Tutorial on Bitcoin laundering with the help of Monero
You probably already know that newly-mined Bitcoins that are purchased at bulk from crypto miners are sold through OTC with 15-20% premium. Why? Because they are usually purchased by large corporations or financial institutions and legal compliance is of crucial importance to them. By getting Bitcoin from miners rather than from exchanges or other entities, they may rest assured that it will always be easy for them to prove that the BTC they own was never involved in any illicit activity.
VHCEx community members also sometimes noticed that their withdrawals from exchanges were stalled due to 'suspicions of illegal activities'.
We've been cooperating with a former US financial custodial agency investigator who wished his name to remain undisclosed. He told us about the most effective and widely used scheme of 'laundering' crypto with one of the most anonymous coin - Monero. In this article, we've decided to share this valuable information with you.

Let's start with a bit of theory:
What secures the anonymity of Monero coins?
Hidden addresses
In Monero there is no concept of permanent addresses, like with Bitcoin. Bitcoin money is constantly moving from one address to another, addresses are public, and each address has its own owner, who can manage the funds at that address. In Monero, all money moves to one-time, unique addresses each time. For each transaction, a unique one-time address is created that will be used 2 times (at the entrance and at the exit), it is impossible to determine the owner of the address for certain.
The address that you have in the mono-wallet is the “instruction” for generating a one-time address for you from “random value and your address”.
Hidden tx amounts
Amounts in any transaction are undisclosed.
Hidden sender
You don't know who sent money to you. The apparent sender might be a number of different nodes
Delusions: what, in fact, should not be done
Never believe in the anonymity of bitcoin mixers. First, you trust your security to an outside service and you have to believe their word for it that they do not keep logs, that they have no security holes or that they don’t cooperate with the authorities. Secondly, the bitcoin blockchain is public, and the entire history of its transactions will be stored "forever." How difficult it is to unwind the mixer's chain depends on the computing power and level of interest in you. But we must understand that every day such computational power will be more accessible.
Never use Monero relying on online wallets or exchanges. All these are third-party services that perfectly see your actions, and make the use of Monero meaningless.
Example: Bitcoin => exchange number 1 (BTC in XMR) => exchange number 2 (XMR in BTC). A Bitcoin user thinks that buying Monero for dirty bitcoins on one exchange, transferring them to another exchange and exchanging them is enough. Big delusion. Firstly, for the most part, all exchanges and exchangers use payment ID, and transactions with payment ID are hardly anonymous. Secondly, the exchange number 1 knows to which address the Monero is sent, the exchange number 2 knows that this address belongs to you. The chain "unwound" easier than in the notorious mixer. Your bitcoins are not cleaner. In this example, if we replace the exchange with an online wallet, then conventionally nothing changes.

How to use Monero right?
First of all, you should use the official wallet that can be downloaded here: https://getmonero.org/downloads. Then, you create a wallet, after which you have two ways of proceeds:
- Complete synchronization of your wallet with the network (this is the most secure way). To do that, you need to basically download the whole Monero blockchain and wait for the synchronization which may take a number of days.
In order to execute the complete synchronization, you should go to the settings and type in:
Daemon address - localhost 18081.
'Launch Daemon' button launches the synchronization of the blockchain with the network.
- Another way. It is to use someone's remote node to connect to the network. There are public nodes that you can find at https://moneroworld.com. In this case, do not wait for a couple of days to synchronize.
For example, connect to the node "opennode.xmr-tw.org at port 18089".
The address of the Daemon is opennode.xmr-tw.org 18089.
In this case, you do not need to click on the "start daemon" button, since this will start downloading your local blockchain, just click "connect" and wait. If the node is working, you will see the synchronization process, it may take 5-10 minutes. If the left status is "not connected", the node probably does not work, and you should try another one.
When you have the status "connected" on the left - your wallet is connected to the network, and you can spend XMR. In order for the XMR to "come", the wallet may not be connected.
The address for the XMR receipt is in the "receive" tab.
It is recommended that you use a new alternate address each time to avoid attacking a sequence.
Payment ID - do not use to receive funds. More precisely, even, it is better not to use, only for sending, when the recipient requires it.
To send funds - tab "send".
The priority of the transaction, the commission to miners - the higher, the faster the transaction.
Payment ID - when sending, always indicate if required by the recipient, such as the exchange or exchanger.
How to use Monero properly?
We’ll omit the moment that Monero blockchain, like Bitcoin's, is logging IP transactions, so we proxify everything via TOR and use either Tails, Whonix, or Torsocks.
Change dirty bitcoins on any exchange for Monero, which you send to your local wallet. For the most primitive concealment of traces of dirty bitcoins, this will be enough. Those. You can send them to the exchanger to exchange for bitcoins, and bitcoins will become conditionally clean.
What can be done for spurring anonymity of your transactions (in priority order)?
1. Increasing the transactions sequence.
Every new Monero transaction increases your anonymity.
Why?
Simplified Monero transaction scheme in simple words:
When you sent funds from a conditional exchange to your Monero wallet, this exchange, using your public address and a random number, created for you a “temporary address” (public key or one-time key) P1, to which you transferred funds for you.
