Beam - The best option to have the best privacy


Preface
Since Bitcoin and BlockChain technology emerged, this technology is revolutionizing the future of the economy and society, many people have been attracted by this technology, because it is a decentralized way of making transactions and the movement of digital assets, many people turn to this technology for their privacy and trust.

Many people are willing to do anything in exchange for having a great privacy and trust, this is something that Bitcoin also offers, also today the average person is more concerned about having greater security in their activities and operations on the Internet .
The Blockchain technology allows us to store the data in a more secure, immutable, decentralized and transparent way, but something that is certain is that this technology is still a slow system, not scalable, with a limited storage capacity and that may have privacy problems
Having the ability to react and adapt without losing quality or also becoming bigger without losing quality in the services offered is something that we need today, it is a big problem that the technology that we use today and see as a revolutionary even present certain faults and problems.

And the truth is that this technology is a slow system with privacy problems, to be able to visualize all the operations that are stored is the block chain has its negative point, because if a person wants to remain anonymous in the long run, a person expert in the topic of piracy can find all this data if it goes from the beginning of operations, thus giving to know the identity of this person, the amount of their assets and even their personal data.
Then the technology we saw as a great alternative and the best option can present its drawbacks, so it is necessary to improve the system, attack the weak points of this technology to strengthen and thus improve privacy and offer a better trust.
That is why I will talk about Beam, is the scalable confidential cryptocurrency that is needed and how along with its use of the Mimblewimble protocol, they will achieve great improvements in the chain of blocks.

What is Beam?

It is a decentralized currency with great fungibility and the ability to react and adapt without losing quality, also has a great privacy, and that Beam transactions are private by default.
Besides with Beam it is not necessary to have to store all the transaction history, something that is required for the block chain validation, but this causes the chain of blocks to be reduced in large size, which achieves a better ability to react and adapt without losing quality, thus achieving continuous growth in a fluid way.
Beam will allow the admission of several types of transactions that are important, such as custody and time-blocking transactions, as well as others.
The Beam cryptocurrency is based on an innovative MimbleWimble protocol. Beam is special for several reasons and that is with Beam users have full control of their privacy, deciding that data or information will be available, allowing you to have full control over your personal data.

In Beam there is a point that is important and it is confidentiality, and that having confidential transactions does not generate penalties, and thus in this way they do not generate an overload in the chain of blocks avoiding a computational overload.
The blocks are extracted by means of the Equihash algorithm, besides a point that is of the utmost importance is that the information about the sender or receiver of some operation performed is not stored in the blockchain, offering that much desired anonymity.
Beam uses the Equihash mining algorithm because it is well accepted by the miners worldwide, and that is that Equihash is based on trying to solve the generalized problems, and comparison of the Bitcoin that requires a lot of processing power the Equihash requires a large amount of memory, currently there are ASIC miners dedicated to extracting Equihash ten times faster than the average CPU.

The need for anonymity
At the beginning of the launch of Bitcoin and its boom, all people believed that the transactions in this network were private, that they had anonymity, it was what they believed due to how this network worked.
The network was in charge of creating random pairs of private and public keys, so many users or the majority assumed that with the use of the public part for the formation of addresses that would be implemented to receive and handle transactions, nothing in the process would serve for a link of your real identity.
It is important that you know how a transaction works in this network, a transaction consists of three parts:
Input / s, sections of the address of the user X that contains the bitcoins.
Quantity, which is the amount that a user X would send to the user Y.
Output / s, the user's purse Y.
It is important to note that all this internal operation is represented under Bitcoin Scripting.

Unfortunately these users were all wrong, because with an analysis to the chain of blocks there would always be infiltrations of data, these data can come from any process that has been done, and that is that having all data open and that are always stored in a book in view of all, any pirate who takes the time to thoroughly investigate all past and future transactions of any user, as well as their balance also, could achieve link all these data with the person.
This is what we have always wanted to avoid, initially using Bitcoin users believed that finally had the desired confidentiality, it is something that people and companies always want to have, that their balance and their operations remain anonymous.
All this would be possible to avoid if it could limit the visibility of the details of the transactions and try to keep the least amount of information in the public registry, thus avoiding the investigation by some malicious entity of this data, this is something that the chain of blocks MimbleWimble Beam to be of lesser magnitude than any other implementation of blockchain can achieve, all this in addition without compromising the security of the block chain.

