Make a Forensic Copy of a File/Disk(Forensics-101)
In this hands-on tutorial you'll learn how forensic professionals make a forensic(bit-by-bit) copy of a file or hard disk. These same techniques are also used by the US military. There are several reasons you may need a forensic copy of an item. Some of these reasons can include:
- if you need to go to court and present the item as evidence
- if you want to probe around a hard drive without altering any of the data
- if you've lost your encryption keys but want to have an exact duplicate that you can later attempt to crack.
Though there are other very important considerations when collecting forensic evidence which I will cover in a later post, by following this easy method you will be able to quickly and safely accomplish all of the above. Let's get to it!
Prerequisites:
- a Linux virtual machine(go here to learn how to create one)
- dc3dd which you can install by going to terminal and typing the following: sudo apt-get update && sudo apt-get install dc3dd
- A file or disk you want to make a copy of.
Creating Forensic Copies
First we need to cover what the various options mean when running dc3dd. These options are:
- if= is the file/disk you want to copy
- hof= is the name of the hashed output file(aka name of file you want to create)
- hash= the type of hash you want to use; i.e. md5, sha-256, etc... (this is vital as it shows the file is an exact copy)
- log= location of log you want to create (this makes sure all activities/any errors are recorded and is vital for forensics)
- verb= determine whether or not to show you current progress
Creating a Forensic Copy of File
For example I have a file named "evidence-file" in my current directory and I want to create a forensic back up in the folder "forensic-copies". I would simply type the following:
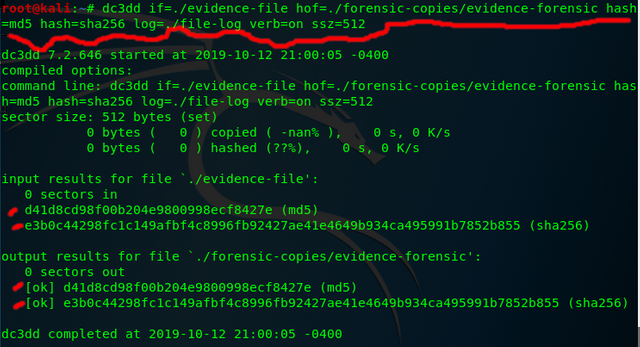
- dc3dd if=./evidence-file hof=./forensic-copies/evidence-forensic hash=md5 hash=sha256 log=./file-log verb=on ssz=512
You will do the same except change if= & hof= to the input/output files you desire. If successful it should look like the below. Notice how the MD5 & SHA256 are identical on the input and output file meaning we have a forensic copy.
Creating a Forensic Copy of Disk
You can create a copy of both partitions and full disks. You can do this with any type of disk(HDD,SSD, USB, etc...). You simply need to find what the partition/disk is labeled as. You can do this by typing in the terminal:
- lsblk
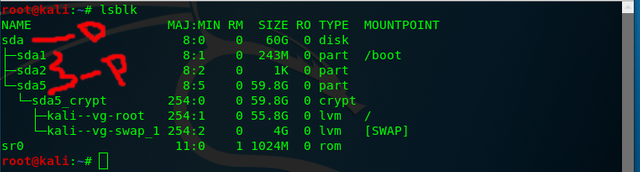
The item labeled "D" is a disk. The items labeled "P" are partitions on that disk.
Then you simply replace the if= to /dev/sda OR the appropriate disk/partition name. For example I have a whole disk I want to back up labeled "sda" and I want to back it up to a file name disk-forensic-image.img. The command would look like the following:
- dc3dd if=/dev/sda hof=./forensic-copies/disk-forensic-image.img hash=md5 hash=sha256 log=./file-log verb=on ssz=512
Conclusion
So there you have it we now have a forensic, bit-by-bit copy of a file or disk. I hope you enjoyed this tutorial. In future tutorials I'll cover how to analyze forensic data and Android forensics. If you have any questions or comments please leave them below and as always don't forget to upvote and follow to keep these tutorials coming.
Congratulations @hack-tha-world! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPDo not miss the last post from @steemitboard: