensus of the blockchain. Therefore, the smart contracts define what a valid transaction is and then all the nodes of the blockchain will enforce that only valid transactions modify the address allocation registry information. Once included in the blockchain, the allocation of a block is irrevocable.
As discussed; JACSis initially configured with the fullblocksof globally routable JACSaddresses to allocate. When arequesting node requests someaddress block, it uses its Ethereum account to perform thisrequest. The request is basically a blockchain transactionthat transfers a predetermined fee in JACS tokens to the smart contract address; hence comes the utility function of the JACS token.
JACS thenverifies that the transaction is valid and that the fee has been correctly transferred.
Upon reception of the transaction, JACS code goes through its associated state (stored off-chain) and finds an address block that is not currently allocated. JACSassociates the available block with the identity of the requesting entity and records the hash of the off-chain allocation on the blockchain (as explained in the previous section)
As opposed to IPv4 or IPv6 allocation, JACS addressallocationis recorded permanentlyoverthe blockchain.
This way; theholder of the address blockswill never need torenew the allocationor abide to any renewal date.
There is a one-time fee to acquire an address block and there will never be any renewal or maintenance fees.
Token Legal and Crowdsale
General Information, The JACS Token does not have the legal qualification of a security, since it does not give any rights to dividends or interests. The sale of JACS Tokens is final and non-refundable. JACS Tokens are not shares and do not give any right to participate to the general meeting of viaBlockLTD.JACS Token cannot have a performance or a particular value outside theviaBlockLTD.JACS network.
JACSToken shall therefore not be used or purchased for speculative or investment purposes. The purchaser of JACS Token is aware that national securities laws, which ensure that investors are sold investments that include all the proper disclosures and are subject to regulatory scrutiny for the investors’ protection, are not applicable.
Tokenomics
JACS token will be used to request and own JACS address blocks. New users (individuals, organizations, providers, operators...) need to acquire JACS tokens to be able to acquire JACS address blocks.
Built over the Ethereum blockchain; JACS has a total of 229 = 536,870,912JACS tokensthat will be created at once.
Limited finite supply ensures liquidity and value.The main categories and sub-categories are:
Crowdfund (62.5%):
Pre-Crowdfund(12.5%)
Crowdfund(50%)
Reserve (18.75%):
Team (6.25%)
Company (12.5%)
Rewards (18.75%):
IPv4 Owners (12.5%)
Adoptersas Enablers (3.125%)
Bounty (1.563%)
Airdrop (1.563%)
Roadmap
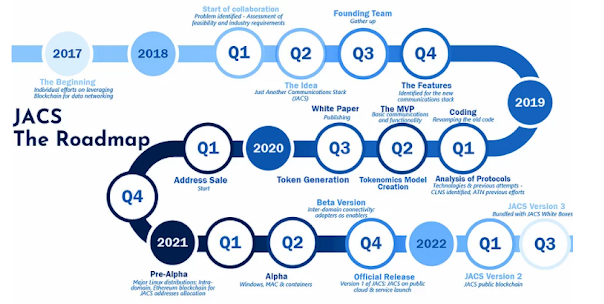
Conclusion
The information described below may be incomplete and does not imply any element of the contractual relationship. While we make every effort to ensure that any material in this whitepaper is accurate and up to date, such as products, services, technical architecture, token distribution, company schedules - such material is subject to change without notice and in no way binds professional approval or advice.
viaBlockLTD. does not guarantee, and does not accept any legal responsibility arising out of or relating to, the accuracy, reliability, currency or completeness of any material contained in this whitepaper. Potential JACS Token Holders should seek appropriate independent professional advice before relying on, or entering into any commitments or transactions based on, material published in this whitepaper, the material being published purely for reference purposes only. JACS tokens will not be intended as securities in any jurisdiction.
For more information on the JACS project you can view it below:
WEBSITE: https://www.jacs.tech/
TELEGRAM: https://t.me/jacstech
TWITTER: https://www.twitter.com/Moustafaamin77
YOITUBE: https://www.youtube.com/channel/UCICHtYggmdDTRJsPdOBs-GQ
FACEBOOK: https://www.facebook.com/viaBlockLTD
ANN THREAD: https://bitcointalk.org/index.php?topic=5279310.0
Author: luckyflop
Bitcointalk Profile: https://bitcointalk.org/index.php?action=profile;u=393201
Eth Wallet: 0xD9635878b44f209d2985a6a7282942152A6375EA