ISIS, Al Qaeda, using Media as a weapon
Author: Hani Chibli, a Syrian researcher in peace and conflict studies.
Through a theoretical framework based on the literature review and findings from academic literature, the overall objective of this paper is to answer the question:
How does the Islamic State (ISIS) recruit using Social Media?
According to Marshall McLuhan1, “it would be impossible for terrorism to exist without the media.” Terrorism is one of the most prominent forms of violence and crime in modern times as it threatens the security and stability of many societies. The terrorist acts have continuously developed over the years and now are characterized by high flexibility and ability to deal with social, international, and security changes, as well as by the capacity to adapt to new technologies. The notion that terrorists have benefited from the development of modern technology is evident by the fact that more than 80 percent of the recruitment operations carried out by ISIS have been accomplished through Social Media platforms2.
The link between terrorism and technology is what is referred to as cyber terrorism and dates back to the famous terrorist organization, Al Qaeda. Al Qaeda was the first jihadist organization that utilized the World Wide Web, and Osama bin Laden was the first terrorist to embrace Internet technology as early as 1997. Ayman al Zawahiri, the current leader of Al Qaeda, stated in 2005 that "we are in a battle, and more than half of this battle is in the media"3. This speech given by Ayman Al Zawahiri was the spark, the beginning of the emergence of the cyber-jihad that is raging today.4
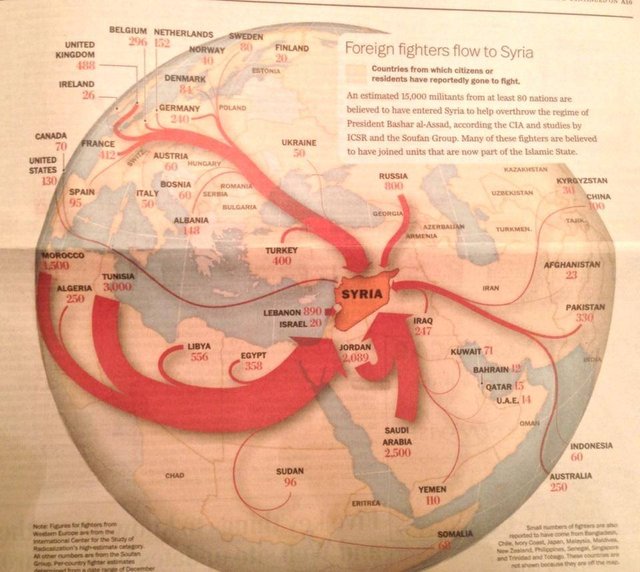
ISIS is the current famous terrorist organization that takes part in the new technology developments by adapting the most beneficial tactics available in cyberspace, "rise and defend your state from wherever you may be, keep plots small and straightforward, and involve as few people as possible" said spokesman Abu Muhammad al-Adnani to urge ISIS supporters. Terrorism carried out by ISIS has evolved to a new level, making efficient use of today's interactive and fast-paced social media platforms and other mobile apps. ISIS supporters are ardently tweeting, streaming, and Instagramming their exploits. Terrorism is now being transmitted across the globe in real-time within seconds. ISIS has broadly exploited blogs, instant messages, video sharing sites, Twitter, Facebook, Instagram, WhatsApp, Tumblr, and Ask FM. Their media strategies reveal that terrorism can be streamed and delivered with graphic images, audio messages, and music. Such forms of ISIS propaganda are a useful tool for psychological operations and recruitment. The Internet is the primary tool that ISIS has been using to lure and brainwash youths to join jihad under the Islamic state. Social media, with its cons, has been used with several destructive online strategies for successfully recruiting young people worldwide. According to a report, the UN estimates that about 15,000 foreigners have joined ISIS and many extreme Islamist groups that are based in Iraq and Syria 5. The report disclosed that these people came mainly from America, Europe, and Australia.
the Lone wolf strategy: ISIS has applied the Lone wolf strategy since September 2014 when Abo Muhamed al Adnani called ISIS supporters through a recorded message to endorse a new strategy6. The message encouraged newly radicalized individuals not to travel abroad but instead fight for ISIS in their home countries. According to Gabriel Weimann, ISIS inspires an individual, but he acts independently. This is without receiving any ISIS direction or support 7. Interestingly, the majority of the Lone wolves have never traveled abroad or even met any ISIS members. Dire consequences have been experienced globally as a result of the propaganda media messages by ISIS with many Lone wolf attacks that have been carried out since 2014.
