IoT: Went to Watch Black Mirror, Found Myself on an Episode.
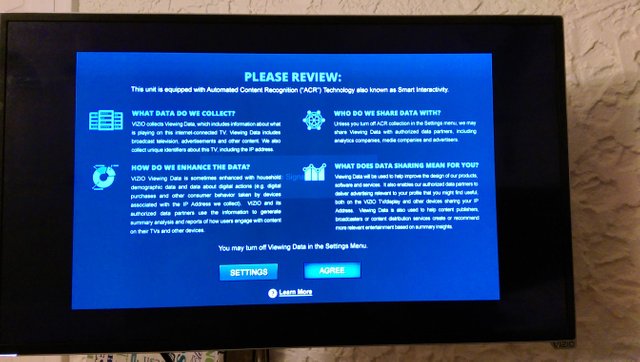
I had heard about the encroachment of IoT (Internet of Things) in the household but had yet to experience it myself. After writing my last post I turned on our "smart" TV to veg out for a minute. Upon turning on the TV I was hit with the above.
What do we collect?
Who do we share data with?
Now mind you we have had the TV for going on two years now. This makes the situation even more alarming to me, an update was pushed that lead to this prompt. The manufacturer must have decided to generate some more revenue from already sold merchandise.
Why is this such a big deal you ask?
Because the rules can change at any moment with or without your knowledge. Lets say this first roll out too many people opt out and they do not make their goal. I am sure they will push another update either to enable the data collection and not tell you. Or they have the option to change the wording to make it seem like you have said no when you have actually said yes. Too hard to believe you say, well check out my post on Microsoft regretting tricking their customers.
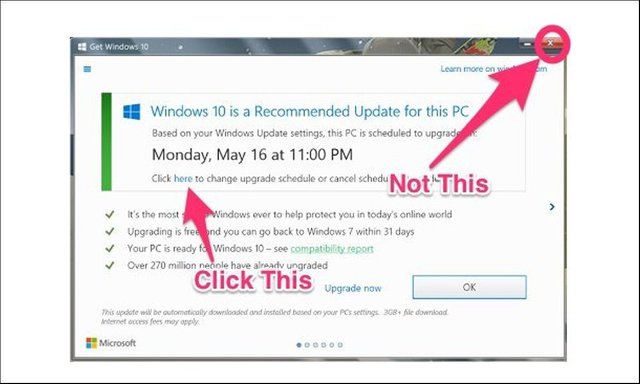
The above is the worry assuming that only the manufacturer can update your device. That is not the case, if they can get in, than anyone with the know how can also get in. With my TV this is not that big of deal because there is no camera or microphone that I am aware of. I have seen some schematics of cable boxes with microphones added. Oh, and how convenient that some TV's have voice command features. Let that sink in for a minute, yes those TV's can be listening in on your private conversations.

The device could also be compromised to use in an effort to gain access to the other devices on the network. If you typed passwords on the device for Netflix or Youtube it may be possible to capture that information to use in some way. I personally consider the actions of the manufacturer to be just as bad though.

I have a couple of raspberry pi's and I may take this TV offline. With the pi's I will have a little more control over the updates and I can almost guarantee there will be no personal data collection. Not going to do any P2P streaming with it though, I have heard a bunch of people bragging about using hacked fire sticks. If only they were aware of how many individuals they were giving their IP address to.
I wrote this post in hopes to bring awareness to the development of IoT and the possible breach on personal information it may cause. Everything is being put online, and I mean everything. This is not a preventable evolution but being aware will help when it comes time to enable or disable auto updates. Unfortunately my TV does not have the option to disable updates, taking it offline is my only option.
Let me know what you think in the comments or your personal experiences with IoT.
Thanks!





