Meltdown and Spectre -Everything you need to know {Part 1}
Improving the speed relates to either improving the operating system with regards to how it schedules processes and manages memory or improving the design of the powerful computer chips on which the operating system run. Keep this in mind.

Now before we can understand what and how Meltdown and Spectre works we first need to understand how the operating system, in general, work.
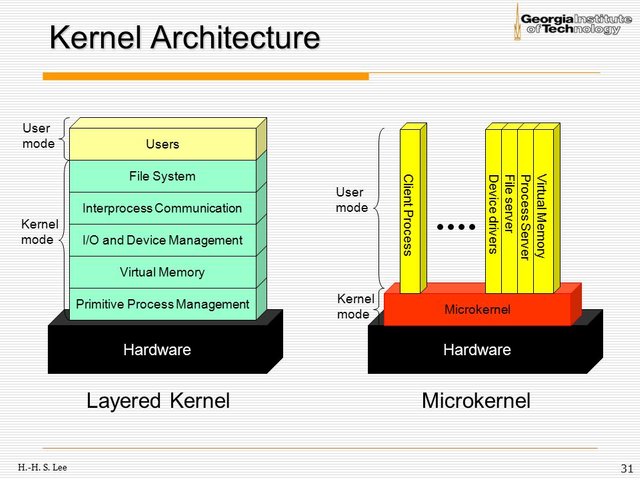
A basic operating system consists of two modes:
User Mode
User mode is typically the place where programs and user-level threads are run. They have no means to access hardware directly or make references to memory what so ever. The only way a switch from user mode to kernel mode can take place is if the program issues a system call which triggers and interrupt. This switching process adds a lot of overhead and is not something you want done often if you have performance as a goal in mind.Kernel Mode
In Kernel mode( also called system mode), privileged instructions may get executed because in this mode programs and threads have access to the hardware. The operating system can reference any memory location in this mode. Crashes in this mode can have severe consciousnesses.Before the scheduler can assign a job to a processor the processes need to be assigned into main memory. The Kernel decides which memory can be accessed and which memory is for the operating system and is not available to the rest of the system.
Meltdown does not exploit the software instead it relies on the disadvantages of using dynamic execution(also known as "out-of-order execution. )
Out-of-order execution is an optimization technique that allows to maximize the utilization of all execution units of a CPU core as exhaustive as possible.
source
Now this is where improving processing speed created these flaws. Dynamic execution(DE) uses algorithms to anticipate where in memory the next instruction is located. Next up is a process known as Speculative Execution, which if done correctly greatly increases performance on devices, but this is the root problem that Meltdown originated from.
Speculative Execution is where the OS looks ahead of the program counter, which indicates at which instruction it is currently at, and executes instruction that might be done at a later stadium.
In layman's terms , Meltdown breaks the barrier between Kernel and User mode which allows privileges to the program like accessing system memory. Because of Speculative Execution the program can load privileged data from memory despite being classified as unprivileged and in User Mode.
This vulnerability not only allows attackers to see kernel memory but they gain access to the whole physical memory mapped in the kernel. Stealing your information and passwords... Is as easy as dumping your device's memory like in the following video.
One distinction between Meltdown and Spectre is
notably that Spectre requires tailoring to
the victim process’s software environment, but applies
more broadly to CPUs and is not mitigated by KAISER.
source
Luckily this means that there are patches on various platforms for this vulnerability. But Spectre still remains even with Meltdown out of the way.

Stay tuned for part 2 where I discuss the more severe vulnerability of the two
You can read more about this here
nice article about these 2 security bugs
@dimitar Thank you , follow me and stay tuned for part two. It takes awhile to write because there is so much information and I try to make the posts short.
yes. I followed you. thanks for your work