The aim of this paper is not only to shed light on the recruiting strategies of the Islamic State but also to show on what premises they are built and how ISIS legitimizes its call for jihad, and what actors and tools are named and framed in their strategies. Further, the paper will explore the connection between Islamic State narratives, online radicalization processes, and online recruitment through Lone wolves.
There is a plethora of research dealing with cyberspace and its exploitation by terrorist organizations 8-9.
The number of recruits was then estimated at 20 thousand fighters as a result of high proficiency of the delivered propaganda tailored by ISIS media savvy.10 New York Times published a critical article describing how the Islamic State, is recruiting young men, threatening enemies, and promoting its claim to have established a caliphate, a unified Muslim state run according to Sharia by a Muslim caliph. According to Shane and Hubbard, the Islamic state's media examinations reveal surprising findings of ISIS propaganda such as the reduced number of calls for attacks on the west, yet there have been videos showing the beheading of Americans, for example, the beheading of the American journalist James Foley 11. ISIS accomplishes this by the use of seemingly less-lethal weapons such as multilingual Twitter messages and state-of-the-art videos.
The terrorist organization after being under strong surveillance and quenched, adapted the "Lone Wolf" strategy - Lone-wolf terrorism 12 - defined as a violent act or threat of violence, with a religious, political, economic, or social objective, without organizational support, and without being involved (organizationally) by ISIS. It has been regarded as a severe threat to public safety in recent years. Moreover, the phenomenon appears to be increasing at an alarming rate, especially after capitalizing on online communication platforms by ISIS.13 Also, the Islamic State issued a Guideline booklet “Safety and Security Guideline for Lone Wolf Mujahideen and Small Cells.”14 The book is based on a series of lectures presented by Abdullah al-Adam. In its introduction, it is mentioned that this work was initially issued to the Mujahideen groups and not to individuals but later was adjusted to suit individual jihadist lone wolves and small cells. In this regard, there is a helpful study of Awan’s that examines the ISIS Propaganda published by the Islamic State (such as the "Dabiq" magazine). Examining Dabiq magazine will further help in examining to what extent ISIS utilizes the Quran to bolster its religious legitimacy.15
Based on Frissen's study, we can examine the taxonomy of Koranic references in ISIS's Dabiq (ISIS-inspired Magazine). 16 The book "Islamic State: the digital caliphate" 17will be used to elaborate on how ISIS cuts, pastes, and specifically merge parts of Koranic chapters to support its Salafi jihadist ideology.
In a similar vein, Atwan’s analysis of literature and internet sources demonstrated the terrorist organization in which “most of the digital caliphate’s business is conducted online, from recruitment and propaganda to battlefield strategy and instruction” (p. 15).18 Also, a study by Imran Awan used is utilizing qualitative data gathering techniques embedded within the grounded theory to study comments and posts concerning ISIS and the role of the Islamic State on Facebook and Twitter accounts, the study19 found that there was a strong online reaction against ISIS and that there was also an infusing sense of online propaganda and an extremist narrative that disclosed in some cases glorification of the role of ISIS. Finally, a study by Dominika and Dimitrios Stergiou explored the shifting of terrorism to cyber terrorism as an upgrade in cyber-terrorism activities. This study demonstrated the application of ISIS cyber-terror strategy20.
Even though ISIS is defeated in Syria and Iraq, the threat is still looming, not confined in Europe or the USA, but as a worldwide threat since it is a decentralized operation. We saw some operations in several countries, and the recent bloody one is in Sri Lanka, the operations which are conducted by Lone Wolf strategy, that is manifesting a real threat of new face of terrorism21. The adoption of this strategy by ISIS is clearly manifested in a recorded audio message22, when the spokesman of ISIS Abu Muhammad al-Adnani asked the sympathizers and supporters with the organization to carry out killing operations against nationals of coalition countries (Recent coalition against the Islamic state) anywhere and by any means available. Urging more attacks on Western interests everywhere, saying that "targeting so-called civilians is the most favorite and the most beneficial, "there is no immaculacy on bloodshed and no innocent people, and if you do not find a weapon, trample them with your own cars." The phenomena of Lone Wolf terrorists are a complicated one; they are individuals with no organizational affiliation and no sources to receive instructions and assignments, they carry out terrorist acts depending on their potential, influenced by extremist movements or based on ideological, religious, or political convictions.
Three criteria should be included in Lone wolf terrorist act: the act should be done individually, even if the Lone wolf does not belong to a terrorist organization and the process should be planned without the involvement of any external elements or organizational leaders. Lone wolves are carrying out individual operations against a community. Unlike traditional terrorists, Lone wolves often combine personal vendetta with religious or collective political grievances. Together, they constitute a powerful impetus to challenge the desired target.
Some of the operation’s forms that can be done by the Lone wolves are: planting self-made bombs in different locations and detonating them remotely or conduct an individual attack with a weapon that can be manufactured at home or legally purchased in the countries that permit its sale (like the USA) or driving a car or a truck and trampling pedestrians or use bladed weapons. All of these are planned, self-financed, and strictly confidential acts of Lone wolf terrorists.
In the study by Danzell & Maisonet Montañez, (2016), “Understanding the Lone wolf terrorism phenomena: assessing current profiles"23, it is disclosed that Lone wolf attacks are on the rise in the United States and many Western European democracies (such as the United Kingdom and Germany) which witnessed 198 terrorist attacks carried out by Lone wolves from 1970 to 2000. It was also pointed out that the attacks in the United States have increased by 45% and that it is the most targeted country in the period from 1990 to 2013, with 46 operations, accounting for 63% of total operations worldwide. The reason for this focus is that the nature of society allows the presence of Lone wolves where weapons can be sold and bought by civilians in stores.
The Islamic jihadist groups adoption of the Lone wolf strategies relies on the idea of decentralization so that the organization becomes truly cross-border in 2014, it was adopted when Abu Muhammad al-Adnani, a spokesman for the ISIS organization, in his voice recording, asked the sympathizers and supporters of the organization to kill nationals of coalition countries anywhere and by any means available — urging more attacks on Western interests. Security experts believe that people who act individually represent a greater risk than known organizations such as al-Qaeda or Daesh and its affiliates. The role of the Internet as a driving force in terrorist attacks was dramatically brought to light by the brothers Tsarnaev who represent an actual case of Lone wolves’ recruitment. They planted bombs at the Boston marathon in April 2013. They proclaimed online instructions on how to build the pressure cooker bombs used in the Boston bombing24. Another evident case illustrating the strategy is the case of Roshonara Choudry, a female university student who was the first and only British woman who was convicted for a violent Islamic attack. She stabbed a member of the British Parliament in November 2010 in the United Kingdom25. Investigations disclosed that both the brothers Tsarnaev and Choudry were radicalized by online content which inspired them to conduct acts of terrorism. Because of the viewed websites and audio-visual sermons of radical preachers, they were victims of internet indoctrination without ISIS playing a direct role in supporting them. The above being some of the examples of recruiting strategies, there is an urgent need to examine the Lone wolf strategy as well as other strategies used in the internet recruitment of young people to ISIS.
In conclusion, and in short, this paper concludes that there is a cohere connection between Islamic State narratives, online radicalization processes, and its connection to the Lone Wolves’ strategy 26.