To spend these funds, for example, transfer them to an exchanger, you take from the exchanger its public key (address), a random number, and generate for it a temporary address P2, where you transfer funds. But in order to hide the true sender of funds (i.e., you), you sign the transaction not only with your temporary key P1, but also with other keys from the network (the number of ring signatures at the moment is according to the standard is 11 pieces, with each new fork) in the minimum mandatory signatures grows, before it was 7, now 11, then there will be more), i.e. use another 10 third-party keys. The exchanger does not know which of the 11 keys is the true sender. But the exchanger and the exchange can exchange information (in the EU it already works), or have a common base, in this case, your transaction is partially deanonymized. Those. The exchange can inform the exchanger that P1 was used by a “such-and-such” user. But in any case, the exchanger cannot be 100% sure that P1 is the true sender. Chance 1 to 11.
Imagine that you have a second Monero wallet. Those. you transfer funds from one of your wallets to the second, and then to the exchanger.
Schematically it looks like this:
The Exchange transfers your funds to the mono-purse_1, generating the P1 key for you, transferring the funds from the mono-purse_1 to the mono-purse_2, generating the P2 key for your mono-purse_2, signing this transaction with the keys (P1, X1, X2, X3, ... X10), where X are third-party keys from the blockchain. Next, with a mono-wallet_2, transferring funds to the exchanger, create a temporary key P3 for the exchanger and sign it (P2, Y1, Y2, Y3, ... Y10). What does the exchanger see in this case? The exchanger, in this case, sees 7 keys, each of which with equal probability can be the sender, spinning each key we have:
P2 Could come from (P1, X1, X2, X3, X4, X5, X6, X7, X8, X9, X10)
Y1 Could come from (Z1, Z2, Z3, Z4, Z5, Z6, Z7, Z8, Z9, Z10)
Y2 Could come from (Q1, Q2, Q3, Q4, Q5, Q6, Q7, Q8, Q9, Q10)
...
Y11 ...
121 probability, and only 1 true, but it is impossible to reliably determine which one.
Increases in progression. The larger the chain, the greater the likelihood.
For this, it is not necessary to have a second wallet. Simply send the entire amount to yourself. Since your public key is all just an instruction for a new one-time key temporary address. Each time, sending all the coins to yourself, you simply extend the chain, creating a new temporary address (Pn), and use 6 new additional foreign keys.
How to do it?
In the "send" window, select all the coins (this is important, everything) and specify your address as the recipient. The more such transactions are completed, the greater the likelihood.
2. Countermeasures against 'periodicity attack'
Theoretical attack for deanonymization in Monero.
Let us return to the scheme "Exchange => Monero-Wallet_1 => Monero-Wallet_2 => Exchanger", which was written above. All this works fine when it happens one time, the more often such an exchange takes place, the more often the keys of the exchange and the exchanger will be compared, provided that they use the same base.
It is easier to disassemble the "exchange => Monero => exchanger" scheme, which was also described above.
In this case, if for the first time for the exchanger you are one of 11, then when you re-run such a chain, the keys will match, which is very likely to point to you, etc.
What to do against it?
It is necessary every time for the exchange to use the new address. For this, you can use "additional addresses".
3. Waiting time
This one is simple. The longer you wait before making a regular transaction in Monero, the more likely it is that your one-time key will be used by someone else for its ring signature. This increases anonymity. Those. Immediately, there is no need to commit another transaction for lengthening the chain, waiting for 10-15 minutes.
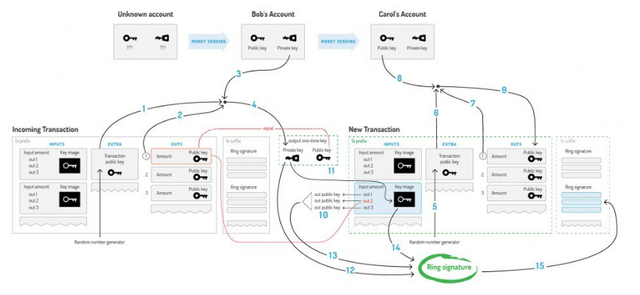
Example of an input-output transaction in Monero:
Bob decides to spend the output that was sent to the one-time public key. It needs Extra (1), TxOutNumber (2) and its private key (3) to restore it to one-time private key (4). When sending a transaction to Carol, Bob randomly generates its Extra value (5). He uses Extra (6), TxOutNumber (7) and the public key of Carol's account (8) to get her Output public key (9).
At the entrance, Bob hides a link to his exit among third-party keys (10). To avoid double costs, he also packs the key image obtained from his one-time One-time private key (11). Finally, Bob signs the transaction using his one-time One-time private key (12), all public keys (13) and the key image (14). It adds the received ring signature to the end of the transaction (15).
@Monero should definitely love this tutorial, huhuh
Do you really think those purse_N mnemonic phrases are generated by exchanges themselves?
I think they are more likely just linked to the blockchain and send the generation trigger with front-end to Monero wallet
no, exchanges generate themselves
it's an easily-embeddable leverage taken directly from Monero blockchain
there's the issue with privacy on exchanges however
no matter what exchanges generate, when it happens on the level of Monero blockchain, the seeds and addresses are mixed, so the real sender of money is always untraceable
Don't you think ZeroCoin would suit better for those purposes?
yeah, I concur, it's easier too to do just the same thing within their blockchain, no need to even transfer funds to exchanges
agreed
absolutely
the most useful text I've read in the last month
it should be posted somewhere in the darknet
hahah, just realized this article is the most popular of VHCEx :)))
Binance 7k hacker should realle pay attention to this one, lol
I think they will probably just get off with BTC mixers