What is Metasploit Framework? How to Install? General Command and Concepts #1
What Will I Learn?
- What is Metasploit Framework?
- How to Install?
- General Command and Concepts
Requirements
- Linux Operating System
- Metasploit Framework
Difficulty
- Advanced
What is Metasploit Framework?
Metasploit is an open source penetration testing tool developed for security testing. Ruby is encoded in the language and has a practical interface and rules. It contains over 1000 exploits. Metasploit contains many parameters and modules for easy use of exploits and other tools.
It provides convenient use when performing safety tests on this site. If any exploit is coded for Metasploit, it can be used and improved by adding it inside. With Metasploit, simple web security tests and managed tests on operating systems (Windows, Linux, Android, etc.) can be applied. Information is gathered from the system, the acquired information is exploited, and then the system is tracked for progress and persistence. Of course, this is something that the person doing the security test will have to do. The crucial point is that it can be used for many purposes, not for a single purpose. The user identifies the operations to be carried out and forms their own test strategies. This can be done in a practical and quick way.
Metasploit has its own file system:
| Data | Data is used and can be changed by metasploit. |
|---|---|
| Lib | The main structure of the system that makes up the Framework is the library. |
| Plugins | Plugins that work automatically and function using all the features of the Framework. They work during the process. |
| Tools | These are tools that work on their behalf and work on command lines. |
| External | External resources are 3rd party software and source codes. |
| Documentation | Documents used to inform the Framework. |
| Modules | Normal modules. |
| Scripts | Advanced scripts like Meterpreter |
These may be reproduced. As you can see, metasploit architecture works fairly regularly. To understand these terms in full, it is necessary to use the stated facts. In this way you can produce strategies according to the process.

How to Install?
Metasploit can work on many platforms. For example, Mac, Windows and Linux. With these options, each user can address and make comfortable use. I use Linux and I will show you how to install and use it in Linux because I am more dominant. You can perform operations on Windows or Linux. I recommend Linux for convenient and practical use.
Installation for Linux:
Since I use the Lubuntu operating system, I will show you how to install it via Lubuntu, but most linux distrars have the same structure. If you are using operating systems such as Kali Linux or Backtrack Linux, the Metasploit Framework comes pre-installed, but if you are reading this tutorial and you want to learn how to do it by following the steps in the series, it's a good idea to update it.
We enter the following commands in order;
sudo apt-get install curl
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall
chmod 755 msfinstall
./msfinstall
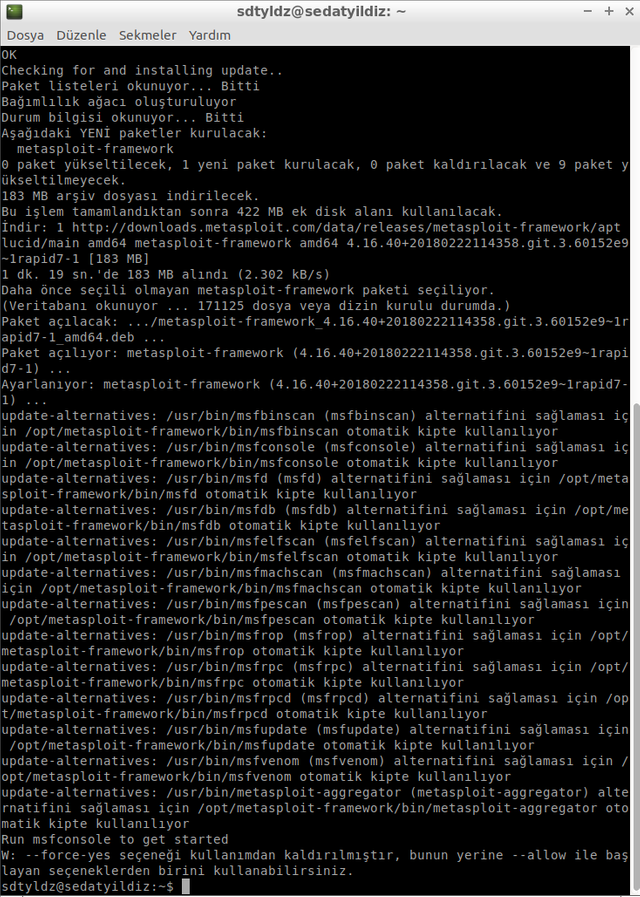
We have entered our commands in order and your installation process has been completed successfully.