This is why I would really like competition. Real competition, not the same manufacturer making all the different brand names.
These makers of govern-cement spy-ware for the home should have been put out of business.
Furthermore, with all of our advances in technology, we have failed to do the most important thing, make the computer a good tool.
Currently, Winderz is not an OS, it doesn't show you all of the running processes and doesn't allow you to kill them at your command. If you have a known virus, you can't tell winderz to kill it. You can ask politely.. to which, most viruses will say, no.
A computer does not easily tell you what it is doing. That is the important part of a good tool. It is apparent what it is doing.
A phone should tell you if its microphone or camera is being used, and by which applications. It doesn't do either.
And don't get me started on the poor state of security. Why are we still using passwords?
Awesome comment! Gave you a follow. I agree 100% with your comments and feel that the next eight years is the time to push that agenda. The presidency is starting on a net security theme so it will be a buzz word for a while. It also needs addressed, let me know if you make a post on the subject. Would be interested in you solution to passwords.
The solution to passwords is the same as the solution for verifying a person, is the same for knowing who your friends are.
Why do we still have cell-phone numbers? Why do we still have email addresses? Our computers should be smart enough to call Bob, or send Bob a message. It could easily be done with nested public/private keys. But we don't have a stay linked protocol yet. Bob gets a new phone or server and that information is pushed to all of his mates.
Been having a lot of Bitcoin conversations lately and people say the don't trust it because it is electronic money with no value. I simply ask if they use credit or debit cards and they get that puzzled look on there face when they realize they already use electronic money.
I like the concept but this is the transition from analog(life) to digital(computer). Did you have a method in mind for creating and storing these public and private keys? I feel a bit behind on these concepts, I am curious how Bob would navigate this world with no passwords.
Humans are not designed to store multiple passwords.
So, anything that uses a password to allow an individual access has access to a password that is common for many other such devices. Just one of those devices has to fail in its security for the password to become known to someone outside. And then the entire chain of security fails.
We all know this scenario.
Something needs to be invented, and something will be. Where the computational device recognizes you. The thumbprint identifier is stupid, but may be a step in the correct direction. But, I can tell more about you by the way you swipe the screen, which icons you go for first, how fast you type. All of these could be used to identify you, or identify not you.
The way the public/private keys work. Mathematically, you create a lock, and so you have the lock and the key. If you have the lock (say on your door) and you give out the key to your friends, only your friends can enter that door. (those are public keys) The private key is like the key to the lock of safe in your house. And this safe has a drop slot. So, your friends come over, use their public key to enter your house and drop a message into your safe. You come home and use your private key to open your safe and read the messages.
So, now you know only your friends are dropping you messages, and that you are the only one who reads them.
At a meeting of you and Bob, you will pull out your computational device and trade contact information. Currently we do this as a long string of incomprehensible letters such as [email protected] or 714-555-1212. We hope that no one guesses these long strings, else they can harass us. A computer can make up a longer incomprehensible string and trade that with another computer. Then, its even harder to guess. All you have to do is have an application that talks to the other computer and trades locks and keys. Then you have to place a human identifying mark on the lock/key pair you have... such as "Bob" and then you can use that to always contact Bob.
It is a really simple concept, but right now difficult to do on internet 2.0, but someone will come up with some fix/application/protocol. Internet 3.0 will have this built in.
I am fully on board with this, ConsenSys was working on an identity system I believe if you want to check them out.
I've worked for cable companies for many years and they have access to a lot of behavioral data through the boxes, I as a simple phone representative did. They can tell just how many times you rewinded that particular PPV scene...
This was many years ago and back then when the boxes were being rolled out because some analog signal was coming off I remember that having access to that kind of information was scary to me, that someone could know exactly what I was watching and what my preferences were.
Anyone that can collect data about you will or is already doing it because information is valuable. I try to keep it in mind without going too crazy with it because now phones have a front and back camera and I watched Person of Interest, hahaha. The perfect surveillance is the phones, even if in your pocket unable to use its eyes, it has ears too and they are traceable by GPS.
Oh yea, the surveillance is real. Thank you for the insights on your experiences as an employee of a cable company. The only internet app we use on that TV is Netflix and they keep a record of your viewing history so I saw no advantage to enabling the collection feature. I recall a bunch of convo when pokemon go came out about how they were using that game to map the real world for Google. I liked what @builderofcastles said about seeing what was running and what it was doing, that would go a long way in preventing unwanted surveillance.
Been seeing alot of chatter about vizo tvs being used to spy on us
Any documentation on that?
I just assumed it was probably true and didnt look it lol it was all twitter chatter
Been worried about similar issues thinking besides the raspberry pi another method would take setting up routing tables a second Wi-Fi network just for things like your tv. Or route it through a computer to prevent you personal data from being sent out. Let's say only allow the tv to connect to Netflix nothing else. I think a network inside of a network is the way to go then your home iot devices are on one network tv and media devices on another network and computers and everything else on another just a thought I have considered not sure how practical it really will be though.
For the end user that is not practice at all given what you just wrote is a foreign language to some. However bundle the services you just mentioned into a nice little package and you have a product. A router with the option to add IoT devices with their stated purpose. Those categories would have a set of common IP addresses unlocked. I would personally purchase something like that and I am sure there is a tinfoil hat market for it.
lol Your probably right there, bet there would be a market for it, but then you would need to know addressing and such or outside control would be needed so I don't see much of a practical way of doing it either.
Remote access would be a must, or just scheduled IP updates. You could always just run your own DNS and have it connect through that.
True that might be the easier way.
Now you would have a single point failure. Figure how to put it on the Blockchain. ;)