How to acquire a memory image for later analysis!(Forensics)
Why do we want to get a systems memory for later Analysis? Let‘s say you had an incident on a machine in your network and you suppose you have been „hacked“. A memory dump is a great way to see all the processes and the loaded DLL‘s and to analyze the machine and what was happening at the time of the capture.
The dump can later be analyzed with rekall or volatility.
Loadable Kernel Module:
A Loadable Kernel Module is a module that can be inserted into the kernel to extent the kernels functionality. In Linux Kernel Modules have the extension .ko which stands for „kernel object“.
Typically LKM‘s are used for programs like hardware drivers.
You can view the loaded modules with lsmod in the terminal.
Acquisition in Linux:
In Linux we can use a tool called LIME for the Acquisition of a memory image. LIME is an open source command line tool and works as a loadable kernel module(LKM).
First you need to get LiME via the following command and navigate to the directory and run the make command
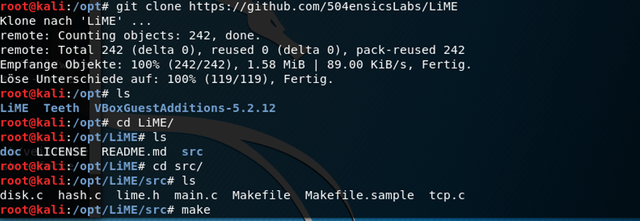
Now the module is being built on your system. You can also use external builds if you don‘t want to touch the targets harddisk. You can read about the external building here
After buildig the Kernel Module we have to type the following to acquire an image of the current memory.
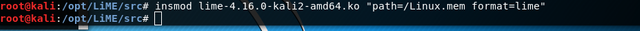
insmod – insmod is the program to load a module to the kernel
lime-4.16.0-kali2-amd64.ko – that‘s the name of the module we want to use
path=/Linux.mem - the location of the dump
format=lime – specifies the format of the dump; other options are „raw“ and „padded“
Acquisition in Windows:
In Windows we can use a tool called FTK Imager which is a program that comes with a GUI. Dumping memory with ftkimager is a very straight forward process.
Just open Ftkimager and click on the following and go to capture memory
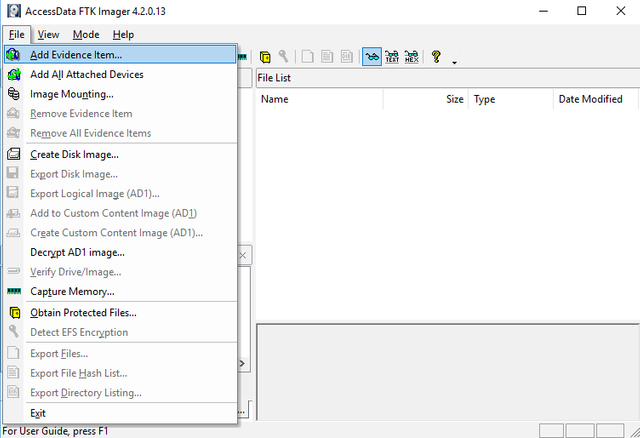
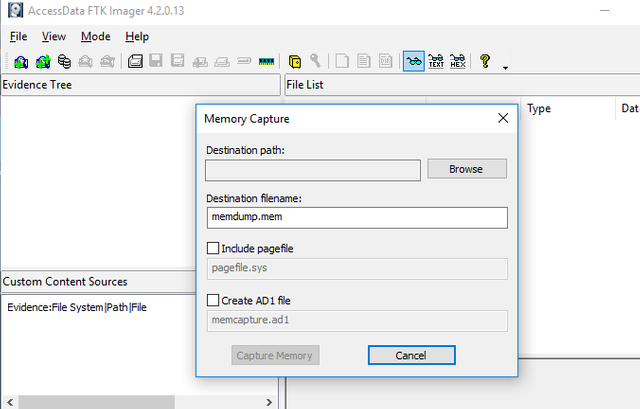
After that you‘ll find the following screen. Here you have to give ftkimager a location for the dump.
Acquisition in Windows over the command line:
There is a tool called winpmem.exe which belongs to the Rekall Suite.
With winpmem you‘ll have to open the command line as adminstrator and type the following.
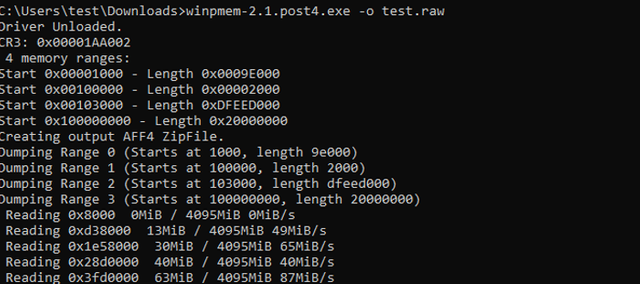
or you can run
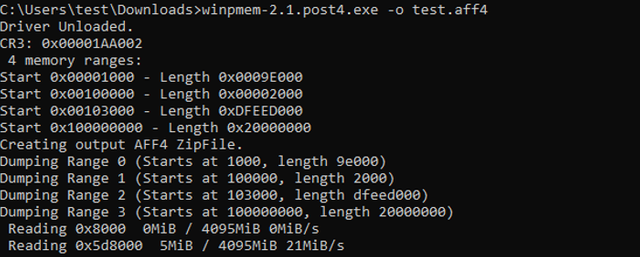
which‘ll give you an aff4 compressed image.
So that's it for today. Soon we'll look a little bit into analysis of such an image.
I followed you and upvote you, follow back @hammad41
Very helpful, thanks for sharing!
Posted using Partiko Android
Looks like a good oversight of tools! Thank you!
Nice Work !