2 Factor Authentication - Is It Enough?

Even if you're new to the crypto-sphere, you're probably familiar with 2 Factor Authentication (2FA) offered on various platforms, including crypto-currency exchanges, used to help identify account owners. After your password, 2FA provides an additional layer of protection to verify if you are indeed who you say you are. On crypto-exchanges, 2FA is commonly required to initiated any transactions relating to your assets. This gives users a greater sense of security and confidence in managing their accounts.
But is this a false sense of security?
Before answering the question, let's first define 2FA .
2 Factor Authentication
Many of the world's most popular websites already use some form of 2FA security, however, it may go by another name. Twitter (login verification), Facebook (login approvals) and Google (2-step verification). Regardless of what it's called, 2FA is an accessible way to strengthen account security without having to get too technical.
According to the Electronic Frontier Foundation (EFF), 2FA comes in several forms:
A one-time verification code sent to you via SMS text message
A time-based one-time password (TOTP) generated by a dedicated app, like Google Authenticator and Authy
A download-able, print-able, hard-copy backup code
A hardware token, like a Yubikey
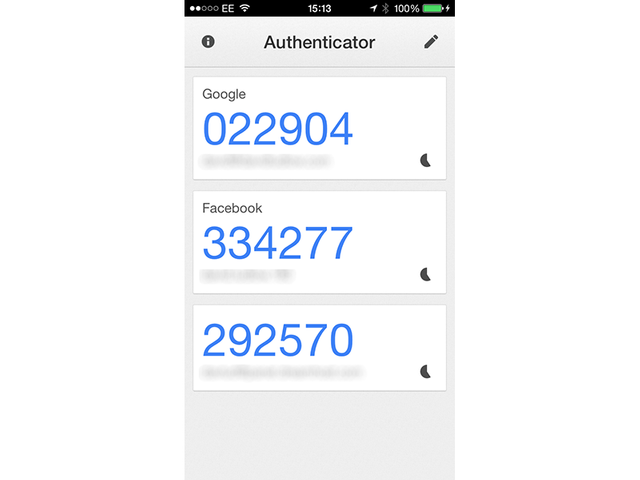
Google Authenticator is widely used throughout the internet providing users quick and easy 2FA services. Bittrex, Changelly and Coinbase are just a few examples of crypto-exchanges that provide users with the option to enable Google Authenticator 2FA.
While the EFF certainly advocates for the use of 2FA (in combination with a strong password), it also cautions that 2FA is not infallible and can be vulnerable to attack. For example, when receiving 2FA in SNS form it is possible that the texts, and the codes they contain, can be intercepted by telecom and by third parties.
Crypto Wallets
In a recent article titled Here's How Hackers can Hijack Your Online Bitcoin Wallet, the Hacker News reports that a long suspected 'critical issue' regarding Signal System 7 (SS7) may allow hackers to eavesdrop on phone conversations and intercept and view text messages which could be exploited on a large scale even with high level encryption on cellular networks.
Despite fixes being available for years, the global cellular networks have consistently been ignoring this serious issue, saying that the exploitation of the SS7 weaknesses requires significant technical and financial investment, so is a very low risk for people.
However, earlier this year we saw a real-world attacks, hackers utilised this designing flaw in SS7 to drain victims' bank accounts by intercepting two-factor authentication code (one-time passcode, or OTP) sent by banks to their customers and redirecting it to themselves.
In addition to demonstrating the vulnerability of the telecom networks, white hat hackers also demonstrated how the SS7 exploit could be used to take control over online bitcoin wallets and drain them of their assets.

While demonstrating the attack, the Positive [white hat] researchers first obtained Gmail address and phone number of the target, and then initiated a password reset request for the account, which involved sending a one-time authorization token to be sent to the target's phone number.
Just like in previous SS7 hacks, the Positive [white hat] researchers were able to intercept the SMS messages containing the 2FA code by exploiting known designing flaws in SS7 and gain access to the Gmail inbox.
From there, the researchers went straight to the Coinbase account that was registered with the compromised Gmail account and initiated another password reset, this time, for the victim's Coinbase wallet. They then logged into the wallet and emptied it of crypto-cash.
Thankfully, these hacks were not executed by cyber-criminals but by white hat hackers who wanted to demonstrate the vulnerability of SS7 and 2FA, especially to raise awareness for crypto-currency investors and enthusiasts.
Aside form the SS7 issue, there are further weaknesses related to phones in general. Phone numbers are a weak point if a cyber-criminal obtains your number along with a few personal details.
All an attacker has to do is call your cell phone company’s customer service department and pretend to be you.
...
These are the kinds of details — for example, credit card number, last four digits of an SSN, and others — that regularly leak in big databases and are used for identity theft. The attacker can try to get your phone number moved to their phone.
A hacker can than disable 2FA or simply have the 2FA authenticator code sent to their phone via SMS or voice calls.
Similarly, 'account recovery' remains a difficult conundrum as websites/accounts desire to maintain customer satisfaction and do not wish to have customers locked out of their accounts. If said hacker knows enough about you and your habits it is possible for them to gain access to your accounts through 'account recovery', providing they have enough personal information. New passwords can be generated and sent by email, ultimately bypassing 2FA.
Solutions
In light of the fact that 2FA could potentially be bypassed by exploiting the critical issues with SS7, there's not much that can be done to completely eliminate the threat at the individual level as the telecom industry needs to address these vulnerabilities in their networks. Unfortunately, it seems unlikely that that will happen as it would require a significant financial coordinated effort and financial burden to the network providers.
Last year, the researchers from Positive Technologies also gave demonstrations on the WhatsApp, Telegram, and Facebook hacks using the same designing flaws in SS7 to bypass two-factor authentication used by those services.
As a precaution suggested by The Hacker News:
Avoid using two-factor authentication via SMS texts for receiving OTP codes. Instead, rely on cryptographically-based security keys as a second authentication factor.
If there's a silver lining here for my fellow Steemians, it is that Steem Wallets are some of the most secure funds in the crypto landscape and STEEM and SBD do not depend on 2FA and instead require the use of permission keys.

