Hackers Using Fake DDoS Protection Pages to Distribute Malware
Hackers Using Fake DDoS Protection Pages to Distribute Malware
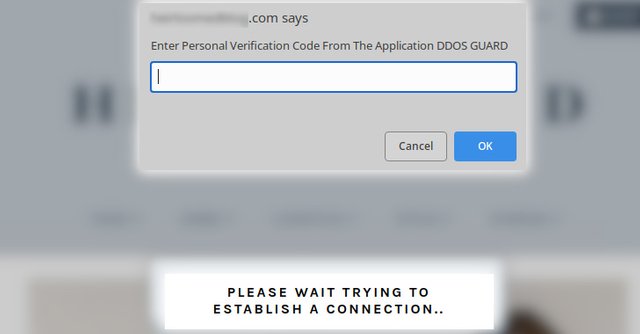
WordPress sites are being hacked to display fraudulent Cloudflare DDoS protection pages that lead to the delivery of malware such as NetSupport RAT and Raccoon Stealer. "A recent surge in JavaScript injections targeting WordPress sites has resulted in fake DDoS prevent prompts which lead victims to download remote access trojan malware," Sucuri's Ben Martin said in a write-up published last week. Distributed denial-of-service (DDoS) protection pages are essential browser verification checks designed to deter bot-driven unwanted and malicious traffic from eating up bandwidth and taking down websites. The new attack vector involves hijacking WordPress sites to display fake DDoS protection pop-ups that, when clicked, ultimately lead to the download of a malicious ISO file ("security_install.iso") to the victim's systems. This is achieved by injecting three lines of code into a JavaScript file ("jquery.min.js"), or alternatively into the active