Tutorial Penetration Tools #3 || How to Find Website Vulnerability using Nikto on Kali Linux 2 || Bagaimana mencari kerentanan website menggunakan Nikto di Kali Linux 2

What is a Nikto..?
Nikto is a most popular web security app when you start a web pentesting. Nikto is a web application scanning tool that searches for configuration errors, open access web directories and number of web applications. Nikto is an Open Source web scanner (GPL), which performs comprehensive tests on web servers. Nikto has the ability to detect 3500 potentially dangerous / CGIS files. Nikto can test web server quickly, but it's easy to see on the log. But it is very useful to test a web server. I think this nikto web server reader that has a vulnerability of CVE and OSVDB (Open Source Vulnerability Data Base).

Nikto Functions :
Nikto is an Open Source (GPL) web server scanner that performs comprehensive tests on web servers for multiple items, including over 6700 potentially dangerous files / CGIS, checks for outdated versions of over 1,250 servers, and certain version issues in over 270 server. It also checks server configuration items such as presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be updated automatically.
Features
These are some of the key features in the current version:
- Support SSL (Unix with OpenSSL or maybe Windows with ActiveState's
- Perl / NetSSL)
- Full HTTP proxy support
- Check out obsolete server components
- Save the report in plain text, XML, HTML, NBE or CSV
- Scan multiple ports on a server, or multiple servers via input files (including Nmap output)
- Identify installed software through headers, favicon and files
- Host authentication with Basic and NTLM
- Scan tuning to enter or exclude all consumer class checks
- The upgrades are composed of several methods: headers,
- Save request / full response for positive test
- Maximum execution time per target
Tutorial using Nikto at Kali Linux 2
Open your linux terminal and make sure your computer is connected to the internet to penetrate the target website.
Then open Nikto app in Kali Linux then follow the following command :
Applications ->> Vulnerability Analysis ->> nikto
first open terminal in linux time, then type command :
nikto
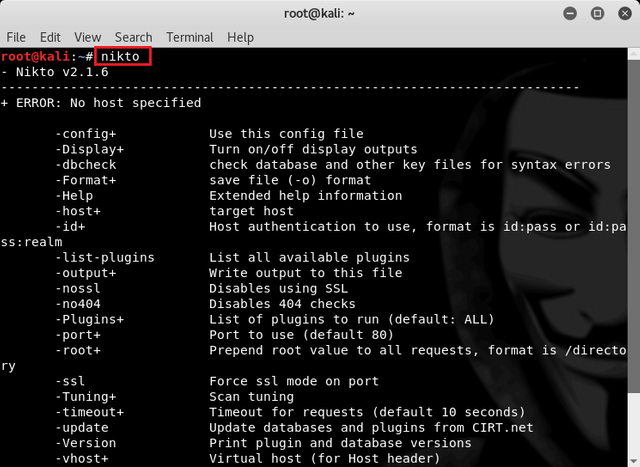
then next comes some options that can be used on nikto
Note :
Then we determine the website that we will test the vulnerability, for example here using the website "www.yahoo.com" which we test as learning about knowledge vulnerability analysis of a website.
Then to scan the website with the host name we can use the -h option by typing the command :
nikto -h www.yahoo.com
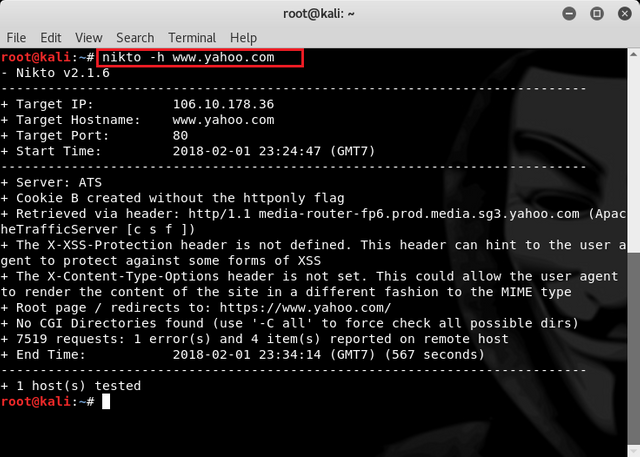
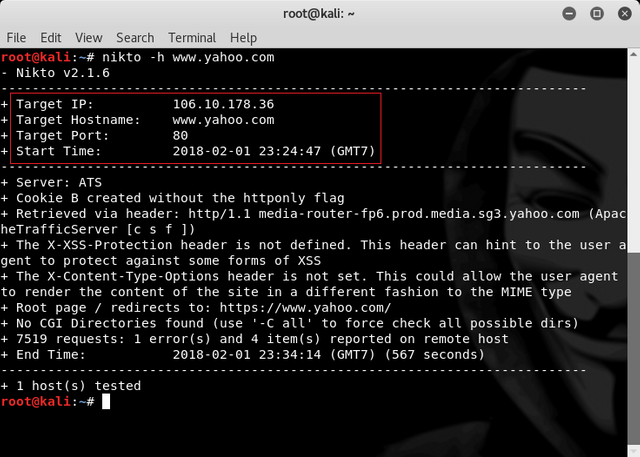
Then we wait until the scan is complete and then we can see find some information about the target that is : Target IP, Target Hostname, Target Port and Start Time.