Tip: Do not keep your private keys on your computer, store them offline where they cannot be hacked.
Tip2: Use your Posting Key to log into Steemit. This allows you to Vote, Post and Comment but does not give access to wallet transactions.
Furthermore, it seems logical that as the adoption 2FA becomes more mainstream, so too will there be an increase in attacks against the system. Some suggest that the next level of protection may come from 'biometrics', but for myself, I would prefer to put my trust in crypto-currency hardware wallets such as Trezor and Ledger Nano.
Of course, if you're accessing an exchange there is always going to be some risk involved but hopefully being aware of some of the ways in which your accounts can be compromised will allow you to make better decisions going forward.
Images:
EFF
ExpertReviews
coinbase
Steemit-@noisy
Steemit-@steemitguide


As one of "those" people who isn't really up to speed with all the latest in technology and so on, I get rather concerned when reading articles/posts such as these.
"hackers this, hackers that and so on"
Not all that long ago I was reading posts about how some hackers ripped off some people investing in a new crypto currency..... I was left speechless for days on that topic.
However, what I do like, is when people like yourself explain things in ways that "us common folk" like me can understand and more so the fact that you explain what we can and should do to protect ourselves from those out there who would gladly take what doesn't belong to them.
In short:
THANK YOU.
Very important post - thanks
thank you for this detailed blog man! It's blogs like these that I want to read! Looking forward to your future posts!
Incredibly important in all things security: you're only as secure as the weakest link in your security chain.
I could have an air-gapped network with 2FA on everything, but if I allow employees to plug in any device they'd like into a USB port, all I have to do is drop a few Rubber Duckies in the parking lot and it's over.
2FA is not any different. The second factor can be compromised just like the first.
I always thought there should be an extra factor for resetting password, like a delay period while website attempts to notify the user via all provided contact information.
the delayed withdraw process in steemit seems to do that.
Thanks for the useful data, I had no idea 2FA can be hacked that easy and used as a weak point at the seam time.
I think one of the issues is that the websites need to strike a balance between those of us who are just plain forgetful, providing fast and convenient services while also providing security. I think there are services that are multiple-authentication that go a bit further that are available as well.
Great point on the delayed withdrawal or the Steemit powerdown. At first a lot of people think this is inconvenient but soon realize that it makes your Steem Wallet much more secure in the event someone attempts to steal your funds.
True, True, 👍 in most cases, those get hacked that are not careful with their security. they must learn from crypro currency community hot to do it.
I recently read about hackers calling phone companies and getting phone numbers transfrered to hacker phones. Peoples wallets got cleaned out that way.
My only problem is ignorance of exactly what's happening in the Cryto- hacking space
Very good article, 2FA is a very strong security and should be required to all accounts. But there isnt a 100% secure system.
Thanks for sharing
Thanks for your comment. Yeah, I'm not knocking 2FA, I use it too, and it does provide more security than only having a password. A friend of mine always mentions 2FA as if it is fool proof. Just reminding people to be vigilant.
Well, as cryptocurrencies are going mainstream, and they are being used more than ever, it will be a very big race between the security and the hacking groups
Many hacking attempts and successes are not reported but my guess is that its so crazy. I joined Bittrex just a month ago but lost Bitcoins
Which means there is a huge opportunity for 'coders and programmers' to create more and more ways for us to secure our coins; the future is exciting!
Yes, indeed :)
I agree, as they gain more popularity, hacking will definitely increase. I try to add as much security to my accounts as possible but I don't know if that will be enough.
Absolutely, so it's important to all of us to stay on top of security issues. Thanks
Yes, it is. And the only way to do that, in my opinion, is to keep reading and learning everyday. :)
Thanks for sharing this information @v4vapid and in terms of logging in I'm going to be sure to use my posting key in the future! The conspirasist within me wonders whether the hackers are in effect exploiting a deliberate flaw in the system? Indeed an impending legal requirement in the UK is for all technology to have a backdoor. In all honesty I don't know and I could be wrong, but it's a thought.
Certainly mandatory backdoors places everyone at a higher risk of having our accounts exploited and/or privacy invaded. You could make a case for the purpose of backdoors serving other purposes than 'keeping us safe', I'm sure of it.
Yes, I can't stress this enough. Use your Posting Key as much as possible!
Good relief to know that Steemit wallet is so secure! :) I didn't know the difference between the two types of password verification vs. Posting Key. Yay for all of your awesome knowledge you keep providing me.
It's definitely a good habit to get into to use your Posting Key here on Steemit, that way if someone does obtain your key somehow, the worst they can do is make votes for you!
I guess they could also make some bad comments but they Do Not have access to your wallet.
ahhh... yes I was like... what are all of these passwords for! So just to clarify, I should be able to use the Posting key as my password to get into my account as well?
Yes @karensuestudios, you can log into your account using your Private Posting Key. I always use the postings key, you can also claim rewards from your wallet but if you attempt to make any transactions, you will be asked to provide your Active Private Key. This is a good way to increase security for your steemit account. I also don't store my keys on my computer.
There are some good posts about permission keys. I'll ass a link here once i find the one i had in mind.
Last day I came across an article explaining how to send an encrypted memo here on steemit. You just have to put a '#' at the very beginning of your memo. It seemed to work for everyone except me. I got an error. It turned out that it was because I was logged with my posting key only instead of my master/owner key.
I was very surprised because this meant that everybody was using their master/owner key to log in maybe without even knowing it.