Solutions proposed to date

There are several solutions that have been proposed to this day, one of them and the best known would be Greg Maxwell who discovered how to encrypt quantities, which makes the graphics of transactions are not recognizable, but still allows Validate the correction of quantities.
Maxwell also CoinJoin development, this is a system where Bitcoin users can interactively combine transactions.
The CoinJoin system has a problem and it is to specify the interactivity, so Dr. Yuan Horas Mouton looked for a solution to this problem making the transactions merge freely, but for this he had to use the cryptography that is based on the pairing, but this process is slow and less trustworthy, Yuan Horas Mouton named this as unidirectional aggregate signatures (OWAS).

We also have Nicolas van Saberhagen who developed a system in charge of hiding movement records. Then Shen Noether combined the works of Maxwell and Noether to obtain the confidential transactions of Maxwell and the obscuration of van Saberhagen.
Going back to the great idea of OWAS, it was a great step to unite the operations and we can create and destroy the outputs, which would be as if they had never existed, and in this way it would only be necessary for users to know when money is introduced to the system to validate the entire chain.

Beam and MimbleWimble
Beam is a novel implementation of Mimblewimble, this was a protocol released by an anonymous developer managed by "Tom Elvis Jedusor" which proposed for the first time an option for a better cryptographic protocol that was of great help to solve the problems of anonymity and improve Scalability, MimbleWimble was later named as the spell of the famous saga of sorcery Harry Potter.
To understand a little more about a cryptographic protocol, it is not too much to say that they are those points that in order to carry out an interaction, they need to use cryptographic functions, in order to assure the security requirements in the communications between the users that interact in this process, such as confinciality, integrity and authenticity.
MimbleWimble is based on two concepts originally proposed by Grex Maxwell which are:
Confidential transactions, this uses two basic properties which are, concealment and linking. In this way, the user is responsible for keeping the password hidden until it is sure that the commitment is valid, offering better security and greater anonymity.
The first thing that should be done in this process is to eliminate the Bitcoin Script, it is a regrettable but necessary thing to do because this process is too powerful, which makes it complicated to join transactions with general scripts.
MimbleWimble also uses a well-known compromise scheme of Pedersen, this is a method for a user X to prove to a user AND that the statement is true and all this without revealing anything other than the truth of the statement.
In addition, the Pedersen commitment achieves all this using elliptic curve cryptography and is as follows:
C = r * G + v * H
A simple way to explain this is that r is a blinding factor, which is a secret key responsible for hiding the real value where v, G and H are points generating a specified elliptic curve, along with this output we can find a test which gives us to understand that v is in [0, 2 ^ 64] and in this way the user can not exploit the blinding and thus avoids overflow attacks.
To validate transactions or any transaction it is necessary that commitments be added for all products.
Merge transactions in blocks, imagine each block as a large transaction, now the transactions of two blocks could be combined in a single block, resulting in a valid transaction, but we can also assume that both commitments are exactly the same, where the output of the First block was used in the second block, then both commitments could be eliminated and still manage to obtain a valid transaction.
And is that there is currently a problem and is that many transactions are maintained that have no use, suppose that in a block has been spent and verified the money of all transactions except one, logically we would not need the rest to verify any process because We are not going to reach such depth in the chain, but we have to keep these transactions in order to verify the transaction that has not been spent.
Using Pederson's commitment, we can cut two transactions if they are identical, explaining it in a better way, if we have two transactions which are F to G and then G to H we can cut the intermediate transaction, obtaining as a result a transaction from F to H , shorter and with less data, offering greater security.
Then it is only necessary to test the value and the single blinding factor, because it is not necessary to have to store any other record in the chain of blocks, after creating the transaction between both parties only the commitment is the one registered in the blockchain.
Each transaction of MimbleWimble also includes the Transaction Kernel, which is the one that contains the difference of the blinding factors of the sender and receiver. They also use Bulletproofs with the finality of avoiding and guaranteeing that the value of the transactions are positive and without disclosing the real value, this with the purpose of preventing a user from creating transactions of negative value, because this would start the creation arbitrarily of new currencies which should be prohibited by the system.

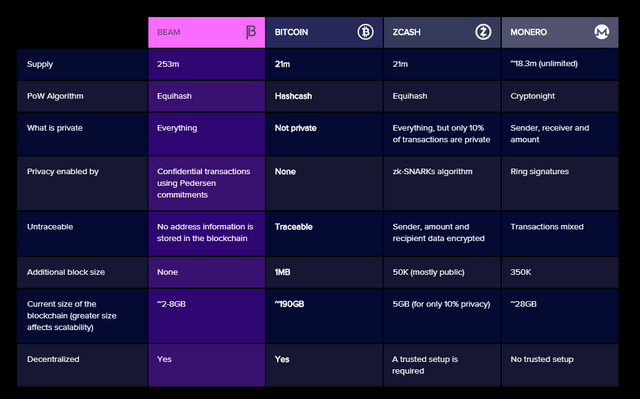
Beam comparison
We can compare Beam with other cryptocurrencies, and we can find what are the big differences and advantages that Beam can offer us, which range from:
- A better supply.
- A super important algorithm.
- Beam offers privacy to the elderly, thus having greater confidence knowing that everything is private.
- It prevents the tracking by any individual and is that because it is not stored all the information in the block chain makes it impossible to track the user's data, which is really a great advantage.
- A smaller size in the chain of blocks, which makes it an ability to react and adapt without losing quality.
- And what everyone always seeks, that is a completely decentralized system.

