// Hacking NEWS // Japanese Government To Create Defensive Malware
The Japanese Defence Ministry will create and maintain cyber weapons in the form of malware that it plans to use in a defensive capacity.

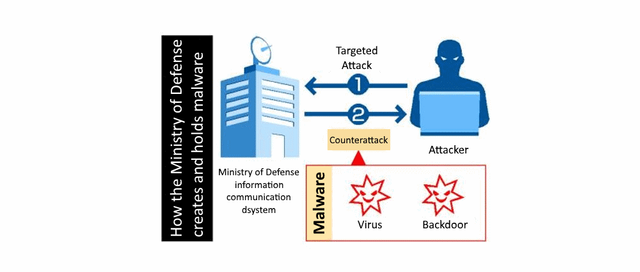
Once created, these malware programs, composed of viruses and backdoors, will become Japan’s first cyber-weapon, the Japanese media reported this week.
The malware should be finished by the end of the current fiscal year and will be created by external providers, and not government employees, a source familiar with the situation told ZDNet.
No official details are available on the capabilities of the malware or on the exact scenarios in which the government plans to use it. Although, a graph published by the government suggests that malware will only be used when Japanese institutions will be under attack, and only against the attacker.
Japan expanding into the cyber battlefield
The announcement comes as the Japanese army has been expanding and modernizing to keep up with modern times and to counteract China's growing military threat in the region.
As part of this modernization effort, the Japanese government plans to expand its military's reach into "cyber" which NATO formally declared as an official battlefield in June 2016, next to air, ground, and sea.
Japan is the last country to officially recognize that it owns and develops cyber weapons. The others include the United States, the United Kingdom and Germany.
Israel, China, Russia, North Korea and Iran are countries that own, develop and aggressively use computer weapons, but they have never officially recognized it.
Government sources in Tokyo told the local press that they hope that just by being in the possession of a cyber-weapon, this would deter foreign actors from attacking the country.
This could be a somewhat naive approach: as the United States, the country with one of the largest and most dangerous assortments of cyberweapons, is constantly attacked by Chinese, Russian, Iranian and North Korean hackers.
This is also the second time the Japanese government attempts to create a cyber-arsenal after a previous attempt failed. In 2012, he asked Fujitsu to create a "search and destroy" malware.
Japan's plan to hack citizens' IoT devices
Nevertheless, the Japanese government seems determined to strengthen its cyber-capabilities, including its ability to respond to cyber-attacks.
Earlier this year, the government passed legislation authorizing National Institute of Information and Communications Technology (NICT) employees to hack citizens' IoT devices using default or weak credentials, as part of an unprecedented investigation into unsecured IoT devices.
The plan is to compile a list of insecure devices that use easy-to-guess default passwords and pass it on to authorities and the relevant Internet service providers. By doing so, they can take measures to alert consumers and secure devices.
This plan was put in place to secure IoT devices before the Olympic Games in Tokyo 2020 and avoid Olympic Destroyer and VPNFilter-like attacks.
Ironically, all these plans come from Japan’s new Cybersecurity Department, which is part of its Defense Ministry. Yoshitaka Sakurada, head of Japan's Cybersecurity Department, was severely criticized last year when he publicly admitted that he does not own, use or know that much about computers...
Source : The Japan Times

I've made a lot of articles with tools, explanations and advises to show you how to protect your privacy and to secure your computer, GO check them out!
This is my guide To Secure your PC after a fresh installation of Windows
If you think that your Phone or your PC has been hacked, you have to check it right now!
That's how you can be more Anonymous on the internet!
The Future of Cyber-Security, what to expect?
The best Crypto debit card – Wirex!
These are the best VPN to protect your numeric life: NordVPN, ExpressVPN and CyberGhost!
Your PC is slow? That's why!
Why is it important to Be Discreet on the Internet
Feel hot? Your Computer also!
How an Adware works?
That's how you should guard against Trojan!
What are the different Types of hackers?

This is really alarming, although malware's exist decade ago. But this government back malware or cyber weapons if fall in the wrong hands. No one is safe for real.