PHP Security : Cross Site Scripting
What Will I Learn?
In this tutorial, We will be learning about what is cross site scripting and how create a filter to prevent xss attack. Cross site scripting is very common bug in most of websites. Some of companies eg. Google, Facebook, Yahoo etc give bounty to reporter.
Requirements
- WAMP/MAMP/LAMP/XAMPP or any other PHP/MySQL web stack package
- Notepad++/Sublime
- Basic knowledge on HTML, PHP
Difficulty
- Intermediate
What is Cross Site Scripting?
Injecting javascript into a website to steal user's cookies or any other credential to get control on any particular victim's account is known as Cross Site Scripting, It is also known as XSS.
Types Of Cross Site Scripting :
Stored XSS
In this type of XSS, Javascript payload will be stored in any particular page and whenever any user try to open it, Then all data which is saved in its cookies will goes to attacker. For example, We have a blogging website, which don't have any filter against XSS. Attacker will add
<script>alert(document.cookies)</script>
this in his blog and this code will show you popup with visitors cookies. So as you know by the name script will stay stored in a page, where attacker inserted that above javascript.
Reflected XSS
In this type of XSS, Code doesn't stored in page as we learned in stored xss. As we can see in example below, Attacker add javascript code in q parameter. Attacker will send it to victim in email or anywhere else. Attacker will make victim to click by wrapping URL in tag
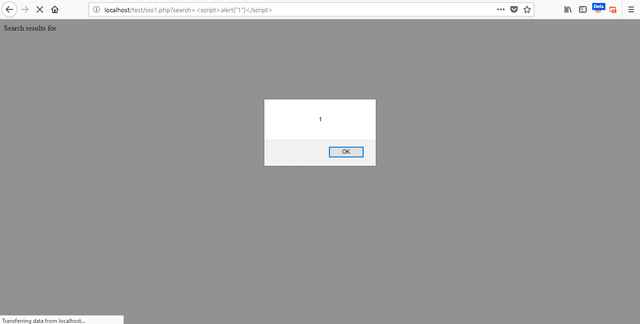
DOM based XSS is totally different from above two type. It is mainly based upon DOM. So it means we can use it only in DOM. In this code, We have a variable $ search as well as a parameter name which is also search. The method we are using is GET. When we execute this code, it will like this But there no any kind of restriction in this code to filter the xss or any other injection. So if attacker add < script >alert(1) </ script > in parameter of search. Then result will be In this code, We have add filter which is htmlspecialchars and **ENT_QUOTES **will convert all double and single quotes into plain text. Unrecognized character-sets will ignore and replace with its UTF8.https://example.com/news?q=<script>alert(document.cookies)</script>
DOM Based XSS
PHP Normal Code
<?php
$search = $_GET['search'];
echo 'Search results for '.$search;
?>
URL : http://localhost/xss1.php?search=Hello
Output: Search results for Hello
Filter to prevent XSS
<?php
$search = $_GET['search'];
$search = htmlspecialchars($search, ENT_QUOTES, 'UTF-8');
echo 'Search results for '.$search;
?>
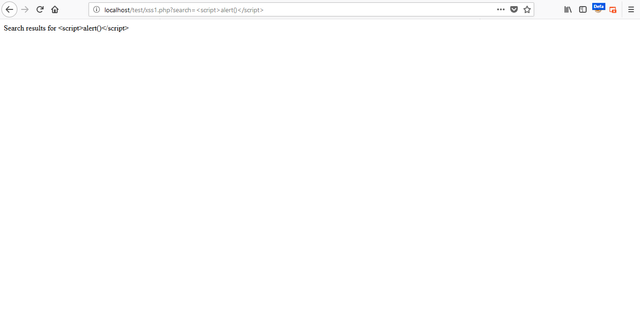
As we can see in output, All code will be execute in normal text. Any kind of code cant be execute till now. There more ways to prevent but the best way to prevent account to me and php development website is this. No one can bypass this filter till now.
Posted on Utopian.io - Rewarding Open Source Contributors
Your contribution cannot be approved because it is not as informative as other contributions.
My opinion:
See the Utopian Rules. Contributions need to be informative and descriptive in order to help readers and developers understand them.
You can contact us on Discord.
[utopian-moderator]
Hey @portugalcoin, I just gave you a tip for your hard work on moderation. Upvote this comment to support the utopian moderators and increase your future rewards!
Hey @karannanda that is a really nice tutorial. Of Course, it is short, but I think the Reader can read it fast and understand what you are saying here.
Well done.
Looking Forward to more tutorials :)