Beam Characteristics
Beam has six features that are of utmost importance for proper management of your system, which are:

Confidentiality, each transaction is only accessible by the person authorized for said information, and no data is stored about the users that are participating in the transaction.

Versatility, "Scriptless Script" technology gives the ability to quickly and easily adapt to different functions such as atomic exchange, security deposit and transactions blocked by time.

Scalability, MimbleWimble offers us to combine the transactions in block keeping only the necessary ones and eliminating the sensitive and private information avoiding in this way also an excessive overload, this makes that the chain of blocks Beam is of greater impact since it has a smaller magnitude than any other chain of blocks.

Sustainability, the best way to keep the process productive is to offer 20% of the reward of block mining, this group is destined to encourage the development of Beam.

Usability, having a wallet that is used both in computers and mobile devices, offers a facility for people to handle it and so that the administration of the budget is easier and with valuable information.

Compatibility, the proven Equihash algorithm has been implemented in the industry that has the quality of being compatible and that can compete in good conditions to ensure the adoption by the miners of the GPU, in this way Beam has an extensive set of tools that allows you to run and manage the mining nodes.

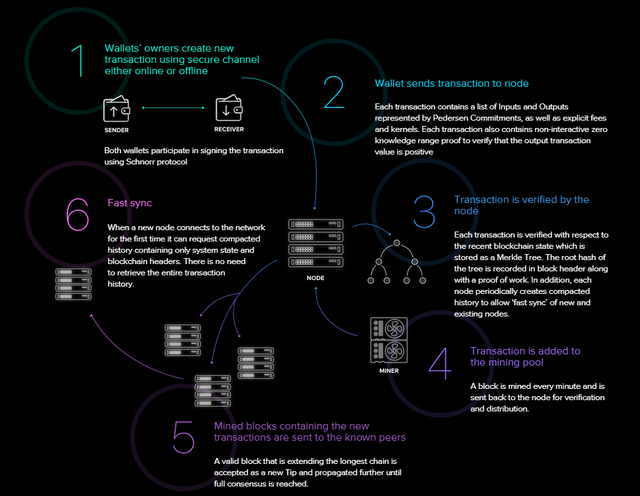
Internal operation of Beam
This process works in the following way:
Through the identification algorithm of Schnorr which is an identification scheme is with the both owners of cartes X and Z can perform their transaction
Each transaction goes through a validation process through a commitment scheme oriented to the Verification of Shared Secrets or more known as the Pedersen commitment, this with the purpose of validating or verifying that the exit amount is correct and can be made.
Then the next process is to be verified by the node, every transaction that takes place must be verified.
Along with the group of miners who are constantly extracting new blocks to verify transactions.
The blocks that are extracted and that have been validated are propagated until the total consensus is obtained.
And last but not least, it may even be the most valuable of this process and is that when a new node makes a synchronization with the network only needs state of the system and the headings of the chain of blocks, it is not necessary knowing or handling all the valuable information for users if there is no need to know such information.

Privacy is everything

Being able to rely on privacy and anonymity is something that since the beginning of the money started, all people have resorted to any method that can offer them privacy, the option of keeping all the data saved and free of any piracy and far from the reach of anyone.
This is something that has always wanted to obtain both in banks and in any financial institution worldwide, offer the user privacy to keep it satisfied and continue to use these services.
In a beginning when Bitcoin emerged, all the people thought and drew a hasty conclusion that they finally found a solution for the total privacy that they had been looking for, and that despite all the advantages that blockchain and bitcoin can offer, with its decentralized method free of the banking environment, it still has its deficiencies when it comes to anonymity, and that is that with the system of the chain of blocks everything is in sight.
This is something that needs to be eradicated, all personal data should not exist or be latent, the amount that people have in their wallets and the transactions they have made, all this should remain hidden, only showing the transactions that have been made but without offering a large amount of details, thus preventing anyone from knowing the identity of others.
Beam wants to solve this, combining the block transactions and eliminating from the view of all those transactions where the personal data could be visualized and leaving only in sight the essential for the proper functioning of the block chain and its decentralized system, would help a better privacy and anonymity, in addition to the features that Beam offers us and privacy by default without penalty makes it a lighter system, without the problem of an overload or weight of data, all these features make Beam offer us and give us the privacy that is so important for cryptocurrencies.