General Command and Concepts
There are always commands to use in Metasploit. These commands will be used in many operations such as selecting an exploit, entering a parameter, and will always get confused.
The parameters vary according to the modules. If you follow the lessons you will know better as you use modules, I will explain from time to time to refresh this information. Since some concepts are long, we will briefly describe this introduction, and we will work in more detail later on.
Exploit Selection
The use command is used to select any exploit or module in the main metasploit window.
E.G.
use exploit/windows/smb/ms08_076_netapi
When the module is selected, it outputs exploit (ms08_067_netapi.
Selecting Payload and Lending of Payloads Suitable for Exploit
Payload is a module that is used to ensure that the system running after the exploit does not proceed and to perform the desired operations.
In general, when selecting an payload, an appropriate payload must be selected for the exploit. In other words, when Windows wants to perform an attack on a system, an appropriate exploit is selected for that system and a payload to be executed after the exploit is selected. Operating systems such as Windows, Linux, and Android have different payloads. Payloads can vary from system to system, as well as from exploits. We will process Payload in more detail in later courses.
Payloads can be used with exploits and usually also use remote exploits. The show payloads command lists all payloads that can be used with the selected exploit.
E.G.
With the command set PAYLOAD windows/shell_reverse_tcp we can choose our payload. When the system is exploited, windows/shell_reverse_tcp will switch to payload.
Getting to Know the Parameters
In order to run the explot on a system, some information about the target system and the target system should be entered into the exploit beforehand. You can use the "show options" command to see these parameters. The command will show the module at the top and the payload's parameters at the bottom.
| Name | Parametric name |
|---|---|
| Current Setting | The value entered for the parameter |
| Required | The place where the input is not mandatory. "No" is not required, if "Yes" it is necessary to enter |
| Description | The description of the parameter |
Parameters should be entered based on this information.
The first topic of our series has been completed here, thank you for reading. See you on the next topic, respectfully.
Posted on Utopian.io - Rewarding Open Source Contributors
Your contribution cannot be approved because it is not as informative as other contributions. See the Utopian Rules. Contributions need to be informative and descriptive in order to help readers and developers understand them.
You can contact us on Discord.
[utopian-moderator]
I do not think it is right to make a review like this, I wrote a detailed message on Discord.
I believe that this post is more about the general information and could be suitable for a person that does not know metasploit.
The information about installation is written in the documentation quite well and your post would benefit from including the links for other platforms even though you show it only for one distro.
You mention some of the commands but I feel that it is not really explained what we can do with them.
There are some passages where you repeat yourself or it is not clearly written.
It could be better if you were able to mention what the following part is going to be about. Afterall, you want to write a series.
Overall, I think that this post is not suitable for the reward right now.
Thank you for the detailed review @espoem
Hey @shreyasgune, I just gave you a tip for your hard work on moderation. Upvote this comment to support the utopian moderators and increase your future rewards!
@sdtyldz, Approve is not my ability, but I can upvote you.
If you are lazy you can use a distro like Kali that already has metasploit installed. All you need to do to start it is:
There should also be a docker container that you can download and run. If metasploit is too much of a learning curve for you then you should have a look at armitage.
Anyways nice article. Here are some bookmarks that I thought you might find helpful:
http://securitytube.aircrack-ng.org/SecurityTube-Metasploit-Framework-Expert/SMFE-Community.zip
http://www.securitytube.net/groups?operation=view&groupId=10
https://github.com/rapid7/metasploit-framework/wiki/
http://www.offensive-security.com/metasploit-unleashed/
http://netsec.ws/?p=331
Thank you for the information.