Goldilock: Top Security Suite for Digital Assets and Cryptos

Vulnerability of information on the Internet
Internet works thanks to the existence of a fluid connection between the main computers of the planet, composed mainly of servers in which large volumes of information are stored, and are an essential part of the modern structure of the Internet.
This interconnection has favoured the development of all kinds of technologies, developing applications that have allowed information to be transmitted to any place on the planet, even the possibility of transferring values or making real time video calls between people who are far away.
As the Internet became a more useful technological tool, the information transmitted through it acquired more value, particularly information that was already valuable on its own, thus increasing the importance of information security on the Internet. Currently there are all kinds of security protocols, passwords, encryption methods, security checks, and others. Some methods provide an acceptable degree of security for common utilities, but all existing platforms continue to operate through the same scheme, maintaining a continuous internet connection which makes it possible for malicious people to make infinite attempts to steal valuable information, until they do so, and for this reason there are still hacking and kryptonite thefts today.
Reasonably, the only way to be completely safe from the risks of Internet theft is to use traditional alternatives to this tool. However, the usefulness of the Internet is such that it has become an indispensable technology for the development of societies. In more practical online utilities such as searching for public information, or accessing digital tools, the benefits of the Internet outweigh its inherent risks. But when it comes to money and digital assets, the scheme changes completely. First, no one with great riches would like to keep their money or digital assets on the Internet knowing the potential danger of losing them, and the second thing is that there is still no platform that offers a magnitude of benefits comparable to the Internet, so dispensing with this tool would be almost counterproductive, because almost all elements of society work around it.
Fortunately, there is a solution to everything. Goldilock has developed a security method that provides a definitive solution to the problems of Internet vulnerability. The Goldilock team has created a device that stores all valuable information locally (cold storage), but this can only be accessed through the Goldilock platform on the Internet, which synchronizes the data to authorize the management of the information. In this way, Goldilock offers a new security scheme that moves valuable information away from the dangers of the Internet, in addition to the highest standards of protection of digital information. Resulting in an absolutely secure method of storing information and values.
Goldilock solution for the security of Cryptocurrencies and Digital Assets
Goldilock is a security system for assets and digital money, created with the aim of offering a secure method of storing information offline. It works as a remote cold device (USB hard drives), in which the owners are the only ones who can access the information through the encryption of the platform, because the data is always stored in the key device, and never gets to be hosted on the Internet.
When using the Goldilock device, encrypted nodes are stored locally that allow synchronization and security verification between the stored information (valuable data) and the parameters set on the platform. Once the device is connected to the platform, it must go through a security verification process similar to that implemented by the sensitive information management pages (two-step verification, confirmation by codes, passwords, encrypted keys and so on) to give access to the nodes on the platform. After the user has made all the transactions and is ready to disconnect the device, the Goldilock system reverts the nodes to the device, disconnecting the information from the internet.
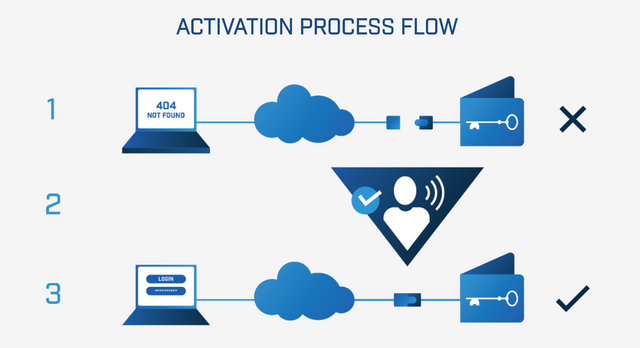
Source
Goldilock implements in its system the two current solutions for information privacy and digital assets, they are hot storage (Cloud storage, exchanges, online wallets), and cold storage (personal USB hard drives, Trezor, Ledger Wallet and others).
- Hot Storage:
The hot storage solution is the best known, even for people without money or digital assets. These are storage solutions within reach of anyone, they work by storing the information of all users in an encrypted way on the servers. Hot storages are mass usage services, so they are always online, so that each user can access their data at any time through a couple of security verification steps.
The main disadvantage of this solution is the way it works. Since it is always available on the Internet, hackers can try to acquire it, and since the information will always be stored in the same place, it makes it possible to keep trying until they get it eventually .
- Cold Storage:
This is the safest method so far, but it is not perfect either. In this method the information is stored on a device disconnected from the internet, and only with that device can it be accessed. There is more safety, but more responsibility and care must be taken, because these devices cannot be replaced when they are lost or broken. This is a method for people committed to your safety.
Both methods have their advantages and disadvantages, but when combined in the same system they complement each other, forming a highly effective safety method, and that is why the Goldilock solution is revolutionary. Goldilock uses the best of the two existing storage solutions (hot and cold storage) to create its revolutionary system.
Prior to Goldilock, methods of protecting information and digital assets had focused only on creating complex parameters that made data difficult for their owners to access and confusing. But thanks to Goldilock you can be sure that it is a completely secure system, as there is nothing stored on the Internet.
Goldilock System Application Forms
Goldilock covers a wide range of possible applications in all types of fields. From the personal storage of very valuable information to the protection of large volumes of valuable assets, all of them through a completely reliable and secure method.
The curious thing about Goldilock is that it is composed of two secure storage methods that individually cover very specific aspects with great disadvantages and security gaps, but when complementing these methods, all security gaps disappear, and the security of your method is absolute.
- Identity validator & Identity data backup:
The data about us is perhaps the most requested information by hackers, and not directly our digital assets, because all these assets are stored in places where they can only be accessed with our data. But there is a problem, our identity data is often stored in emails, or in cloud storage, which puts our assets at risk.
By implementing Goldilock in the validation of our identity, we guarantee that none of our data will reach the Internet. Using these at the time of verification, and then they would be stored again in the device offline.

Source
- Cryptocurrencies Wallet:
In the same way as cold storage wallets, Goldilock can keep crypto coins completely safe, additionally the system facilitates the online connection to take advantage of the benefits of internet cryptocurrencies, such as trading, or investments. Goldilock offers the benefits of the two existing storage forms of cryptocurrencie in one system, and at the same time its security system makes it attractive for more people to adopt.
- Critical information storage:
Goldilock's security system is not only limited to the safeguarding of money, there is also information available from corporations, development centers, and financial institutions that require the highest security standards for the safeguarding of their data. In these cases, Goldilock would represent a totally reliable method, by securely backing up and disconnecting data from all entities from the Internet. It will certainly not be practical to store large volumes of information on the Goldilock device, its practical utility is to use it as a unique key that allows access to such information, in addition to the various methods of identity and security verification to allow access to files.
"Goldilock LOCK Token
LOCK is the utility token that will be used to provide a gateway for Goldilock services.
The LOCK token is required to access the Goldilock Wallet. When the user logs into the Goldilock Wallet, the Wallet will query the NEO public Blockchain to confirm the user’s public key address owns a LOCK token. If the user’s public key address owns a LOCK token, then the Goldilock Wallet will launch in the user’s browser. When the user is granted access, the Wallet will write audit information to our own Private Audit Blockchain. These audit entries will ensure that every time your private key is brought online, this access is written to immutable storage that can be queried from the Goldilock Wallet.
LOCK token allows Goldilock to provide users with a record of their node activity, while keeping user-owned data encrypted and locked away even from everyone including the Goldilock team."
GoldilockRoadmap
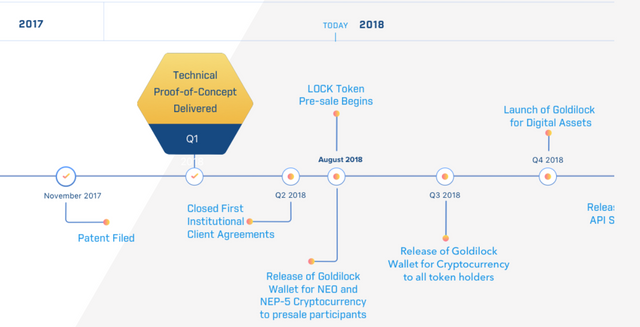 Source
SourceMore Information & Resources:
- Goldilock Website
- Goldilock WhitePaper
- Goldilock Tokenomics
- Goldilock Telegram
- Goldilock Discord
- Goldilock Linkedin
- Goldilock Facebook
- Goldilock Twitter
- Goldilock Reddit
- Goldilock Github
And here is my video:


This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!