Beam - Cases of use
Case 1
Peter is a miner, he has dedicated many hours of his life and several powerful processors specifically commissioned to mine, this is his job, he gets great profits to support his home, Peter has many years in this ecosystem and has already suffered from infiltrations so he has had to use several wallets to exchange and secure his cryptocurrencies.
This has been a constant problem and which has not been solved because the alternatives in the market do not offer the solution that he needs to solve this problem and be able to continue with his mining work without having to worry about his data that are in sight of all.
Peter decided to put a pause on mining and devote the hours that are necessary to a system that allows him to make transactions without the worry that all his data is seen by everyone in the block chain.
It is there where Peter after arduous hours of search gets Beam and how Beam based on Mimblewimble allows the combination of block transactions, taking into account only the important transactions and excluding those data that are important and privacy for the user.
Since Peter now uses Beam he was able to resume his mining work and he could be calm because he knows that all his transactions now remain anonymous because only those transactions that are necessary for a good performance of the chain of blocks but that are not visible are visible. they leave their identity at risk.
Case 2
Chris is passionate about the surveys, he spends all day doing surveys, but of course, paid surveys, from there he gets a good pay and can go out to enjoy with his friends, to go out with his partner and contribute with food in his house, it's practically a job for Chris.

These surveys offer their payment in small installments of some cryptocurrency, which in the long run after having completed several surveys Chris will have managed to collect and obtain a large profit in general, so then Chris has to resort to the exchange of being cryptocurrencies through the chain of blocks, but there is something that bothers you and is the fact that all your data, keys and transactions are constantly in view of all, there is no privacy.
Chris wants to solve this, he does not like to feel that his data is being observed by people who are not known and who may not be trusted. It is there where a friend of Chris tells him about Beam and how he offers anonymity to his data, also doing a safer and even less burdensome work since all of his data in the block chain does not have to be visible.
Since Chris started using Beam, he can now perform all the necessary transactions feeling safe, knowing that his personal data, transactions and the balance of his wallet are no longer visible but still have the confidence that a decentralized system offers. , all that was thanks to Beam.

Conclusion
This publication in which I have spoken about Beam is so that they knew him in a better way and saw all the characteristics that he possesses and all the benefits that he offers us, in addition to how they come to solve the privacy problems that we can find today in the chain of blocks.
And is that Beam has great features that give us to understand that we can make our transactions more safely, since they offer us the elimination and those data that will not be necessary that are in view of all and that are those personal, which undoubtedly we want to keep private, nobody wants to have their data, their transactions and even their balance available to any person.
Each person is responsible for making their data in a secure and private way, this solution was already necessary in the market, because with the increasing use of cryptocurrencies, bitcoin as such and the chain of blocks, it was a solution that I was asking for shouts so that each individual could be calm and remain anonymous, it is for this and other reasons that I believe that Beam will be seen with good eyes and will be taken into account from now on the market as a solution.

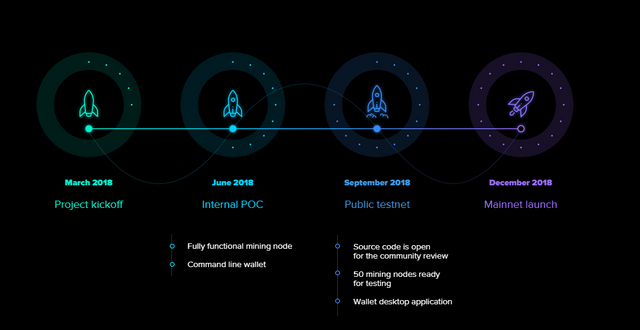
RoadMap

Team Beam

Investors

Check my video

For more information watch this presentation by the CEO, Alexander Zaidelson:

More Information and Resources:
- Beam Website
- Beam Position Paper
- Mimblewimble Paper
- Beam YouTube
- Beam Telegram
- Beam Facebook
- Beam Github
- Beam Bitcointalk
- Beam Medium
- Beam Twitter

This contest is offered by @OriginalWorks if you want to participate go to:
https://steemit.com/crypto/@originalworks/1125-steem-sponsored-writing-contest-beam
Twitter Bonus
Click Herebeamtwitter
beam2018


@contestbot
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by deyvich from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.
This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Congratulations @deyvich,
Your post "Beam - The best option to have the best privacy" hast just been Resteemed !!! 🙂🙂🙂
You have achived this service by following me.
😄😄😄 Be ENGASED to continue with this FREE Restreem service @tow-heed😝🙂😝