Enterprise VPN Network Design
This page tag is dedicated to my professional life as a network engineer and learner. I will just put computer network related things in this tag. This is my network journal.
I have been designing an enterprise VPN network for the company I have been working for. Network is pretty straight forward. The network has several branches across the country.
Each site is a logistic warehouse, connected to head-office via VPN. Users on each warehouse need to access the logisitc web-app running on the server at head-office. Web-app is locally developed. Web server is not exposed to public Internet.
There is also a monitoring server at the oversea office. Monitoring server needs to reach both hub and spokes. Not just that, monitoring server will determine the status of VPN and connectivity between hub and spoke. If there is connectivity problem, server will send alerts to administrator.
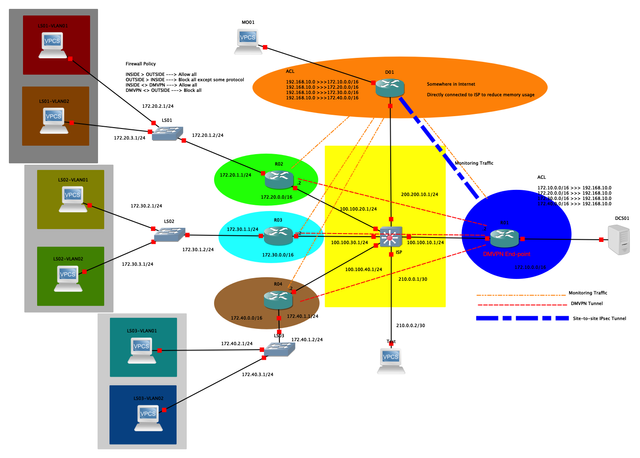
This is quite a simple setup.
- Branches and head-office are connected to public Internet.
- Branches are connected to head-office via DMVPN cloud. (Phase 2 or 3)
- Oversea office and HO has the site-to-site IPsec VPN connectivity.
- Monitoring server should be able to reach branches via HO router and through the DMVPN cloud.
- Zone-based Firewall is enabled on both HO and branches.
- Static route to monitoring server's IP is required next-hop pointing to Tunnel 0 interface.
I am not going to post the full configuration here as it is quite an easy setup but will put some key cheatsheets for DMVPN and ZBF.
DMVPN Hub
! Create an isakmp policy for DMVPN tunnel protection
!
crypto isakmp policy 10
hash md5
authentication pre-share
!
! Create an isakmp key for DMVPN tunnel protection
!
crypto isakmp key aps123 address 0.0.0.0
!
! Create IPSec transform-set
!
crypto ipsec transform-set APS esp-3des esp-md5-hmac
mode tunnel
!
! Create an IPSec profile for DMVPN tunnel
!
crypto ipsec profile aps
set security-association lifetime seconds 120
set transform-set APS
!
interface Ethernet0/0
ip address 100.100.10.2 255.255.255.0
!
interface Ethernet0/1
ip address 172.10.1.1 255.255.255.0
!
! Create GRE tunnel and apply IPSec profile to that tunnel
!
interface Tunnel0
ip address 192.168.1.1 255.255.255.0
no ip redirects
ip mtu 1440
no ip next-hop-self eigrp 10
no ip split-horizon eigrp 10
ip nhrp authentication aps123
ip nhrp map multicast dynamic
ip nhrp network-id 1
zone-member security DMVPN
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 0
tunnel protection ipsec profile aps
!
! Specify routing protocol for end-to-end connectivity
!
router eigrp 10
network 172.10.0.0
network 192.168.1.0
DMVPN Spoke
! create ipsec transform-set
!
crypto ipsec transform-set APS esp-3des esp-md5-hmac
mode tunnel
!
! create ipsec profile
!
crypto ipsec profile aps
set security-association lifetime seconds 120
set transform-set APS
!
! create isakmp policy
!
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key aps123 address 0.0.0.0
!
! create DMVPN Tunnel
!
interface Tunnel0
ip address 192.168.1.2 255.255.255.0
no ip redirects
ip mtu 1440
ip nhrp authentication aps123
ip nhrp map multicast dynamic
ip nhrp map multicast 100.100.10.2
ip nhrp map 192.168.1.1 100.100.10.2
ip nhrp network-id 1
ip nhrp nhs 192.168.1.1
zone-member security DMVPN
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel key 0
tunnel protection ipsec profile aps
!
! specify routing protocol
!
router eigrp 10
network 172.20.0.0
!
