Reflections After the Fomo3D Game Was Broken
Introduction
The first round of Fomo3D, a well-received and ‘never-ending exit scam’ game launched on the Ethereum platform ended August 22nd. It was a surprise for many people. The last prize was won by address 0xa169, and the total purse reached 10,469 Ethereum.
Exitscam.me describes Fomo3D as ‘a psychological social experiment in greed’. They outlined the rules as:
Instead of tokens, players purchase keys to the ICO funds held on the contract
Being the last player to buy keys lets you exit scam the game and drain the ICO funds for yourself when time runs out.
Keys provide you passive ETH income the longer and higher the round runs. Even locking you an ever-increasing personal portion of the ending exit scam!
Every key purchased extends the round time upwards towards a hard cap. To always keep the exit scam within reach of any player
There is no limit to how many times a round can be extended.
Clever players can recruit others, bet early on how high a round might go, or collect mini exit-pot airdrops at any point in the round.
You won’t walk away empty handed when it ends… if you let it end
Was the final winner a lucky player? As will be detailed in the following, obviously not. The terminating outcome resulted from a well-designed and thoroughly tested (malicious) exploit using Ethereum’s limited scalability capacity. The grand prize winner skillfully manipulated this technical weakness of Ethereum with a unique attack strategy that caused the number of transactions packed into a specific set of blocks to be reduced. Although in theory the strategy was not guaranteed 100% success, but it does ‘bias’ the game towards much greater probability of improving your ‘luck.’
Exploit / Attack Chronology
Let’s review the progress of the exploit:
At block height 6191896, the attack key 0xa169 is added to the block.
From block heights 6191897 to 6191902, the attacker begins to use a special smart contract to fill each block and set the gasPrice to an average of around 20G wei. One must admire the patience of hackers who passively monitor the transactions in the network. As a result, no one else was able to participate in Fomo3D in the next six blocks.
Starting from block height 6191903, the attacker suddenly increased the gas price of the contract transaction to 190 GWei, well above the average level. The subsequent transaction set a super high gas price of 500 GWei and the real attack started. Until block height 6191908, each of the six blocks contained less than 10 transactions, and the available gas was completely occupied by these invalid transactions consuming a high gas. The Ethereum network was now blocked.
At block height 6191909, the attack is over, and the network status is back to normal.
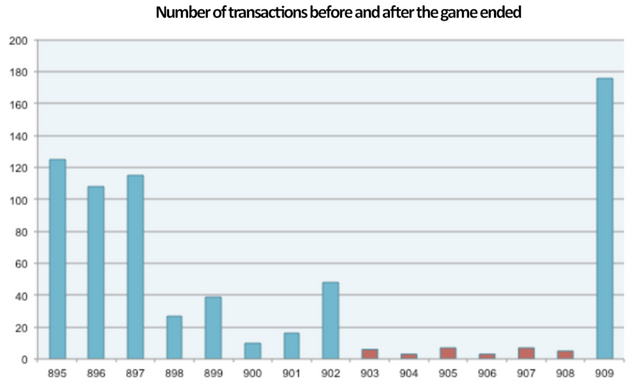
red blocks are the one been part of the malicious exploit regarding Fomo3d
The attack strategy was planned to be rigorous and ruthlessly efficient. To start, a high gas price is used to attract ETH miners, then a ‘rigged’ smart contract at the Ethereum virtual machine execution level achieved the goal of subverting the entire ETH network. This prevented other Fomo3D players from participating at the critical buy-in moments.
Of course, the attacker’s plan was not guaranteed. One transaction with a gas price up to 5559 Gwei tried to purchase a Fomo3D key appears into the block 6191907. However, (it is a pity that) the gas limit of this transaction was only set at 379000. The lack of gas limit causes this transaction to fail (due to an out of gas error). It squanders a 2.1 Eths fee and eventually loses out on the grand prize.
The only high gas price transaction that breaks through the malicious attack.
Exploit / Attack General Analysis
The transactions are not selected randomly
- Fee competition
a. Ethereum, the miners prioritize the package from the selection of transactions in which the gas price is significantly higher than other transactions, which is the selectivity of the transaction. Based on the principle of fee competition, the hacker can artificially increase the gas price including some invalid transaction calling a smart contract and use these meaningless transactions to occupy the available gas of the block in a short time, so that other normal transactions cannot be packaged.
- Gas limit
a. The number of transactions that can be included in a block in Ethereum is controlled by the gas limit of the block. The number of transactions that can be included in a block depends on whether the total gas consumed by the execution of these transactions reaches the gas limit of this block. The upper limit of the gas limit of the current block is generally 8 million gas.
b. Each transaction on Ethereum also have a gas limit concept, which is set by the transaction initiator to represent the maximum gas consumption that can be consumed by the transaction. The actual gas consumption is subject to the specific execution cost of the transaction.
- invalid instructions
a. You may want to ask the attacker how to successfully take up the gas limit of the entire block through a small amount of transactions? Then you must mention that three instructions in the Ethereum smart contract Solidity can cancel all state changes in the contract execution and lead to the contract execution. The instructions that stop are “require”, “revert”, and “assert”. According to the instruction design of the EVM, calling require and revert uses the EVM opcode 0xfd. When the program stops executing, it will roll back and return the remaining gas for the transaction execution. When assert is called, the EVM opcode 0xfe invalid command is used when the condition is met, thus consuming all available gas attached to the transaction. The gas limit of the block is exactly the attacker’s goal, so we see that he used “Bad Instruction” which caused failed transactions using the 0xfe invalid command before the game ends, all due to “assert” instruction.
Turing complete smart contract
The concept of a ‘Turing complete smart contract’ proposed by Ethereum has many advantages compared with the simple scripting system of Bitcoin, but there are also great security risks. Since Ethereum’s is live, malicious incidents caused by smart contracts have emerged one after another.
- We cannot predict the amount of used gas
a. The reason why the above-mentioned transaction failed is because we cannot effectively predict the gas limit because the fomo3d project itself is only partially open source. Its main contract 0x9da1 is open source, but looking at its code, there are still three sub-contracts that are not open source.
- Decompile
a. The Ethereum Solidity language does not currently have any decompilation tools, so it is impossible to effectively predict or verify the results through the code. It can only be reversed by tracking the historical data. The lack of formal verification is a vulnerability of the contract. It is the Turing code level of the Ethereum that makes it possible to implement contracts with complex terms. Making it more difficult to analyze, it is convenient for hackers to launch attacks, which also allows us to see the need to limit code complexity and functionality.
Enlightenment to the architecture of public blockchain projects
Design a more reasonable fee model, instead of Ethereum who only charge the gas by performing operations on the EVM.
Cancel 0xfe and other invalid instructions, gas consumption is limited to the actual use, do not allow the abuse of gas to submerge the network.
Limit the number of times a high gas consumption instruction can be used in the same block. Miners can block such transactions through static code checking.
Take measures to limit smart contracts that are not open source. Explicitly mark the unopened smart contracts and the contracts they call and provide effective smart contract decompilation tools.
Simplify the smart contract instruction set. Cancel jump instructions and limit the use of general loop instructions. At the same time, the use of predictable loop instructions is encouraged to facilitate the static checking of contracts.
Conclusions
Fomo3d’s frenzy and 0xa169’s cool rapacity let us better understand the limitations of both Ethereum as a public blockchain, and its current generation of smart contracts. Fomo3D shows that the POW consensus algorithm which limits the transaction throughput and scalability of Ethereum, makes it easier for a malicious entity to subvert the network. Further, the complexity of smart contracts is a critical part of Ethereum’s security not being fully guaranteed. In response, as a next-generation public blockchain infrastructure, Penta is developing a unique DSC consensus algorithm, PSG sharding model and PDW to successfully meet similar challenges, to further improve blockchain performance, scalability and security.