Target IP : 106.10.178.36
Target Hostname : www.yahoo.com
Target Port : 80
Start Time : 2018-02-01 23:24:47 (GMT7)
Then to scan the vulnerability we can see the running process we need to use the Display option by typing the command :
nikto -D v -h www.yahoo.com
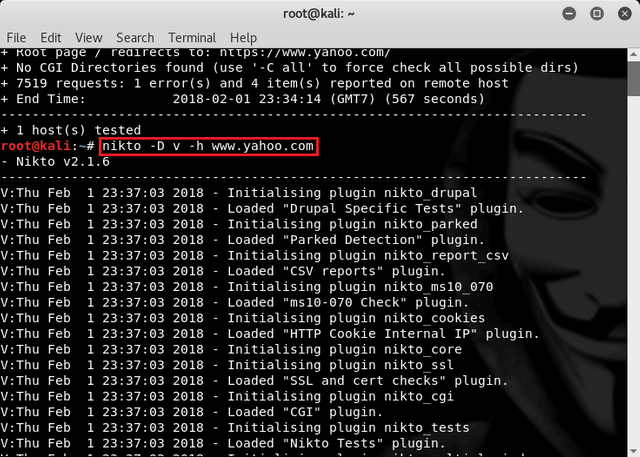
Then on this display we can see all the processes that are in progress and need a long time until the process is complete.
After the process is complete we can see how long it takes to do the scanning and in this process takes (612 seconds) to complete the scanning process.
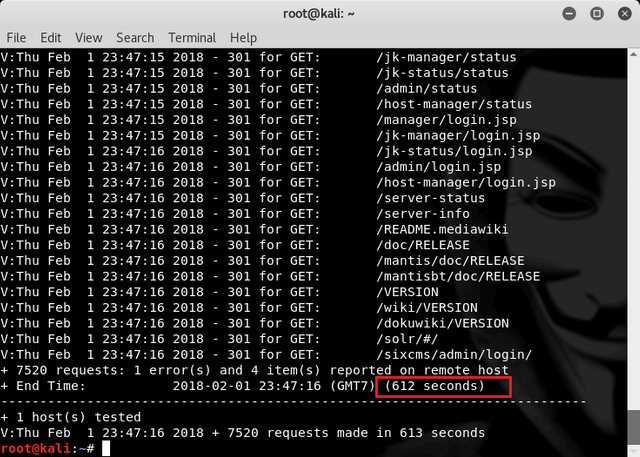
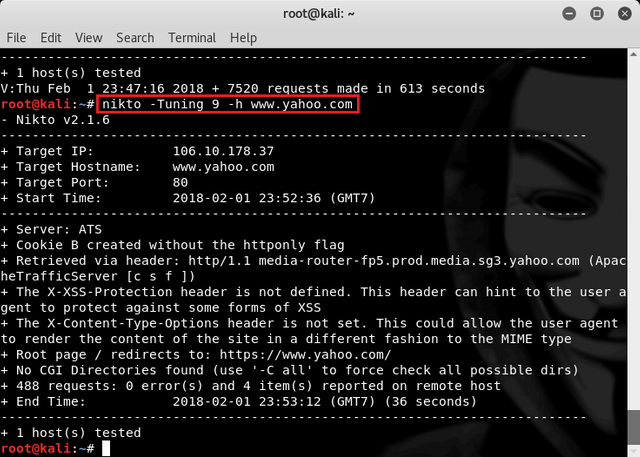
Next to scan for SQL Vulnerability for a website. We can do a single scan can be completed with a fast time by typing the command :
nikto -Tuning 9 -h www.yahoo.com
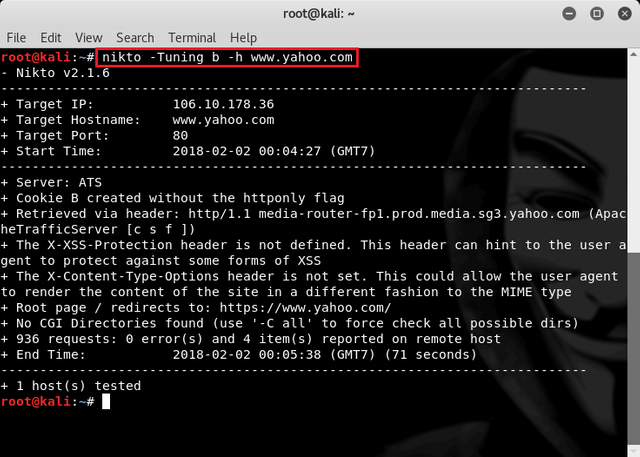
Next to scan the software identification on a website we can type the command :
nikto -Tuning b -h www.yahoo.com
Next to scan Denial Distribute of Services (DDoS) on a website we can type in the command:
nikto -Tuning 6 -h www.yahoo.com
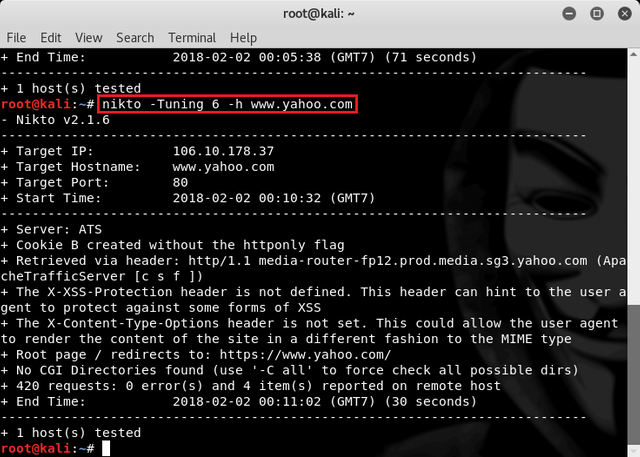
Then to scaning results can we save on file by using command below to find the vulnerability.
nikto -Display V -o nikto_scan_result.html -Format html -h 106.10.178.37
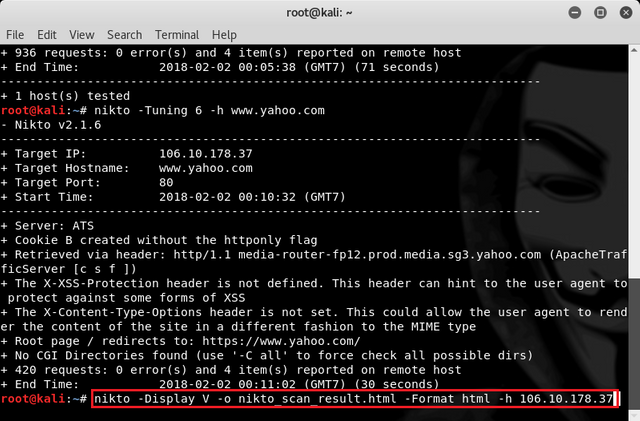
Then wait until the process is complete. Furthermore, when it is finished to see the file we can type the command :
ls
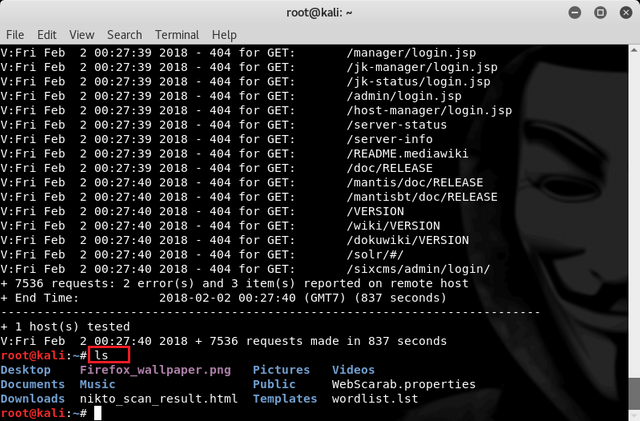
Then we find the file named nikto_scan_result.html
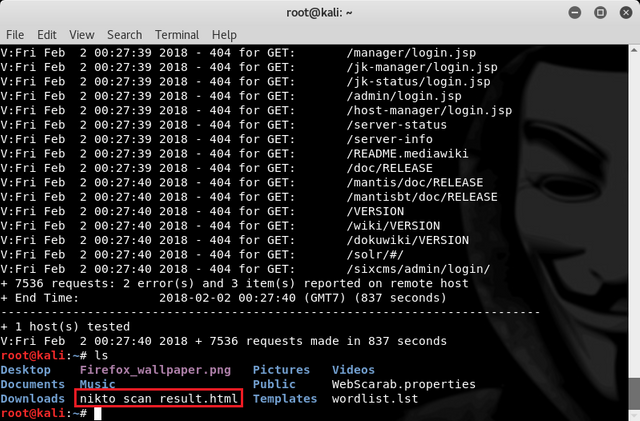
Then to open the file we go to folder /Home and click on file: nikto_scan_result.html
Home ->> nikto_scan_result.html
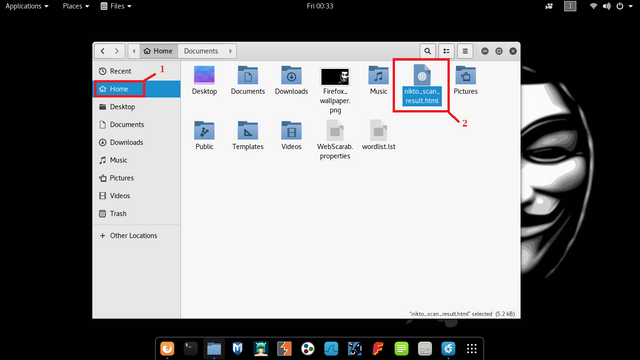
Finally, that open nikto_scan_result.html in our browser and we can see the full results of vulnerability scanning website we have done.
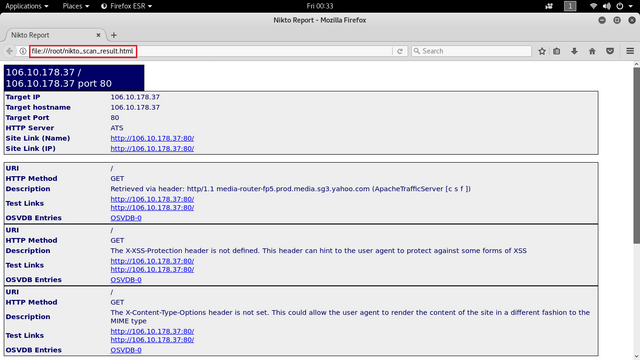
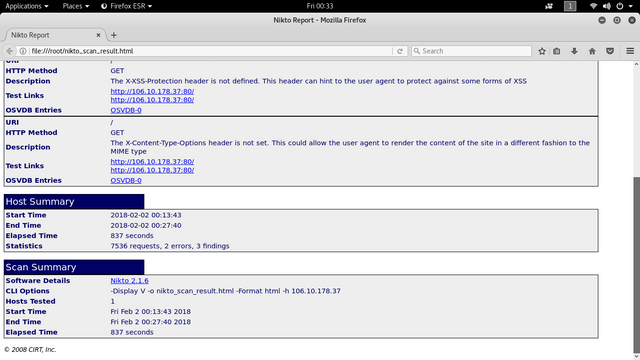
Syntax Description :
-Tuning : Scan Tuning
-D : Display
-h : Hostname
v : Virtual Host (for host Header)
V : Print plugin dan Database Version
b : Tuning to Software Identification
9 : Tuning to search for sql vulnerabilities
6 : Tuning to scan Denial Distributed of Services (DDos)
Posted on Utopian.io - Rewarding Open Source Contributors
Hello @fandimuhammad11 your post looks awesome.
Thank you for the contribution. It has been approved.
Maybe you should consider keeping your titles just in English, which is not mandatory but makes a lot of sense in my personal opinion. It would also be useful to add the difficulty of your tutorial to the introduction as suggested by our template so readers can decide right away if this is helpful to them or not.
You can contact us on Discord.
[utopian-moderator]
thanks @flauwy next i will make better contribution
Hey @fandimuhammad11 I am @utopian-io. I have just upvoted you!
Achievements
Suggestions
Get Noticed!
Community-Driven Witness!
I am the first and only Steem Community-Driven Witness. Participate on Discord. Lets GROW TOGETHER!
Up-vote this comment to grow my power and help Open Source contributions like this one. Want to chat? Join me on Discord https://discord.gg/Pc8HG9x