! This route is important for monitoring traffic
ip route 192.168.10.0 255.255.255.0 Tunnel0
!
!
ZBF
! create object groups for zones
!
object-group network DMVPN
172.10.0.0 255.255.0.0
172.30.0.0 255.255.0.0
172.40.0.0 255.255.0.0
192.168.10.0 255.255.255.0
!
object-group network INSIDE
172.20.0.0 255.255.0.0
!
object-group network OUTSIDE
192.168.10.0 255.255.255.0
!
! create zone
zone-security INSIDE
zone-security OUTSIDE
zone-security DMVPNzo
!
zone-pair security INSIDE-OUTSIDE source INSIDE destination OUTSIDE
!
zone-pair security OUTSIDE-INSIDE source OUTSIDE destination INSIDE
!
zone-pair security OUTSIDE-DMVPN source OUTSIDE destination DMVPN
!
zone-pair security DMVPN-OUTSIDE source DMVPN destination OUTSIDE
!
zone-pair security DMVPN-INSIDE source DMVPN destination INSIDE
!
zone-pair security INSIDE-DMVPN source INSIDE destination DMVPN
!
! apply zones to interface
!
interface Ethernet0/0
zone-member security OUTSIDE
!
interface Ethernet0/1
zone-member security INSIDE
!
interface Tunnel0
zone-member security DMVPN
!
! create ACL
!
ip access-list extended DMVPN-INSIDE
permit ip object-group DMVPN object-group INSIDE
ip access-list extended DMVPN-OUTSIDE
deny ip object-group DMVPN any
ip access-list extended INSIDE-DMVPN
permit ip object-group INSIDE object-group DMVPN
ip access-list extended INSIDE-OUTSIDE
permit ip object-group INSIDE any
ip access-list extended OUTSIDE-DMVPN
deny ip any object-group DMVPN
ip access-list extended OUTSIDE-INSIDE
permit ip any object-group INSIDE
!
! create class-map
!
class-map type inspect match-all DMVPN-OUTSIDE
match access-group name DMVPN-OUTSIDE
class-map type inspect match-all OUTSIDE-DMVPN
match access-group name OUTSIDE-DMVPN
class-map type inspect match-all INSIDE-OUTSIDE
match access-group name INSIDE-OUTSIDE
class-map type inspect match-any OUTSIDE-INSIDE
match protocol ssh
match protocol telnet
match protocol snmp
match protocol smtp
match protocol ftp
match protocol isakmp
match protocol icmp
class-map type inspect match-all DMVPN-INSIDE
match access-group name DMVPN-INSIDE
class-map type inspect match-all INSIDE-DMVPN
match access-group name INSIDE-DMVPN
!
! create policy map
!
policy-map type inspect OUTSIDE-INSIDE
class type inspect OUTSIDE-INSIDE
inspect
class class-default
drop
policy-map type inspect OUTSIDE-DMVPN
class type inspect OUTSIDE-DMVPN
class class-default
drop
policy-map type inspect DMVPN-OUTSIDE
class type inspect DMVPN-OUTSIDE
class class-default
drop
policy-map type inspect INSIDE-OUTSIDE
class type inspect INSIDE-OUTSIDE
inspect
class class-default
drop
policy-map type inspect DMVPN-INSIDE
class type inspect DMVPN-INSIDE
inspect
class class-default
drop
policy-map type inspect INSIDE-DMVPN
class type inspect INSIDE-DMVPN
inspect
class class-default
drop
!
! apply policy map into zone-pair
!
zone-pair security INSIDE-OUTSIDE
service-policy type inspect INSIDE-OUTSIDE
zone-pair security OUTSIDE-INSIDE
service-policy type inspect OUTSIDE-INSIDE
zone-pair security OUTSIDE-DMVPN
service-policy type inspect OUTSIDE-DMVPN
zone-pair security DMVPN-OUTSIDE
service-policy type inspect DMVPN-OUTSIDE
zone-pair security DMVPN-INSIDE
service-policy type inspect DMVPN-INSIDE
zone-pair security INSIDE-DMVPN
service-policy type inspect INSIDE-DMVPN
!
Congratulations @andyap! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click here to view your Board of Honor
If you no longer want to receive notifications, reply to this comment with the word
STOPDo not miss the last post from @steemitboard:
@andyap, thank you for supporting @steemitboard as a witness.
Click on the badge to view your Board of Honor.
Once again, thanks for your support!
Do not miss the last post from @steemitboard: